EP 40: Git workflow
This week’s system design refresher:
CAP Theorem (Youtube video)
How Git works
Redis use cases
Linux commands
What 50,000 incidents reveal about the state of incident management (Sponsored)
Jump into the industry’s first Incident Benchmark Report and uncover the patterns and trends that can help you level up how you manage and learn from incidents at your organization.
Discover insights that will give you a blueprint for evaluating your incident management program, like:
- What behaviors make a notable difference in MTTR,
- What days and times incidents most often occur,
- How long the average response effort takes by severity level,
- The best responder team size, and more.
What is the CAP theorem? How useful is it to system design?
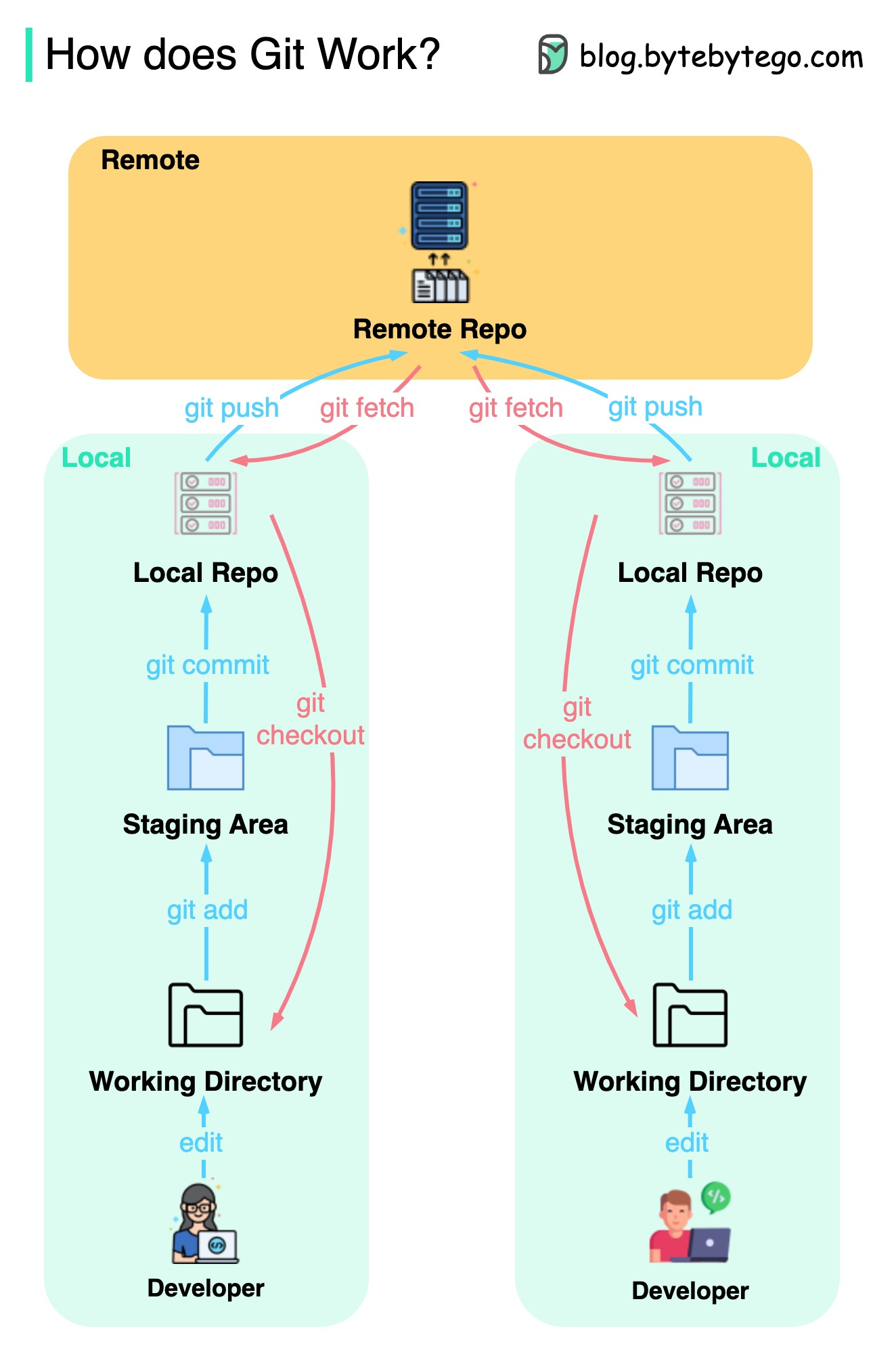
How does Git Work?
The diagram below shows the Git workflow.
Git is a distributed version control system. Every developer maintains a local copy of the main repository and edits and commits to the local copy. The commit is very fast because the operation doesn’t interact with the remote repository. If the remote repository crashes, the files can be recovered from the local repositories.
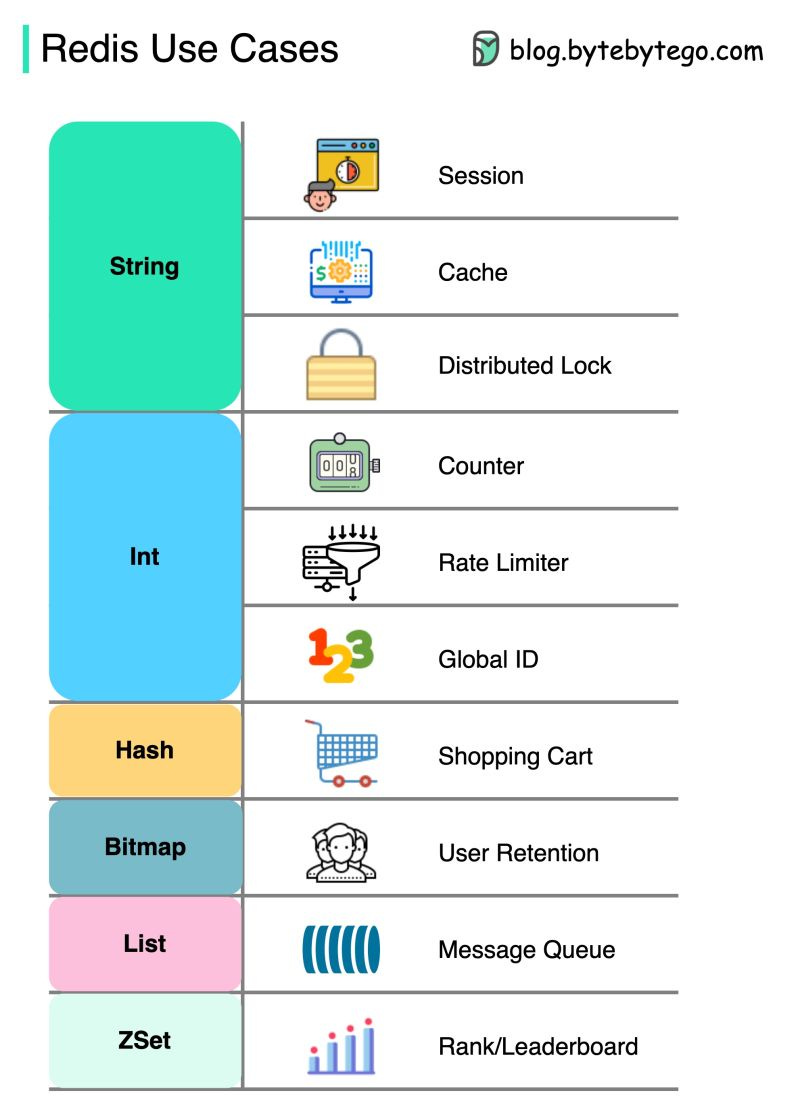
How can Redis be used?
There is more to Redis than just caching.
.
Redis can be used in a variety of scenarios as shown in the diagram.
Session
We can use Redis to share user session data among different services.Cache
We can use Redis to cache objects or pages, especially for hotspot data.Distributed lock
We can use a Redis string to acquire locks among distributed services.Counter
We can count how many likes or how many reads for articles.Rate limiter
We can apply a rate limiter for certain user IPs.Global ID generator
We can use Redis Int for global ID.Shopping cart
We can use Redis Hash to represent key-value pairs in a shopping cart.Calculate user retention
We can use Bitmap to represent the user login daily and calculate user retention.Message queue
We can use List for a message queue.Ranking
We can use ZSet to sort the articles.
Linux commands illustrated on one page!
Take a look at how many you know here :)
Controlling processes: kill, killall, nice
Scheduling jobs: sleep, watch, crontab
Host location: host, whois, ping, traceroute
Network connections: ssh, telnet, scp, ftp
Screen output: echo, printf, seq, clear
Viewing Processes: ps, uptime, top, free
And many more
Featured job openings
HEIR: Senior Software Engineer, Full Stack (United States)




Awsome! 🙏
Thanks for sharing this article! 👍