EP138: How do AirTags work?
WorkOS: Your app, Enterprise Ready. (Sponsored)
WorkOS is a modern identity platform for B2B SaaS.
→ A complete user management solution along with SSO, Directory Sync (SCIM), and Fine-Grained Authorization (FGA).
→ Integrate in minutes with modular and easy-to-use APIs
→ A self-serve onboarding flow that guarantees a seamless UX for your customers' IT admins when setting up SSO and SCIM.
→ Free user management up to 1 million MAUs. Comes standard with social login, MFA, RBAC, bot protection, and more.
WorkOS powers hundreds of high-growth companies including Perplexity, Vercel, and Cursor.
This week’s system design refresher:
Big-O Notation in 3 Minutes (Youtube video)
How do AirTags work?
What is a deadlock?
How Do Search Engines Work?
SPONSOR US
Big-O Notation in 3 Minutes
How do AirTags work?
AirTags work by leveraging a combination of Bluetooth technology and the vast network of Apple devices to help you locate your lost items.
Here's a breakdown of how they function:
Bluetooth Signal: Each AirTag emits a secure Bluetooth signal that can be detected by nearby Apple devices (iPhones, iPads, etc.) within the Find My network.
Find My Network: When an AirTag comes within range of an Apple device in the Find My network, that device anonymously and securely relays the AirTag's location information to iCloud.
Location Tracking: You can then use the Find My app on your own Apple device to see the approximate location of your AirTag on a map.
Limitations:
Please note that AirTags rely on Bluetooth technology and the presence of Apple devices within the Find My network. If your AirTag is in an area with few Apple devices, its location may not be updated as frequently or accurately.
🚀pgai Vectorizer - Automate embeddings for search and RAG, all within PostgreSQL (Sponsored)
Launch Alert: pgai Vectorizer automates embedding creation in PostgreSQL, keeping your embeddings up to date as your data changes—no manual syncing required. You can also test models, switch seamlessly, and manage everything with SQL. Available free on GitHub or fully managed in Timescale Cloud.
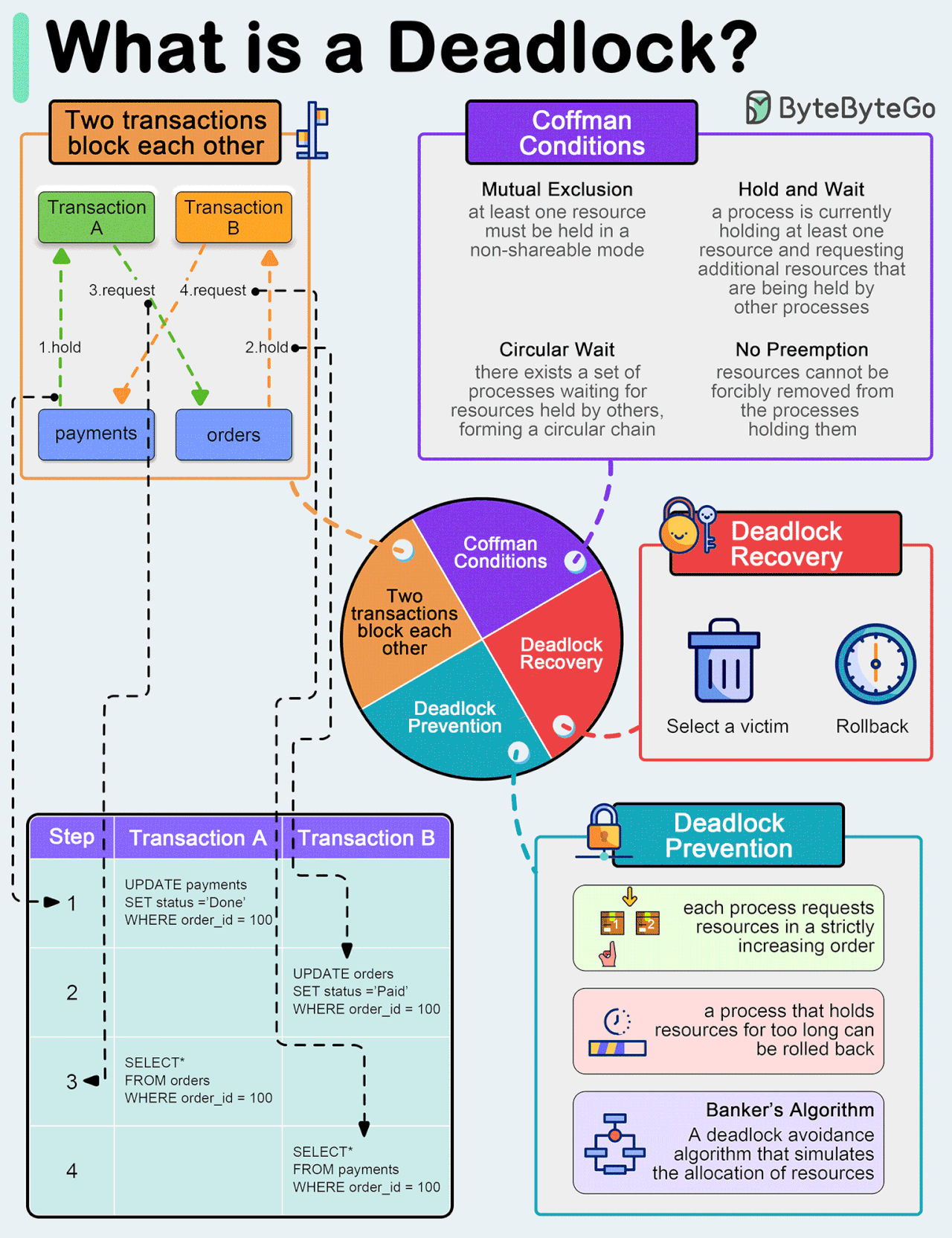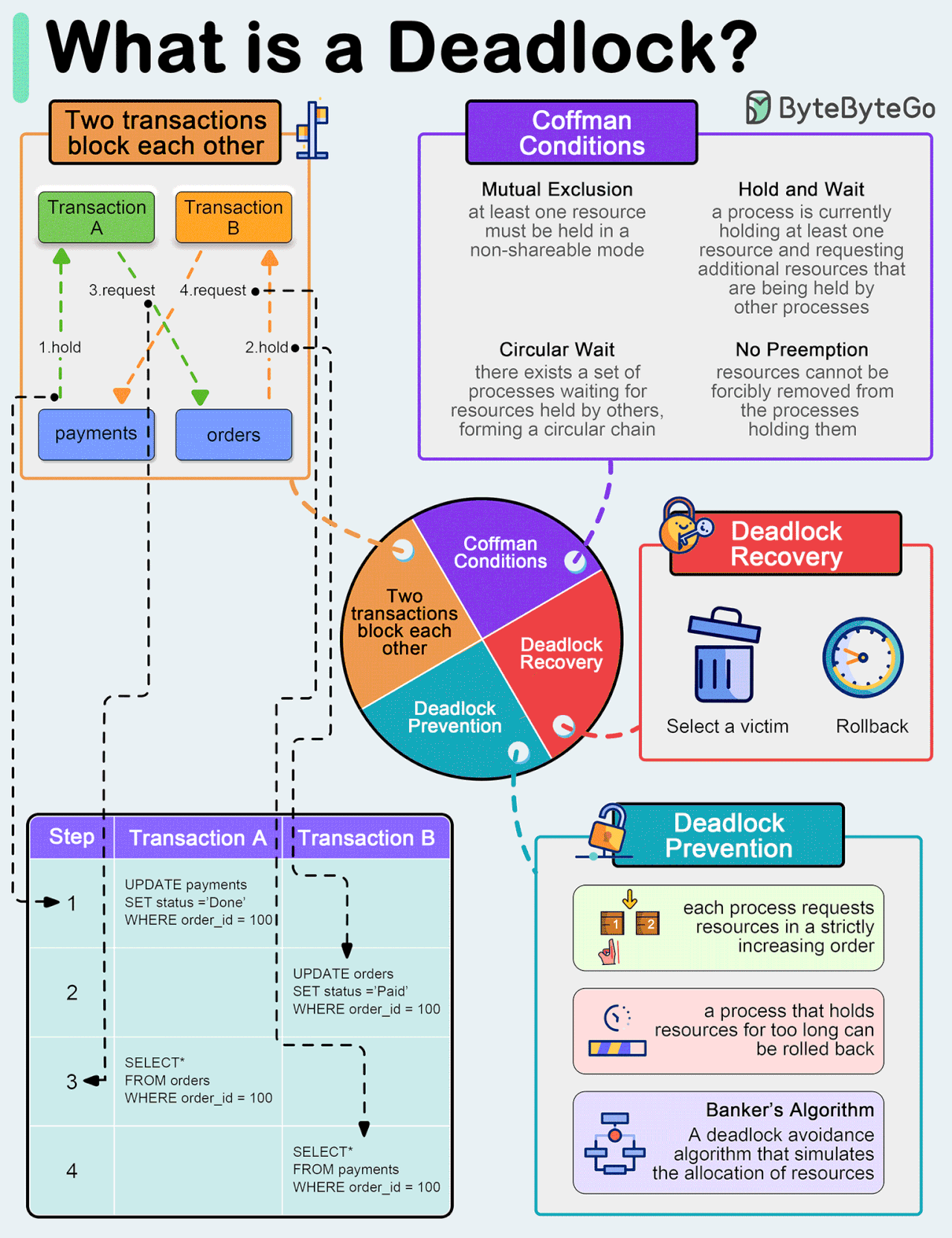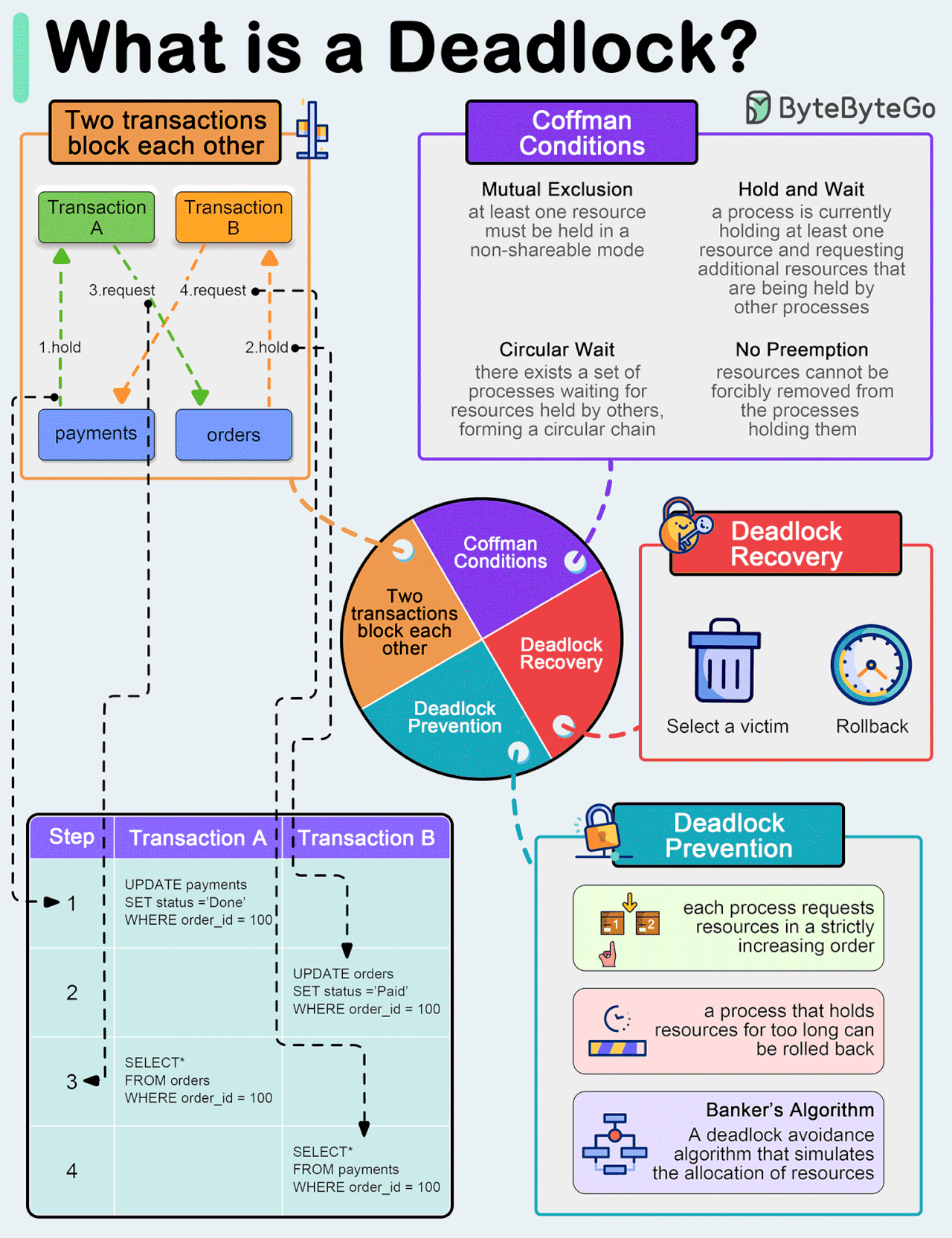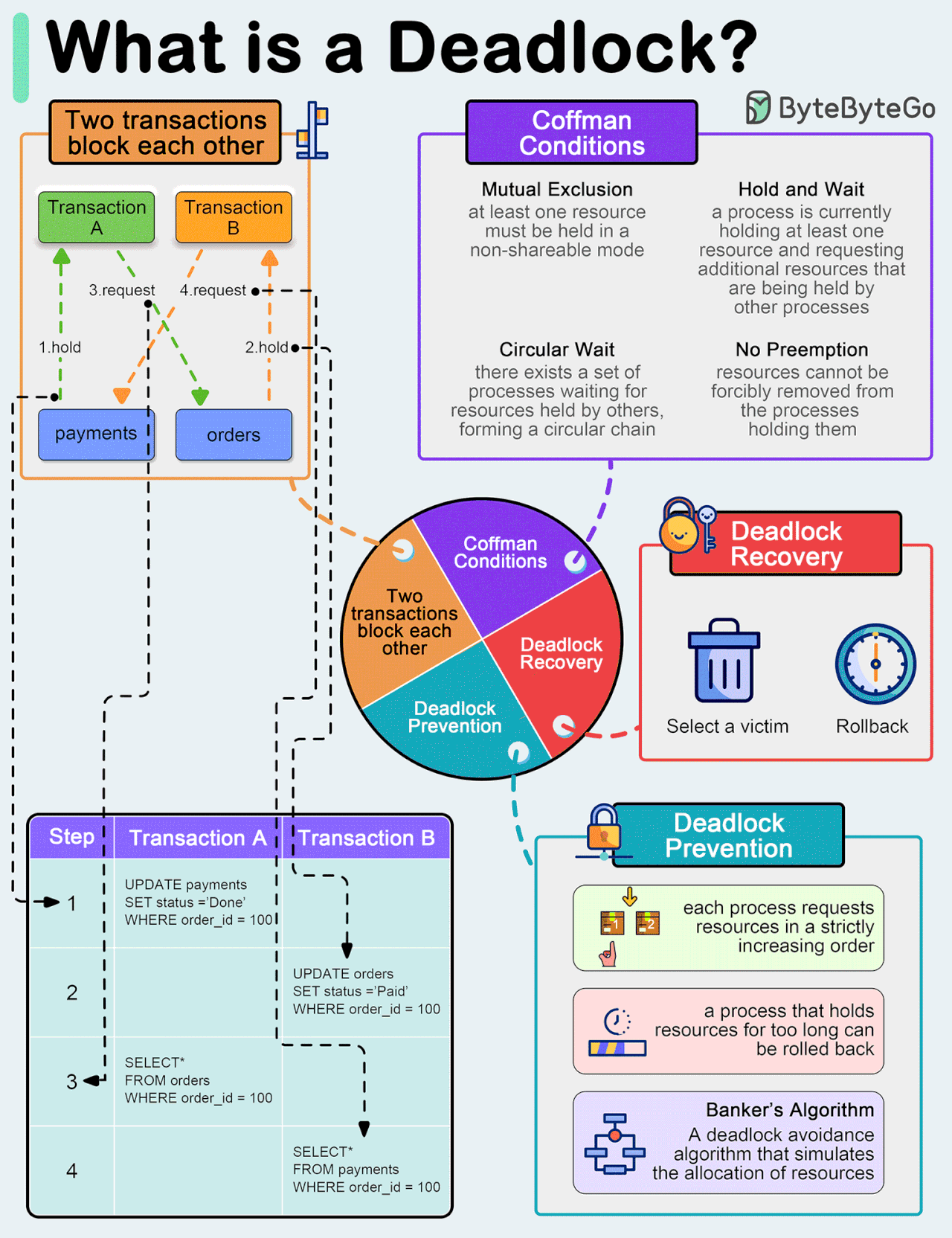
What is a deadlock?
A deadlock occurs when two or more transactions are waiting for each other to release locks on resources they need to continue processing. This results in a situation where neither transaction can proceed, and they end up waiting indefinitely.
Coffman Conditions
The Coffman conditions, named after Edward G. Coffman, Jr., who first outlined them in 1971, describe four necessary conditions that must be present simultaneously for a deadlock to occur:Mutual Exclusion
Hold and Wait
No Preemption
Circular Wait
Deadlock Prevention
Resource ordering: impose a total ordering of all resource types, and require that each process requests resources in a strictly increasing order.
Timeouts: A process that holds resources for too long can be rolled back.
Banker’s Algorithm: A deadlock avoidance algorithm that simulates the allocation of resources to processes and helps in deciding whether it is safe to grant a resource request based on the future availability of resources, thus avoiding unsafe states.
Deadlock Recovery
Selecting a victim: Most modern Database Management Systems (DBMS) and Operating Systems implement sophisticated algorithms for detecting deadlocks and selecting victims, often allowing customization of the victim selection criteria via configuration settings. The selection can be based on resource utilization, transaction priority, cost of rollback etc.
Rollback: The database may roll back the entire transaction or just enough of it to break the deadlock. Rolled-back transactions can be restarted automatically by the database management system.
Over to you: have you solved any tricky deadlock issues?
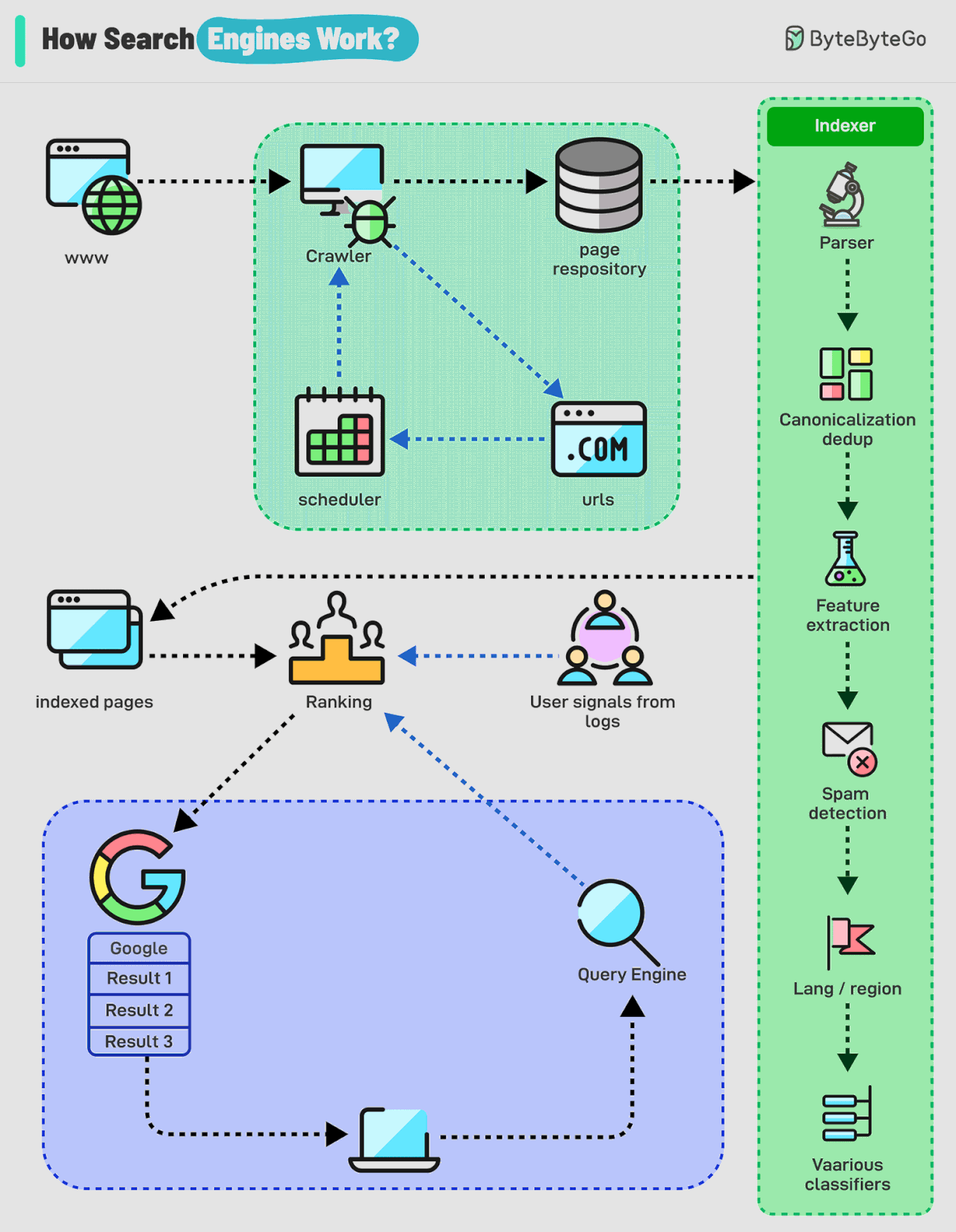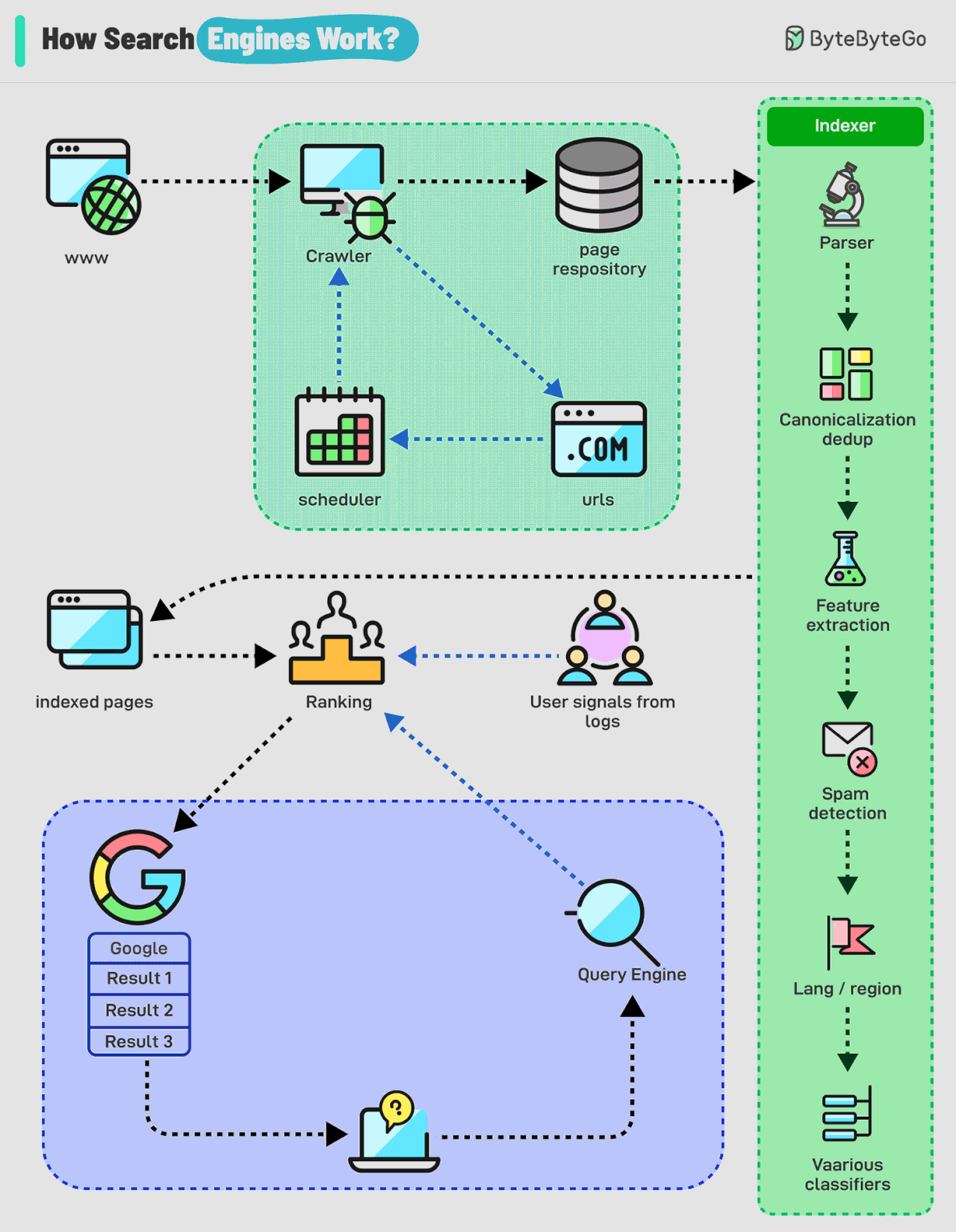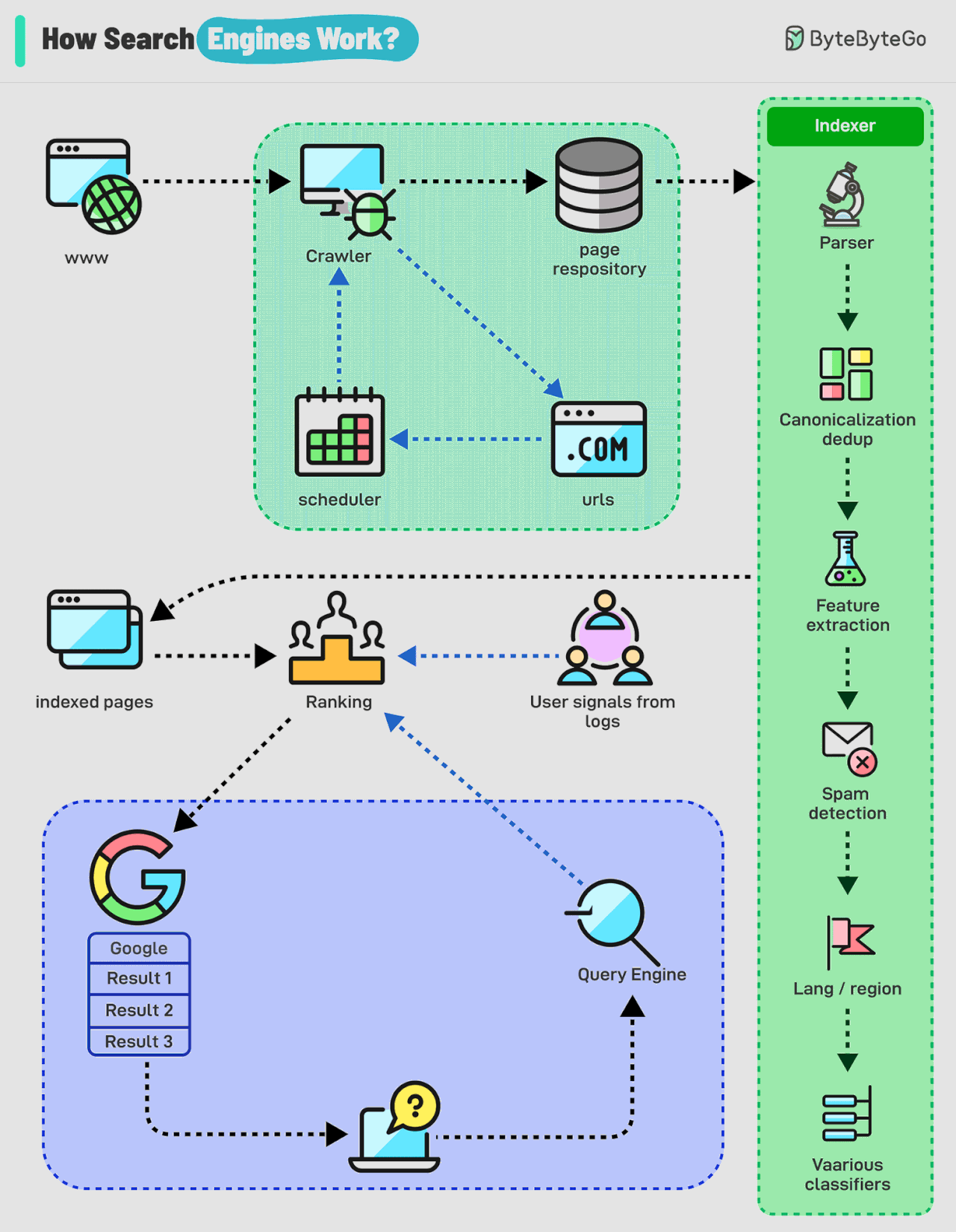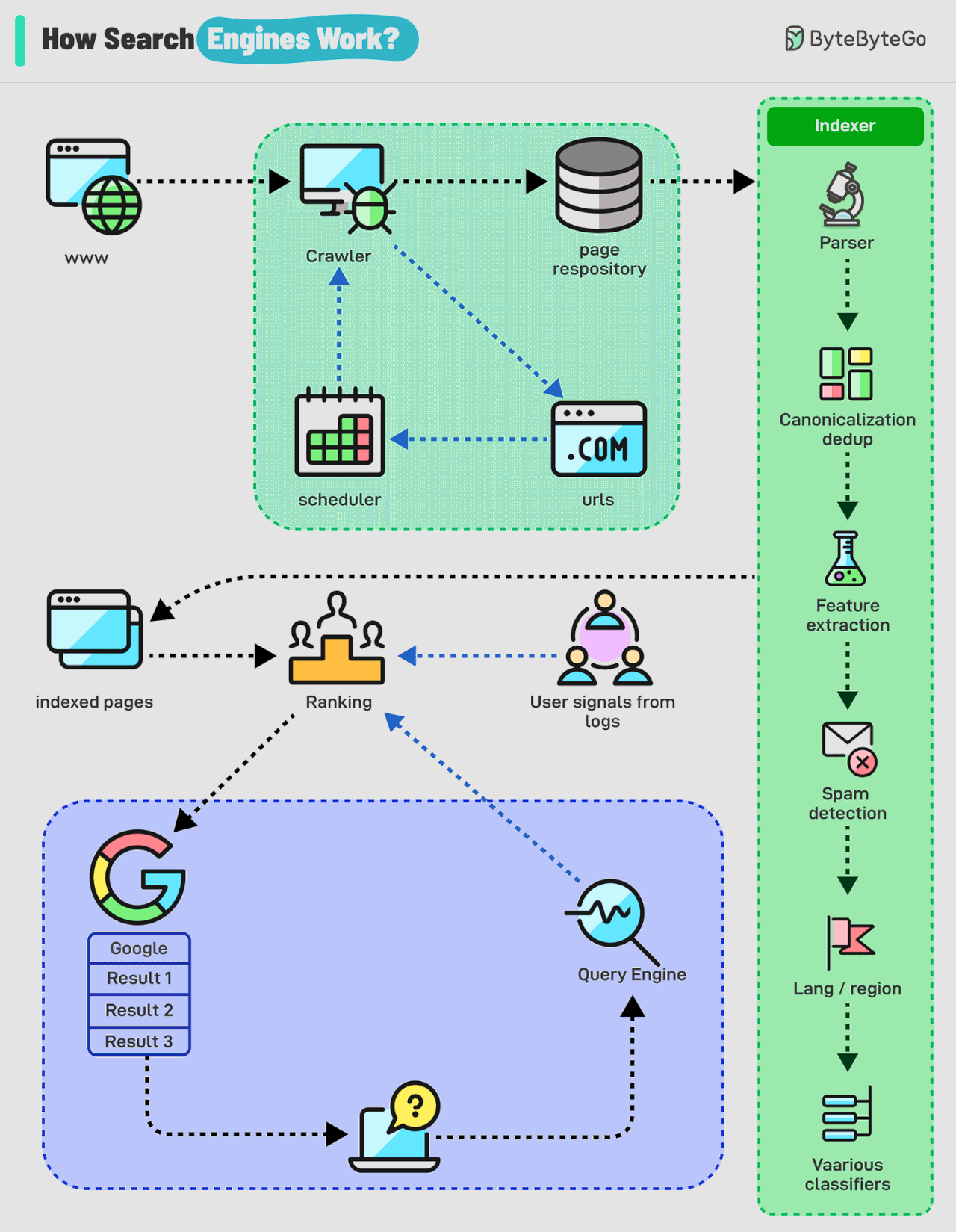
How Do Search Engines Work?
Search engines work through a combination of three core processes:
Crawling: Search engines use automated programs called "crawlers" to discover and download web pages from the internet. These crawlers start with a list of known web pages (seeds) and follow links on those pages to find new ones, creating a vast network of interconnected content.
Indexing: The information collected by the crawlers is then analyzed and organized into a massive database called an index. This process involves extracting key elements such as keywords, content type, freshness, language, and other classification signals to understand what each page is about and how relevant it might be to different search queries.
Serving search results: When a user enters a query, the search engine's algorithm sifts through the index to identify the most relevant and helpful pages. Here's a breakdown of how it works:
Query Analysis: The search engine analyzes the user's query to understand its meaning and intent. This includes identifying keywords, recognizing synonyms, and interpreting context.
Retrieval: The search engine retrieves relevant pages from its vast index based on the query analysis. This involves matching the query's keywords with the indexed content of web pages.
Ranking: The retrieved pages are then ranked based on their relevance and other factors.
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com





Hi,
I enjoy reading your articles and very interesting subject matter. I have one qn. to ask you here.
I viewed your article on "How do Search engines work?" The diagrams look great. Do you mind sharing with me what drawing or diagramming tool (s) do you use to create the diagram?
The subject matter size is enough to trigger further interests on the topic.
Thanks
GL Srinivasan
glsrini1@gmail.com