EP147: The Ultimate API Learning Roadmap
😘Kiss Manual Testing Goodbye—Ship 5x Faster (Sponsored)
Build features without the drag of multi-day QA Cycles. QA Wolf covers 80% of your web and mobile app with automated tests in just four months, then maintains and updates them 24/7.
Unlimited parallel test runs validate every change in minutes, not days.
The zero flakes guarantee cuts out false alarms and wasted engineering hours.
Salesloft saves $750k a year by running over 300 tests on each PR—a clear example of how QA Wolf transforms QA speed and efficiency.
Spend less time stressing over slow test suites and more time delivering what your customers need.
Take your releases from bottlenecked to blazing-fast!
This week’s system design refresher:
What is a LOAD BALANCER really about? (Youtube video)
The Ultimate API Learning Roadmap
30 Useful AI Apps That Can Help You in 2025
10 Essential Components of a Production Web Application
How do we design effective and safe APIs?
Code First v.s. API First
Oauth 2.0 Explained With Simple Terms
Session, Cookie, JWT, Token, SSO, and OAuth 2.0 Explained in One Diagram
SPONSOR US
What is a LOAD BALANCER really about?
The Ultimate API Learning Roadmap
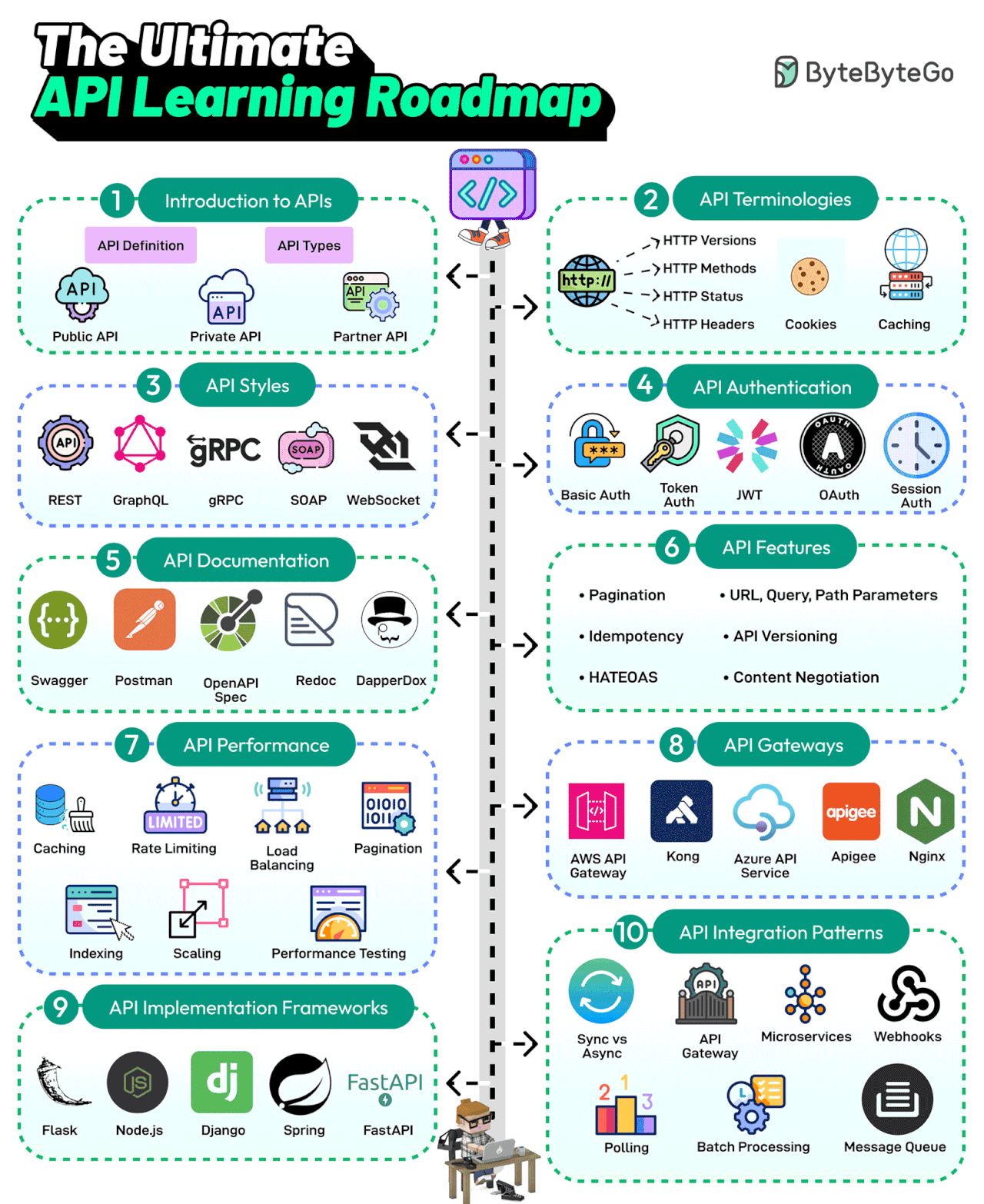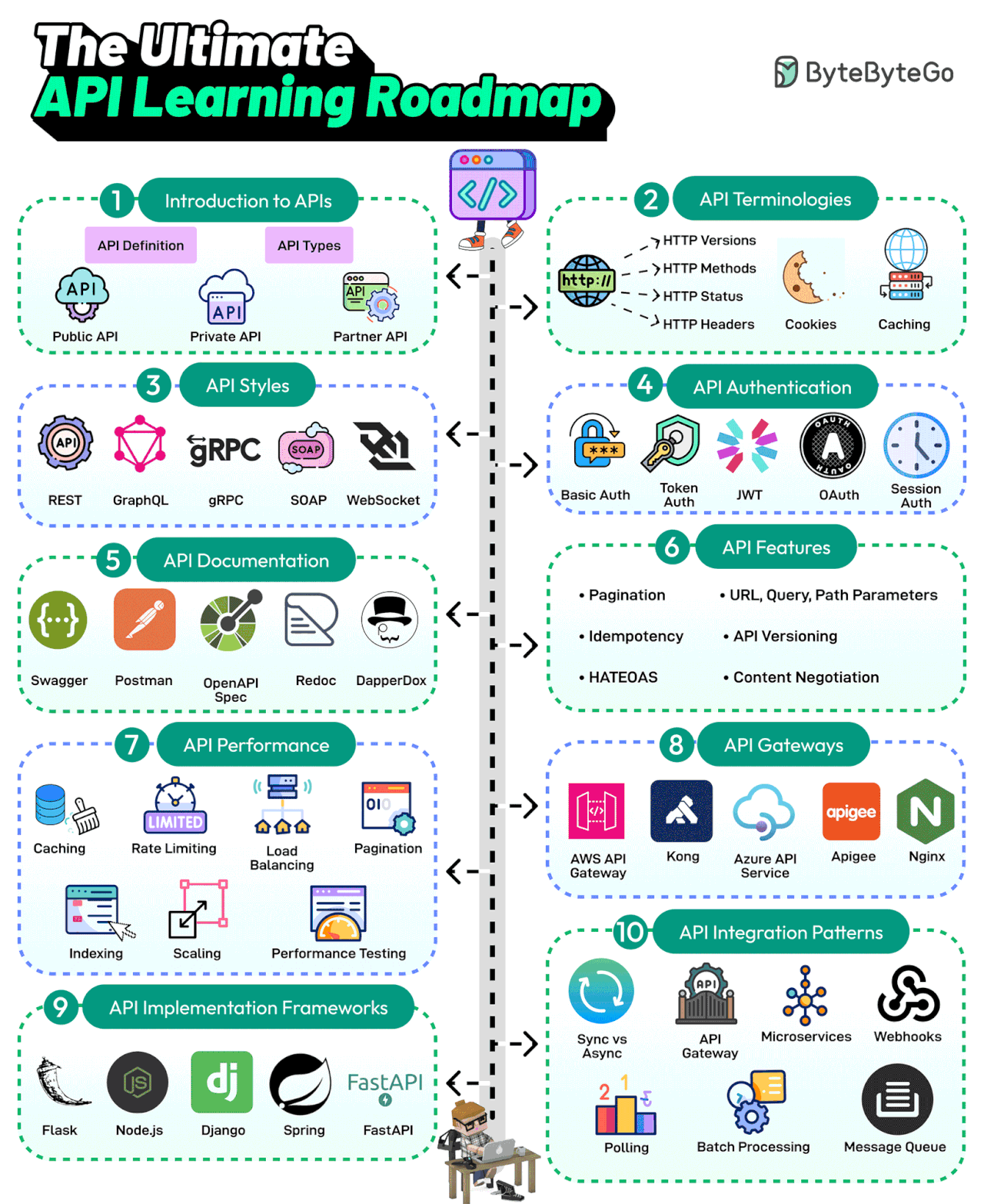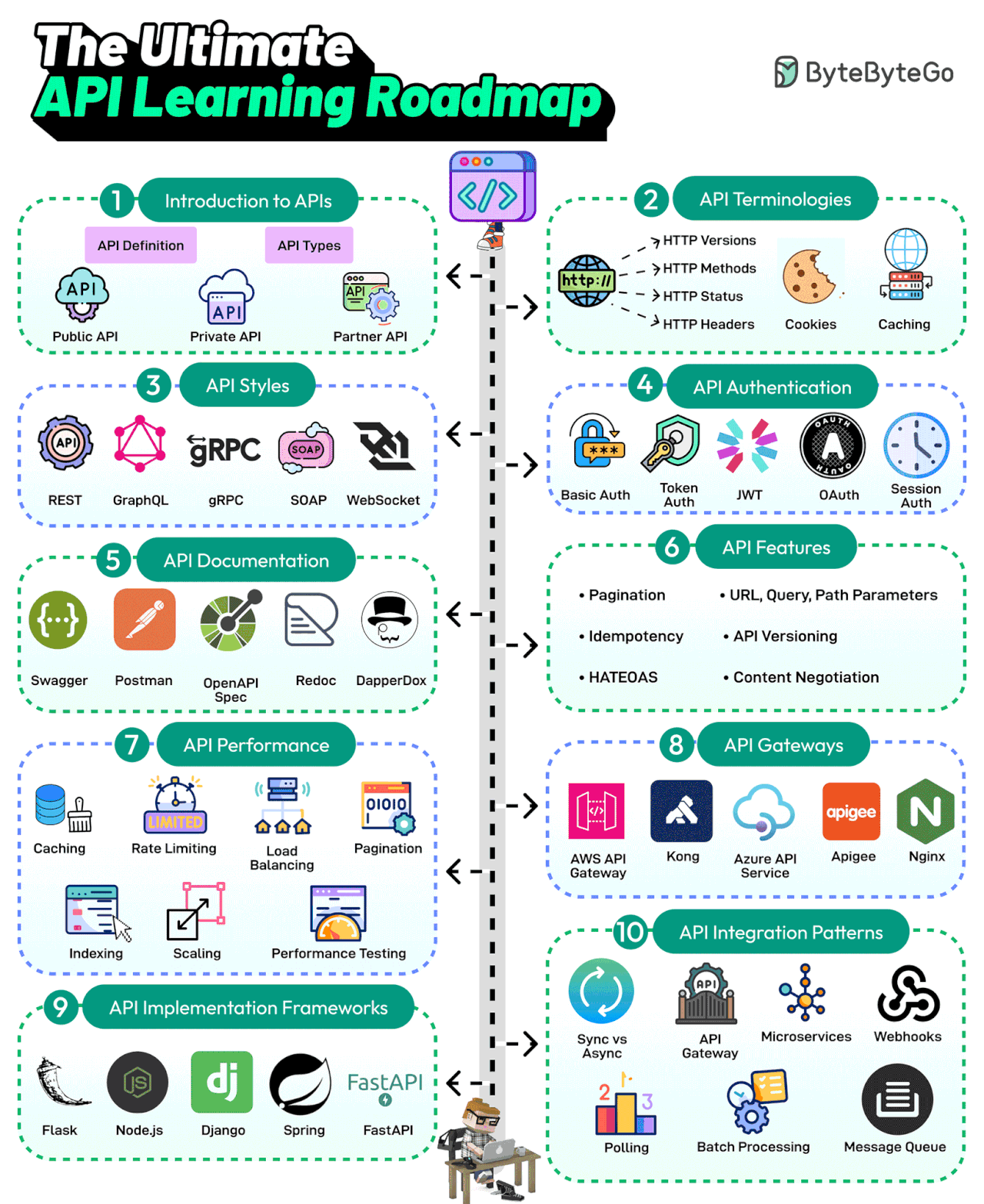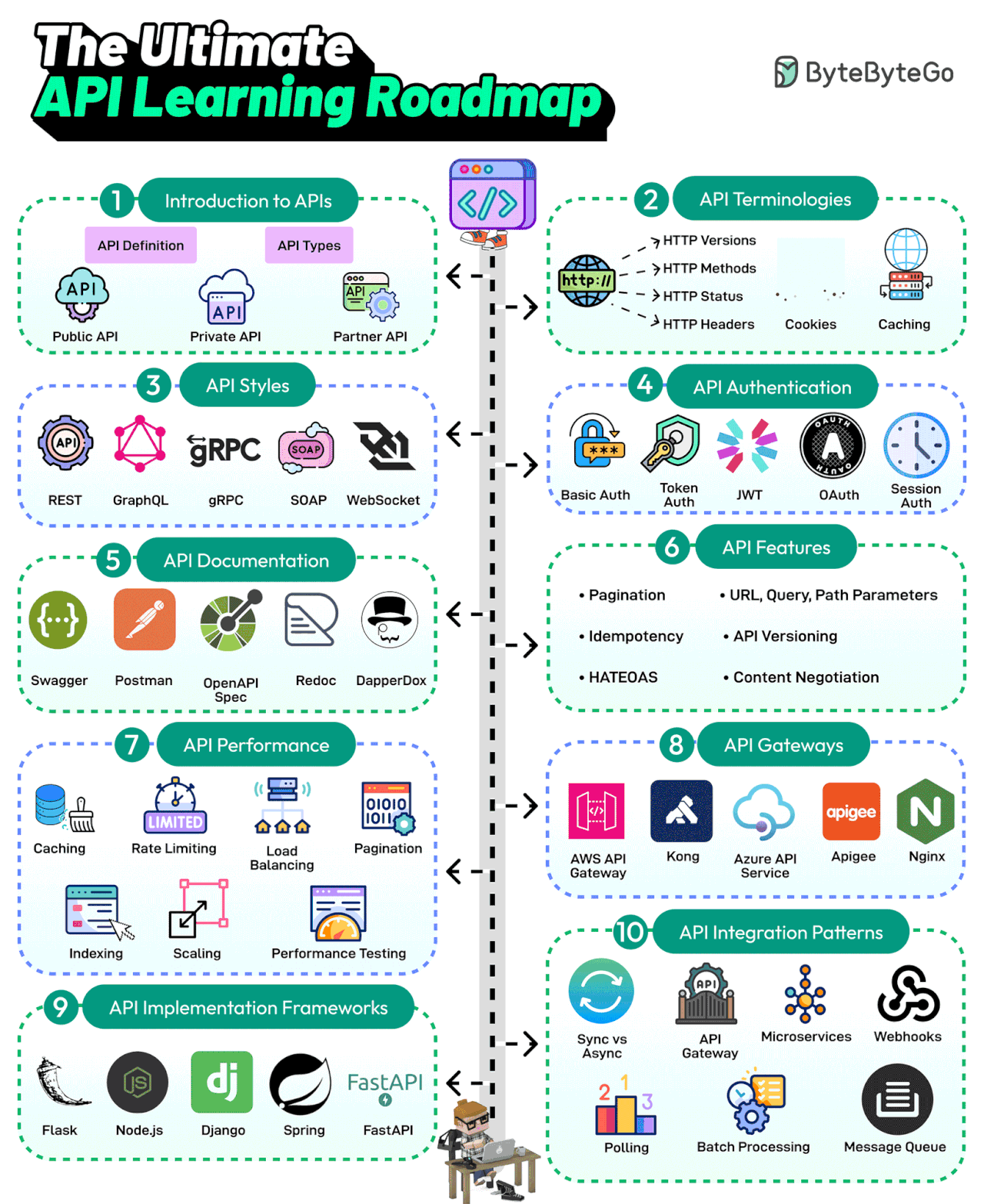
APIs are the backbone of communication over the Internet. Every developer needs to learn about APIs. Here’s a roadmap that covers the most important topics:
Introduction to APIs
API is a set of protocols and tools for building applications. Different types of APIs exist, such as public, private, and partner.API Terminologies
Various API terminologies, such as HTTP versions, cookies, and caching, need to be understood.API Styles
The most common API styles are REST, SOAP, GraphQL, gRPC, and WebSocketsAPI Authentication
API Authentication techniques like Basic Auth, Token, JWTs, OAuth, and Session AuthAPI Documentation
A good API is understandable. API Documentation tools like Swagger, Postman, Redoc, and DapperDox make it possible.API Features
Key API features include pagination, parameters, idempotency, API versioning, HATEOAS, and content negotiationAPI Performance Techniques
Common API performance techniques are caching, rate limiting, load balancing, pagination, DB indexing, scaling, and performance testing.API Gateways
Learn about API Gateways such as Amazon API Gateway, Azure API Services, Kong, Nginx, etc.API Implementation Frameworks
The most popular API development frameworks are Node.js, Spring, Flask, Django, and FastAPIAPI Integration Patterns
Learn about various API integration patterns such as gateways, event-driven, webhook, polling, and batch processing.
Over to you: What else will you add to the API learning roadmap?
Download the high resolution PDF here.
Make 2025 the year you modernize your data infrastructure (Sponsored)
The new year is here. And with it comes the perfect opportunity to set a transformative goal: future-proof your data infrastructure.
Like many, you may feel daunted by the complexities of a “lift and shift” approach to modernization.
That’s why Cockroach Labs developed The Architect’s Guide to SQL Database Modernization: Your Step-by-Step Roadmap.
Designed to help you navigate modernization at your own pace, whether running applications in the cloud, on-prem, or hybrid, this guide will help you:
Assess your current state
Learn strategies to standardize, scale, and diversify your data infrastructure
Follow a simple, proven, three-step modernization framework
30 Useful AI Apps That Can Help You in 2025
AI apps are taking over the world. There’s an AI app for every conceivable use case. Here are some AI apps for different categories:
General Purpose: Perplexity, Anthropic Claude, Grok, ChatGPT, and Gemini
Writing Code: Cursor, Replit, Windsurf AI, Github Copilot, and Tabnine
Productivity: Adobe (PDF Chat), Gemini for Gmail, Gamma (AI slide deck), WisprFlow (AI voice dictation), and Granola (AI notetaker)
Audience Building: Delphi (AI text, voice), HeyGen (video translation), Persona (AI agent builder), Captions (AI video editing), and OpusClips (Video repurposing)
Creativity: ElevenLabs (realistic AI voices), Midjourney, Suno AI (music generation), Krea (enhance images), and Photoroom (AI image editing)
Learning and Growth: Particle News App, Rosebud (AI journal app), NotebookLM, GoodInside (parenting co-pilot), and Ash (AI counselor).
Over to you: Which other AI app will you add to the list?
10 Essential Components of a Production Web Application
It all starts with CI/CD pipelines that deploy code to the server instances. Tools like Jenkins and GitHub help over here.
The user requests originate from the web browser. After DNS resolution, the requests reach the app servers.
Load balancers and reverse proxies (such as Nginx & HAProxy) distribute user requests evenly across the web application servers.
The requests can also be served by a Content Delivery Network (CDN).
The web app communicates with backend services via APIs.
The backend services interact with database servers or distributed caches to provide the data.
Resource-intensive and long-running tasks are sent to job workers using a job queue.
The full-text search service supports the search functionality. Tools like Elasticsearch and Apache Solr can help here.
Monitoring tools (such as Sentry, Grafana, and Prometheus) store logs and help analyze data to ensure everything works fine.
In case of issues, alerting services notify developers through platforms like Slack for quick resolution.
Over to you: What other components would you add to the architecture of a production web app?
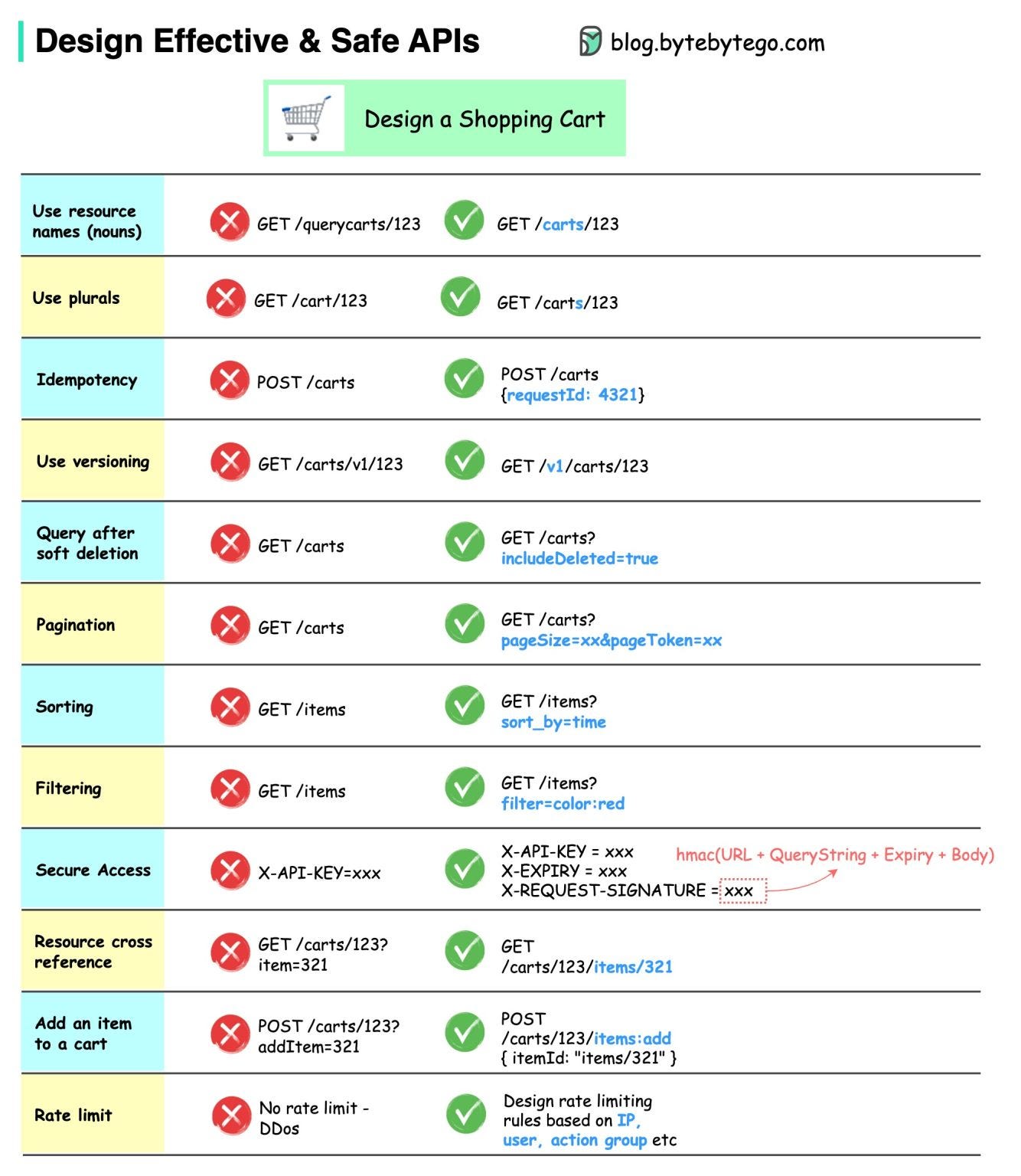
How do we design effective and safe APIs?
The diagram below shows typical API designs with a shopping cart example.
Note that API design is not just URL path design. Most of the time, we need to choose the proper resource names, identifiers, and path patterns. It is equally important to design proper HTTP header fields or to design effective rate-limiting rules within the API gateway.
Over to you: What are the most interesting APIs you’ve designed?
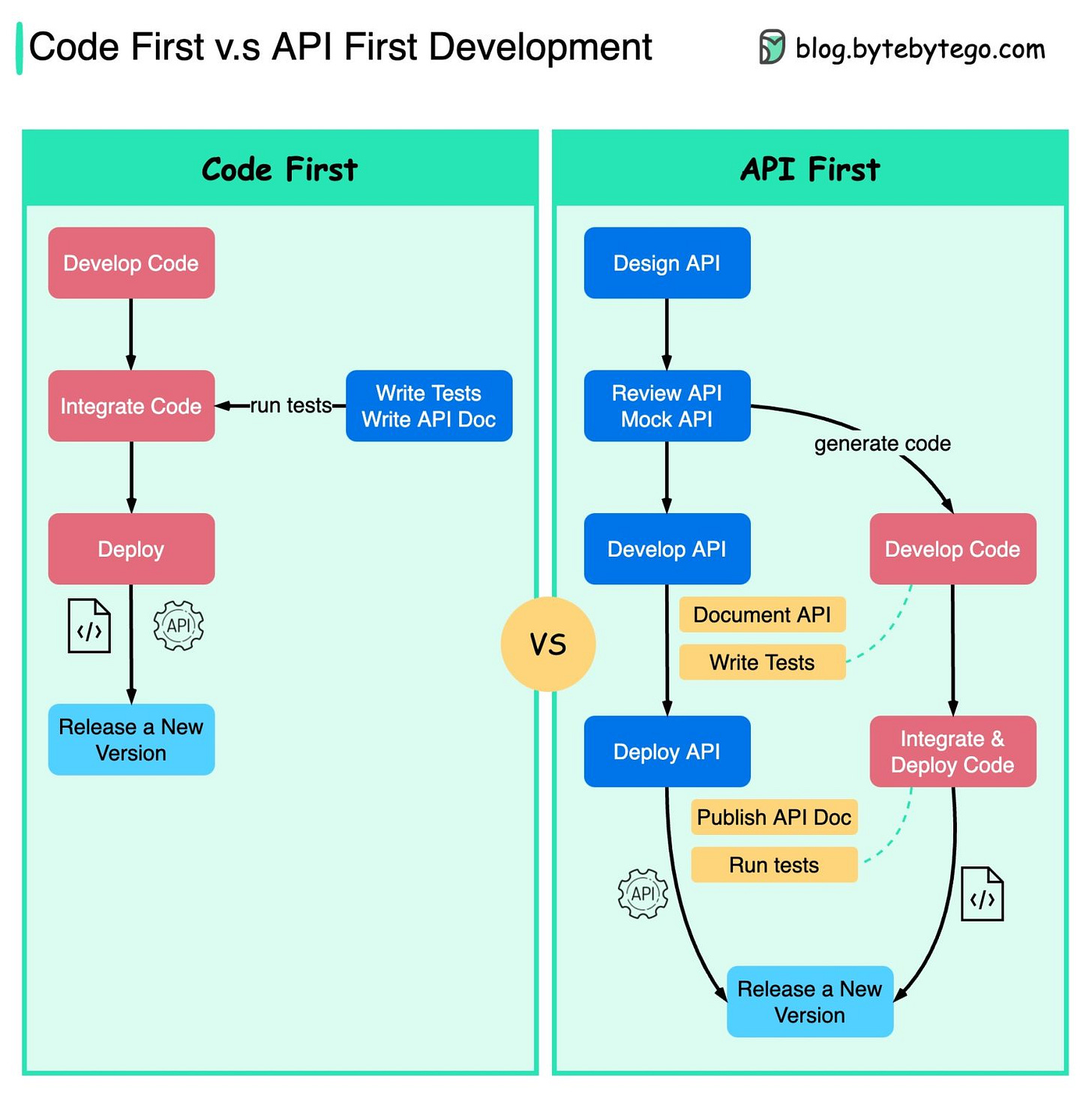
Code First v.s. API First
The diagram below shows the differences between code-first development and API-first development. Why do we want to consider API first design?
Microservices increase system complexity.
We have separate services to serve different functions of the system. While this kind of architecture facilitates decoupling and segregation of duty, we need to handle the various communications among services.Separate functional teams need to speak the same language.
The dedicated functional teams are only responsible for their own components and services. It is recommended that the organization speak the same language via API design.Improve software quality and developer productivity
Since we have ironed out most of the uncertainties when the project starts, the overall development process is smoother, and the software quality is greatly improved.
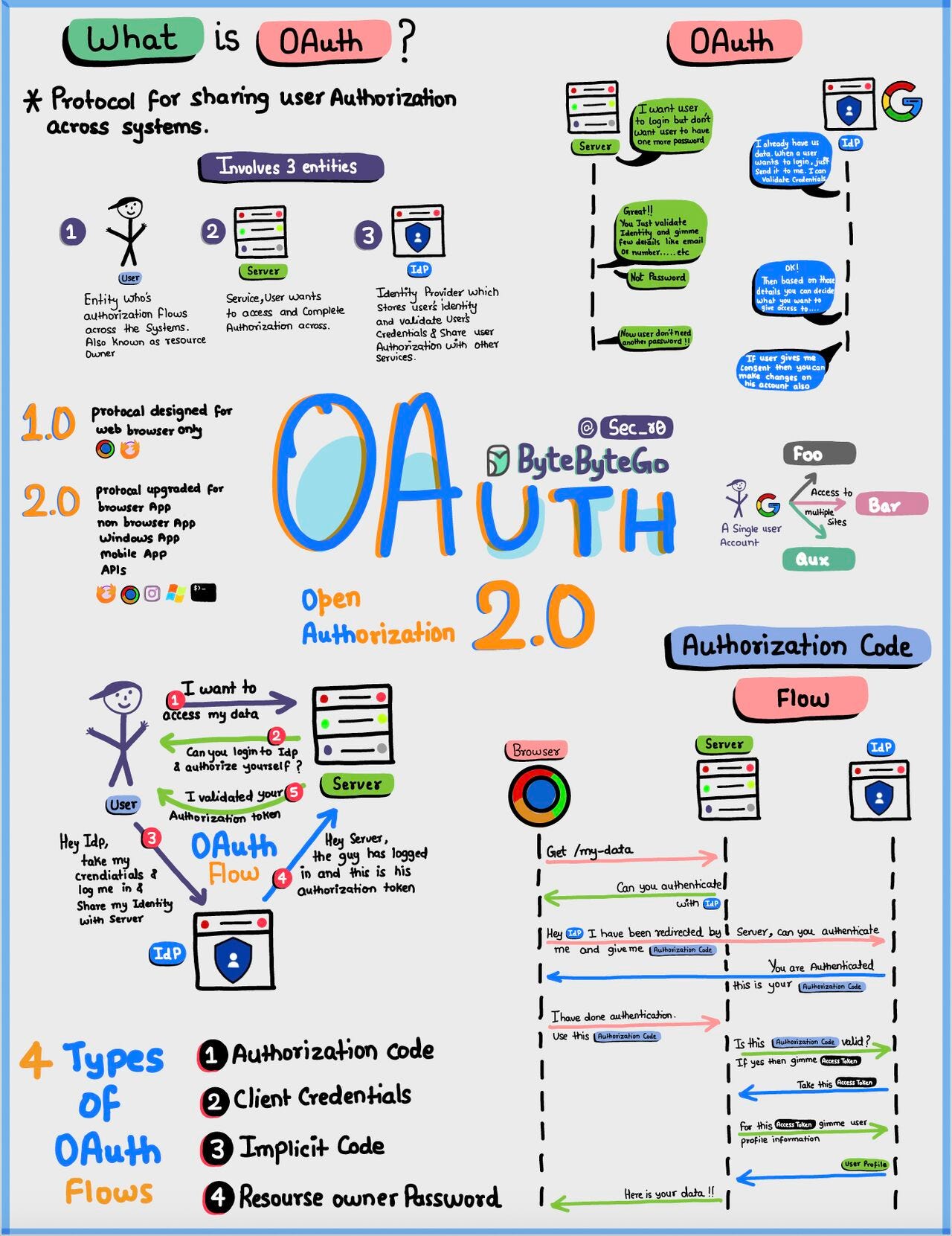
Oauth 2.0 Explained With Simple Terms
OAuth 2.0 is a powerful and secure framework that allows different applications to securely interact with each other on behalf of users without sharing sensitive credentials.
The entities involved in OAuth are the User, the Server, and the Identity Provider (IDP).
What Can an OAuth Token Do?
When you use OAuth, you get an OAuth token that represents your identity and permissions. This token can do a few important things:
Single Sign-On (SSO): With an OAuth token, you can log into multiple services or apps using just one login, making life easier and safer.
Authorization Across Systems: The OAuth token allows you to share your authorization or access rights across various systems, so you don't have to log in separately everywhere.
Accessing User Profile: Apps with an OAuth token can access certain parts of your user profile that you allow, but they won't see everything.
Remember, OAuth 2.0 is all about keeping you and your data safe while making your online experiences seamless and hassle-free across different applications and services.
Over to you: Imagine you have a magical power to grant one wish to OAuth 2.0. What would that be? Maybe your suggestions actually lead to OAuth 3.
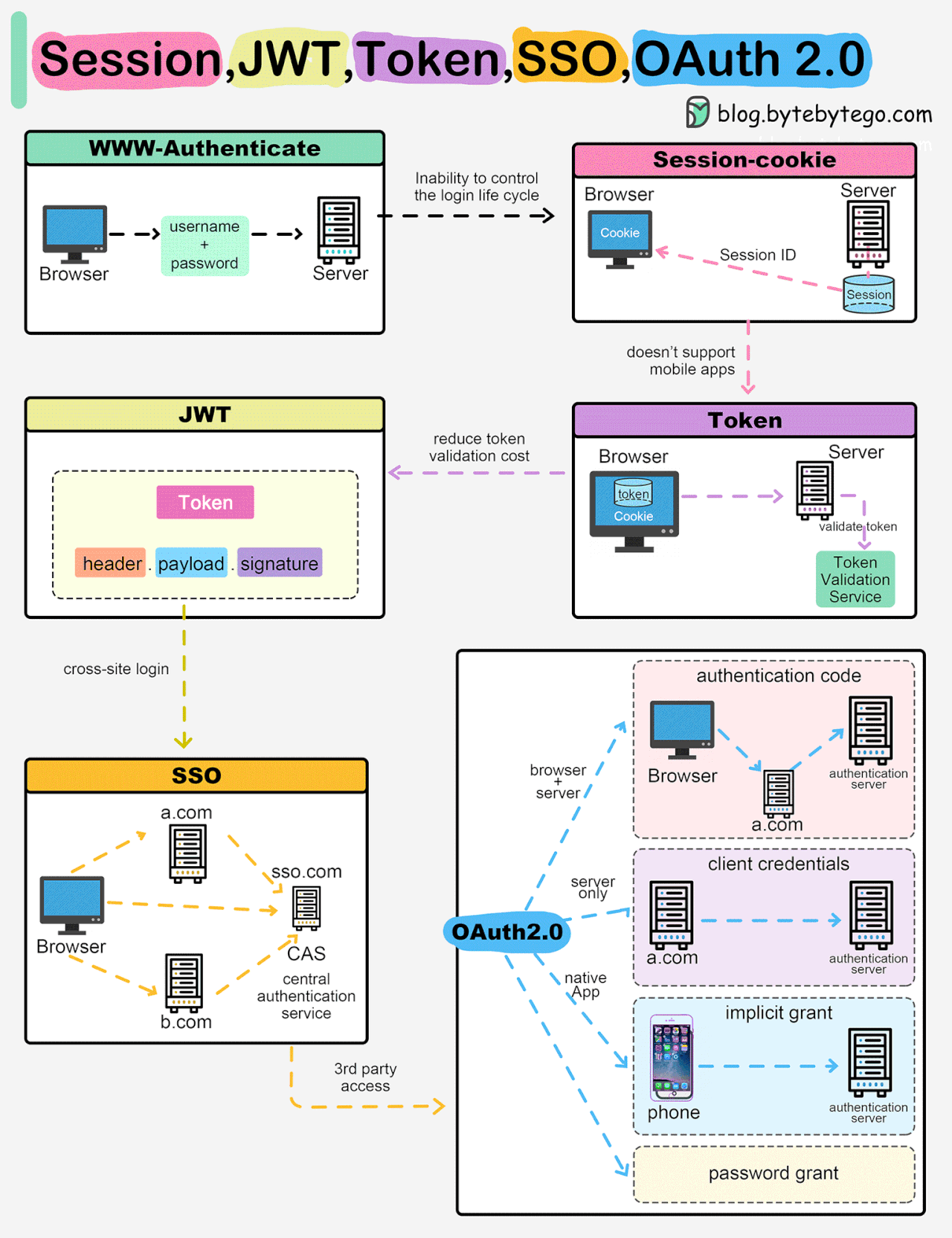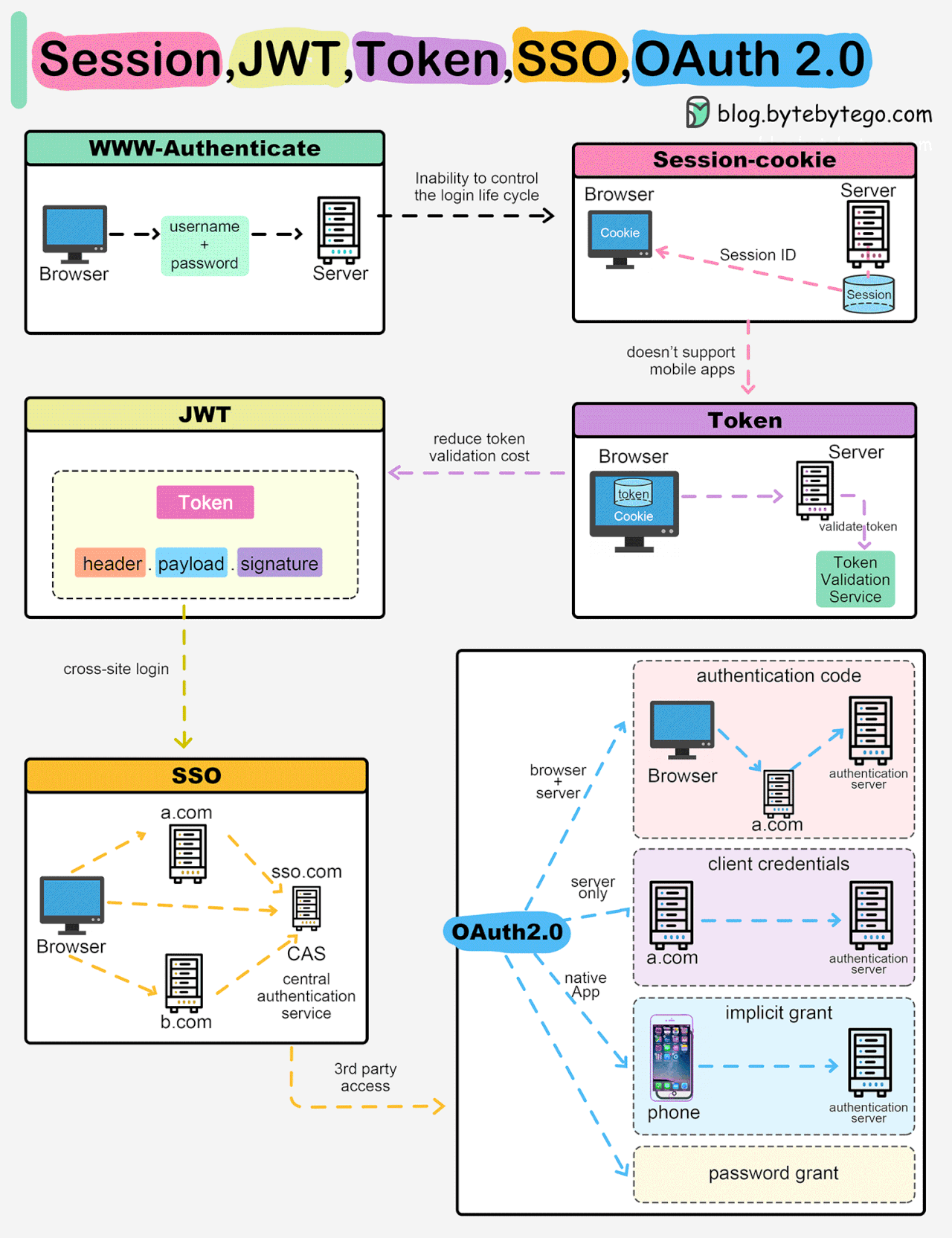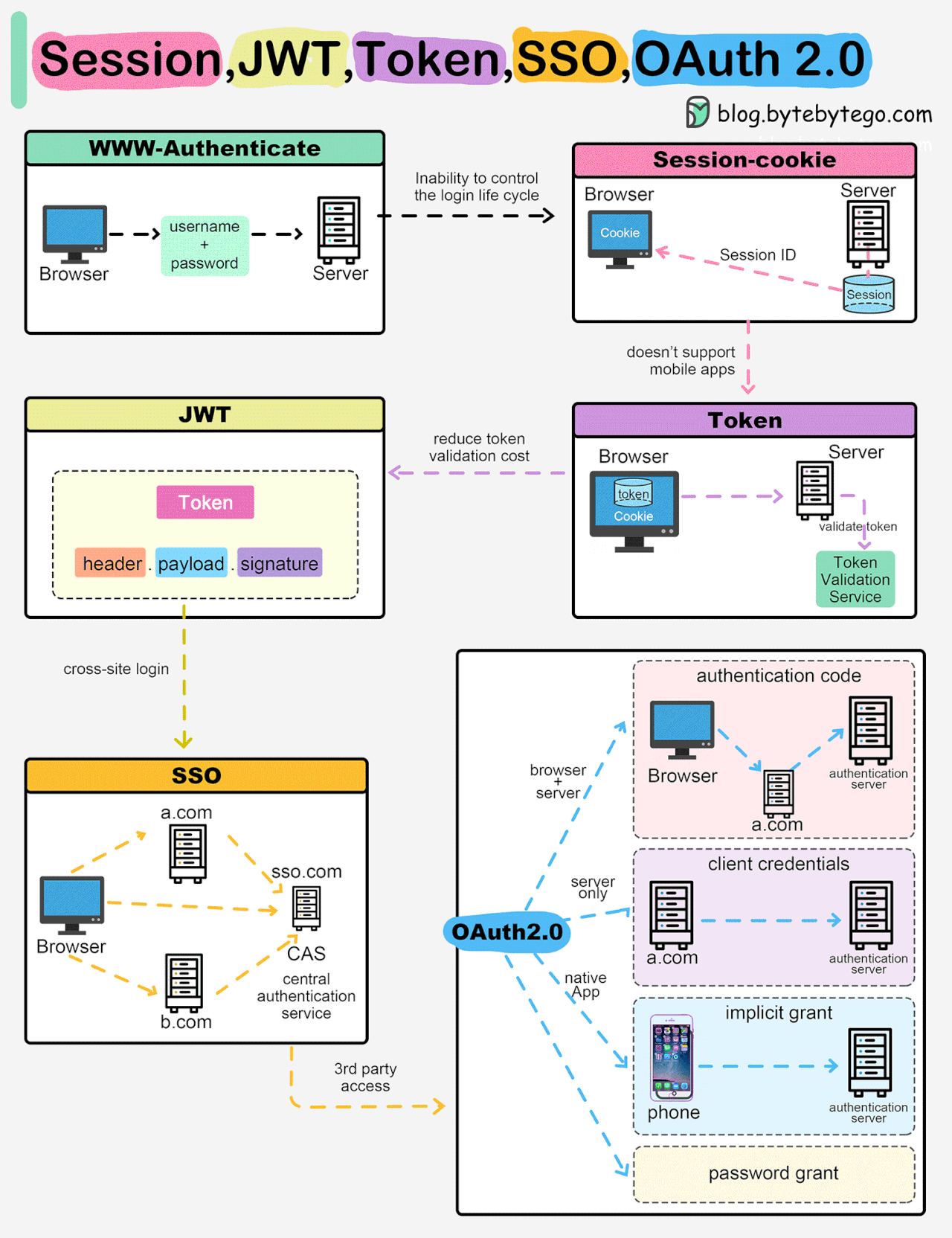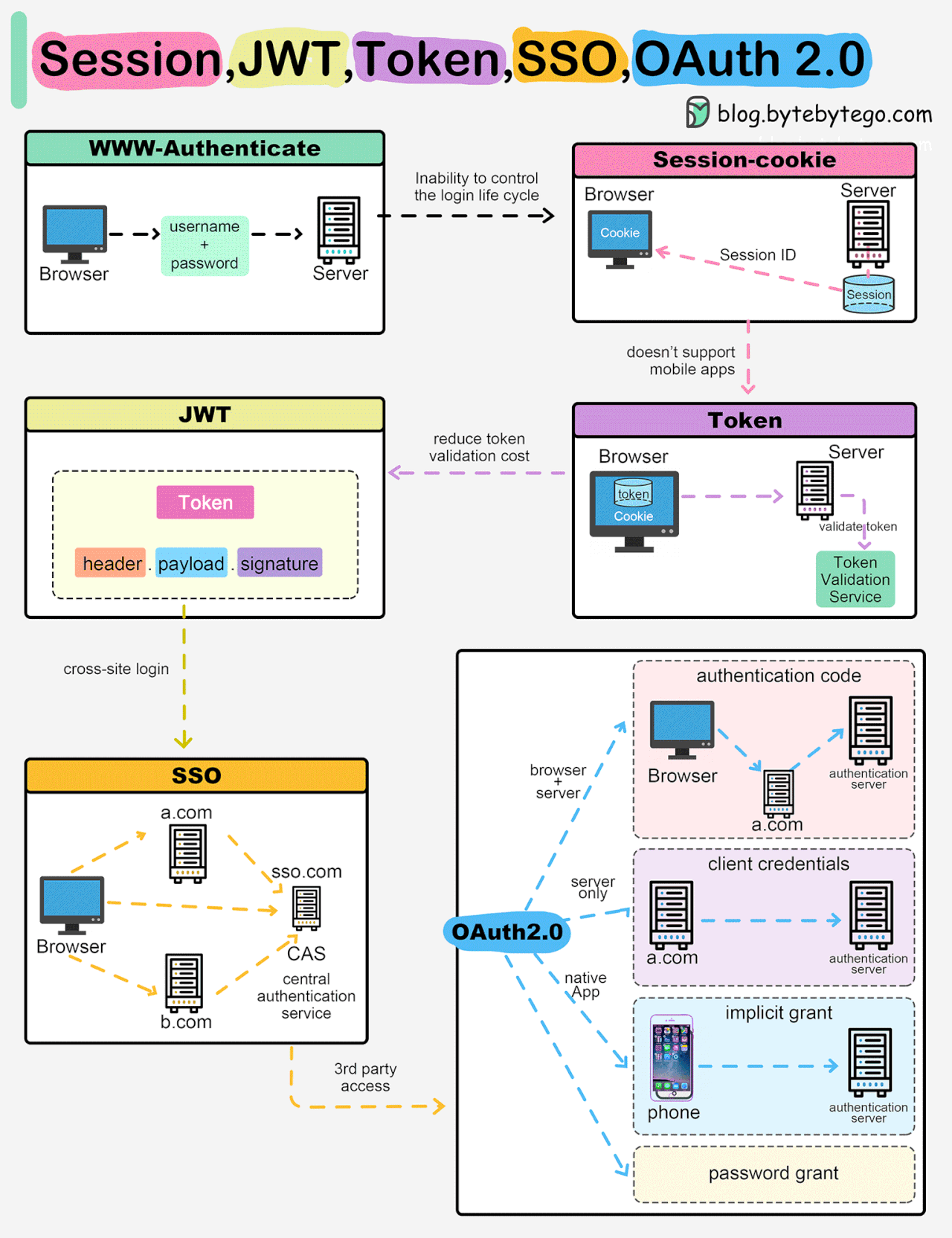
Session, Cookie, JWT, Token, SSO, and OAuth 2.0 Explained in One Diagram
When you login to a website, your identity needs to be managed. Here is how different solutions work:
Session - The server stores your identity and gives the browser a session ID cookie. This allows the server to track login state. But cookies don't work well across devices.
Token - Your identity is encoded into a token sent to the browser. The browser sends this token on future requests for authentication. No server session storage is required. But tokens need encryption/decryption.
JWT - JSON Web Tokens standardize identity tokens using digital signatures for trust. The signature is contained in the token so no server session is needed.
SSO - Single Sign On uses a central authentication service. This allows a single login to work across multiple sites.
OAuth2 - Allows limited access to your data on one site by another site, without giving away passwords.
QR Code - Encodes a random token into a QR code for mobile login. Scanning the code logs you in without typing a password.
Over to you: QR code logins are gaining popularity. Do you know how it works?
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com.