EP162: 9 Clean Code Principles To Keep In Mind
🚀 Faster mobile app releases with 100% parallel automated QA (Sponsored)
Manual testing on personal devices is too slow and too limited. It forces teams to cut releases a week early just to test before submitting them to app stores. And without broad device coverage, issues slip through.
QA Wolf gets mobile apps to 80% automated test coverage in weeks. They create and maintain your test suite in Appium (no vendor lock-in) — and provide unlimited, 100% parallel test runs with zero flakes.
✅ QA cycles reduced from hours to less than 15 minutes
✅ Tests run on real iOS devices and Android emulators
✅ Flake-free runs, no false positives
✅ Human-verified bug reports
No more manual E2E testing. No more slow QA cycles. No more bugs reaching production.
Rated 4.8/5 ⭐ on G2
This week’s system design interview:
9 Clean Code Principles To Keep In Mind
The 4 Types of SQL Joins
How to Learn Cloud Computing?
Visualizing a SQL query
Explaining JSON Web Token (JWT) with simple terms
SPONSOR US
9 Clean Code Principles To Keep In Mind
Meaningful Names: Name variables and functions to reveal their purpose, not just their value.
One Function, One Responsibility: Functions should do one thing.
Avoid Magic Numbers: Replace hard-code values with named constants to give them meaning.
Use Descriptive Booleans: Boolean names should state a condition, not just its value.
Keep Code DRY: Duplicate code means duplicate bugs. Try and reuse logic where it makes sense.
Avoid Deep Nesting: Flatten your code flow to improve clarity and reduce cognitive load.
Comment Why, Not What: Explain the intention behind your code, not the obvious mechanics.
Limit Function Arguments: Too many parameters confuse. Group related data into objects.
Code Should Be Self-Explanatory: Well-written code needs fewer comments because it reads like a story.
Over to you: Which other clean code principle will you add to the list?
Guide to AI Assisted Engineering (Sponsored)
The zero-to-one guide for teams adopting AI coding assistants. This guide shares proven prompting techniques, the use cases that save the most time for developers, and leadership strategies for encouraging adoption. It’s designed to be something engineering leaders can distribute internally to help teams get started with integrating AI into their daily work.
Download this guide to get:
The 10 most time-saving use cases for AI coding tools
Effective AI prompting techniques from experienced AI users
Leadership strategies for encouraging AI use
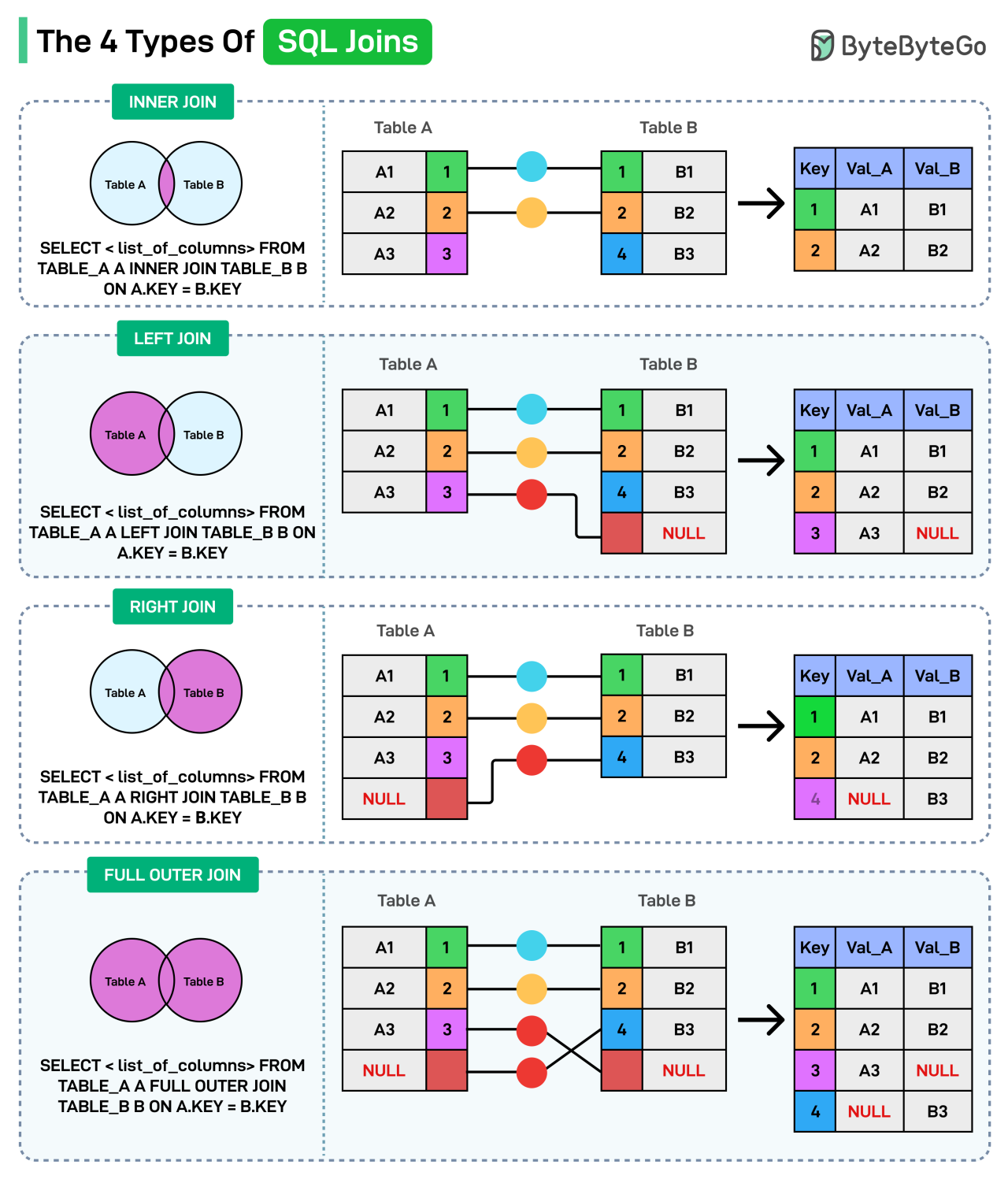
The 4 Types of SQL Joins
SQL joins combine rows from two or more tables based on a related column. Here are the different types of joins you can use:
Inner Join
Returns only the matching rows between both tables. It keeps common data only.
Left Join
Returns all rows from the left table and matching rows from the right table. If a row in the left table doesn’t have a match in the right table, the right table’s columns will contain NULL values in that row.
Right Join
Returns all rows from the right table and matching rows from the left table. If no matching record exists in the left table for a record in the right table, the columns from the left table in the result will contain NULL values.
FULL OUTER JOIN
Returns all rows from both tables, filling in NULL for missing matches.
Over to you: Which SQL Join have you used the most?
How to Learn Cloud Computing?
Cloud computing is a vast field with an ever-growing footprint. It can often get tricky for a new developer to understand where to start. Here’s a learning map:
Cloud Computing Basics
This includes topics such as “what is cloud computing,” its benefits, cloud models (public, private, hybrid, and multi), and a comparison of cloud vs. on-premise.
Cloud Service Models
Learn about cloud service models such as IaaS, PaaS, and SaaS.
Cloud Providers
Explore the various popular cloud platforms such as AWS, Azure, GCP, Oracle Cloud, IBM Cloud, etc. Also, learn how to choose a cloud provider.
Key Cloud Services
Learn the key cloud services related to Compute (EC2, Azure VM, Docker, Kubernetes, Lambda, etc), Storage (EBS, Azure Disk, S3, Azure Blob, EFS, etc.), and Networking (VPC, ELB, Azure LB, Cloudfront, and Azure CDN).
Security & Compliance
Learn about the critical security and compliance points related to identity, access management, encryption, data security, DDoS protection, and WAF.
Cloud DevOps & Automation
Learn Cloud DevOps and automation in specific areas such as CI/CD, IaC, and Monitoring.
Over to you: What else will you add to the list for learning cloud computing?
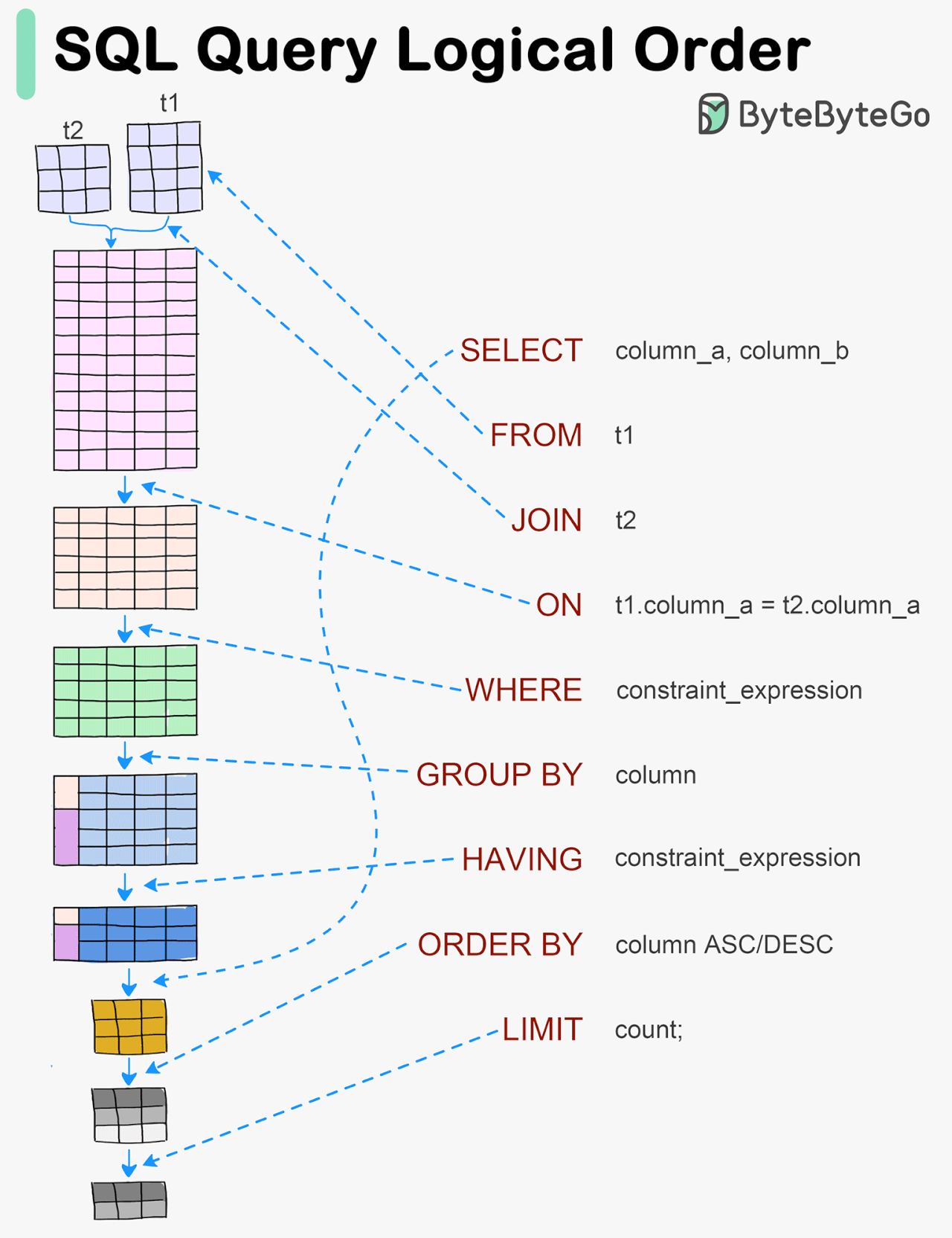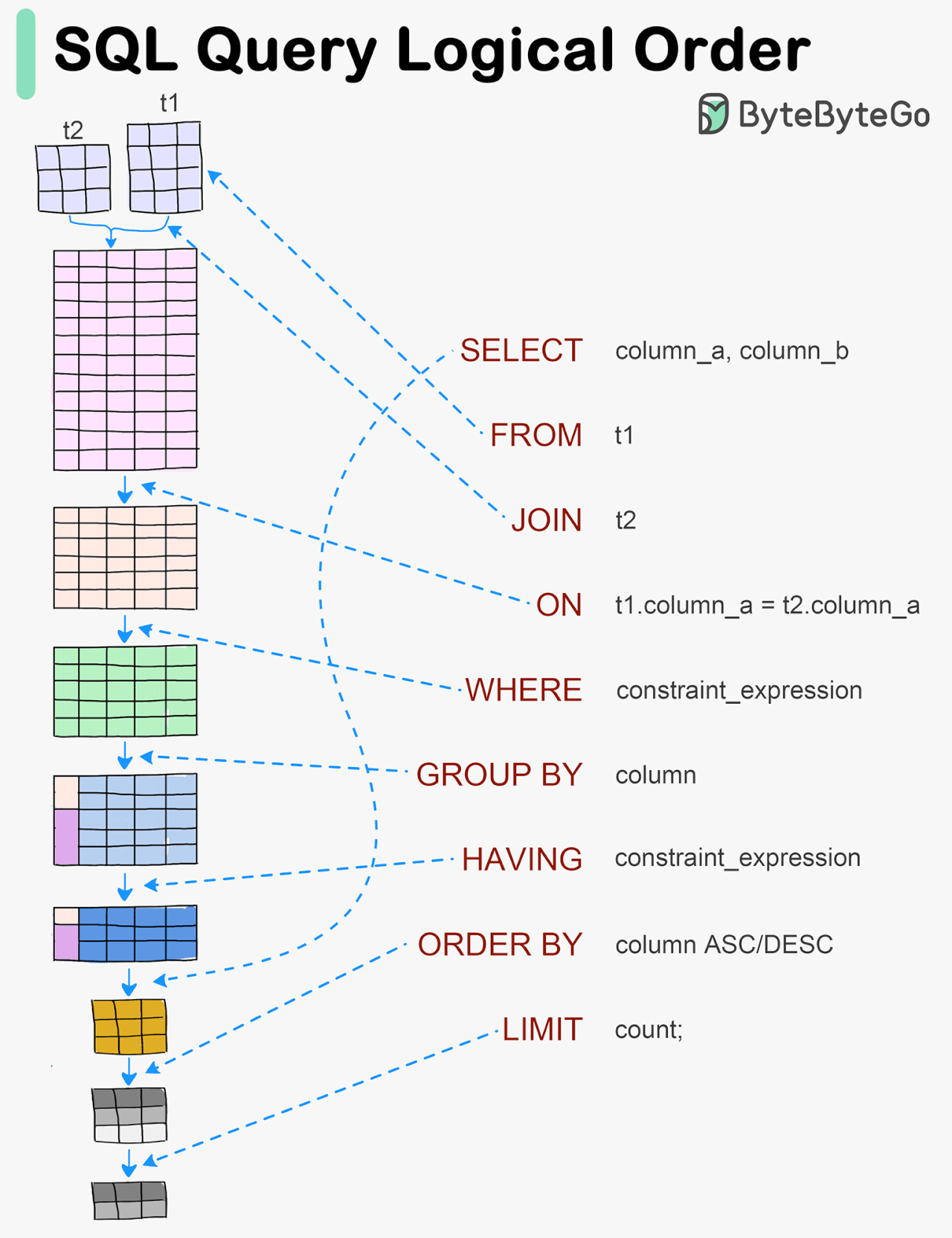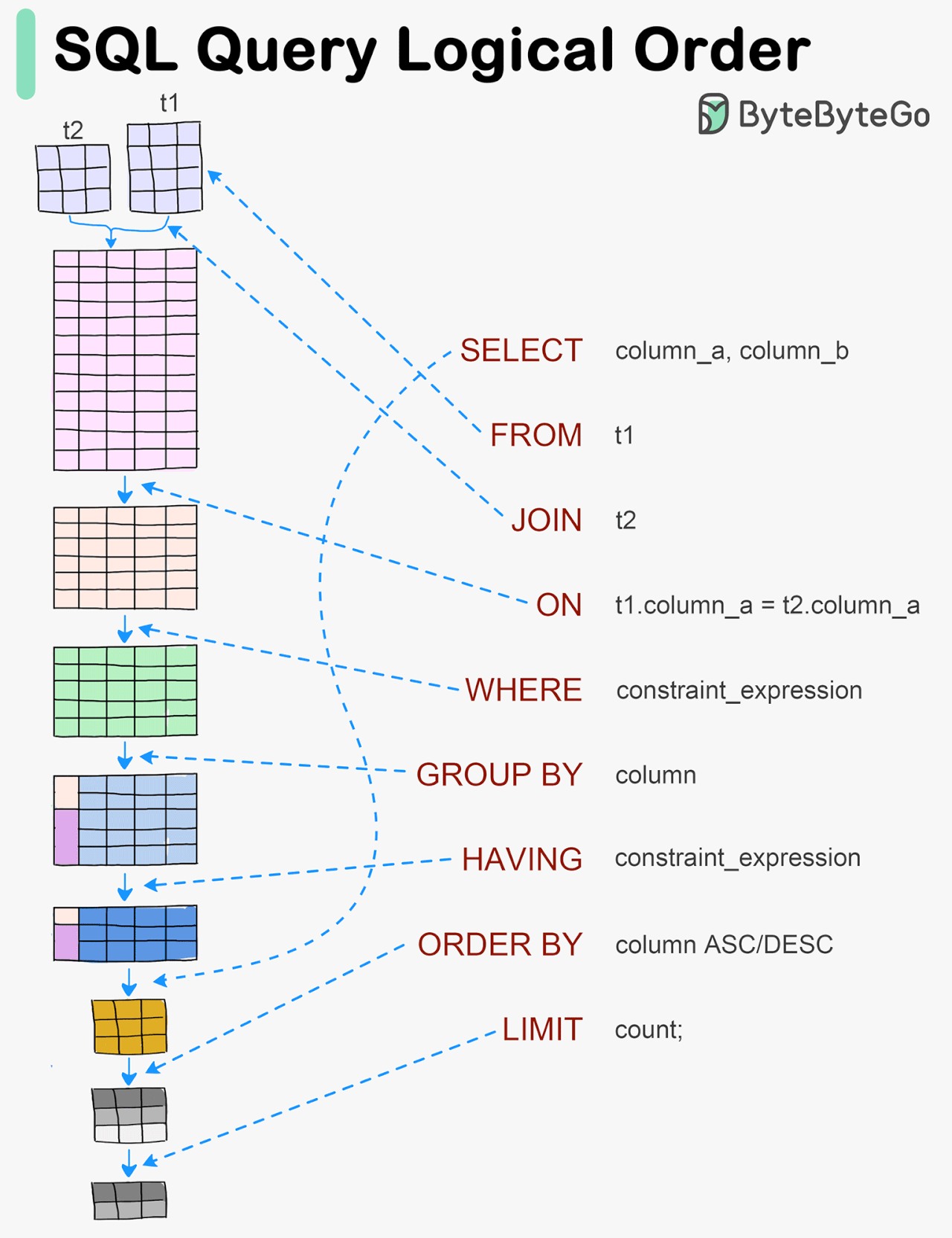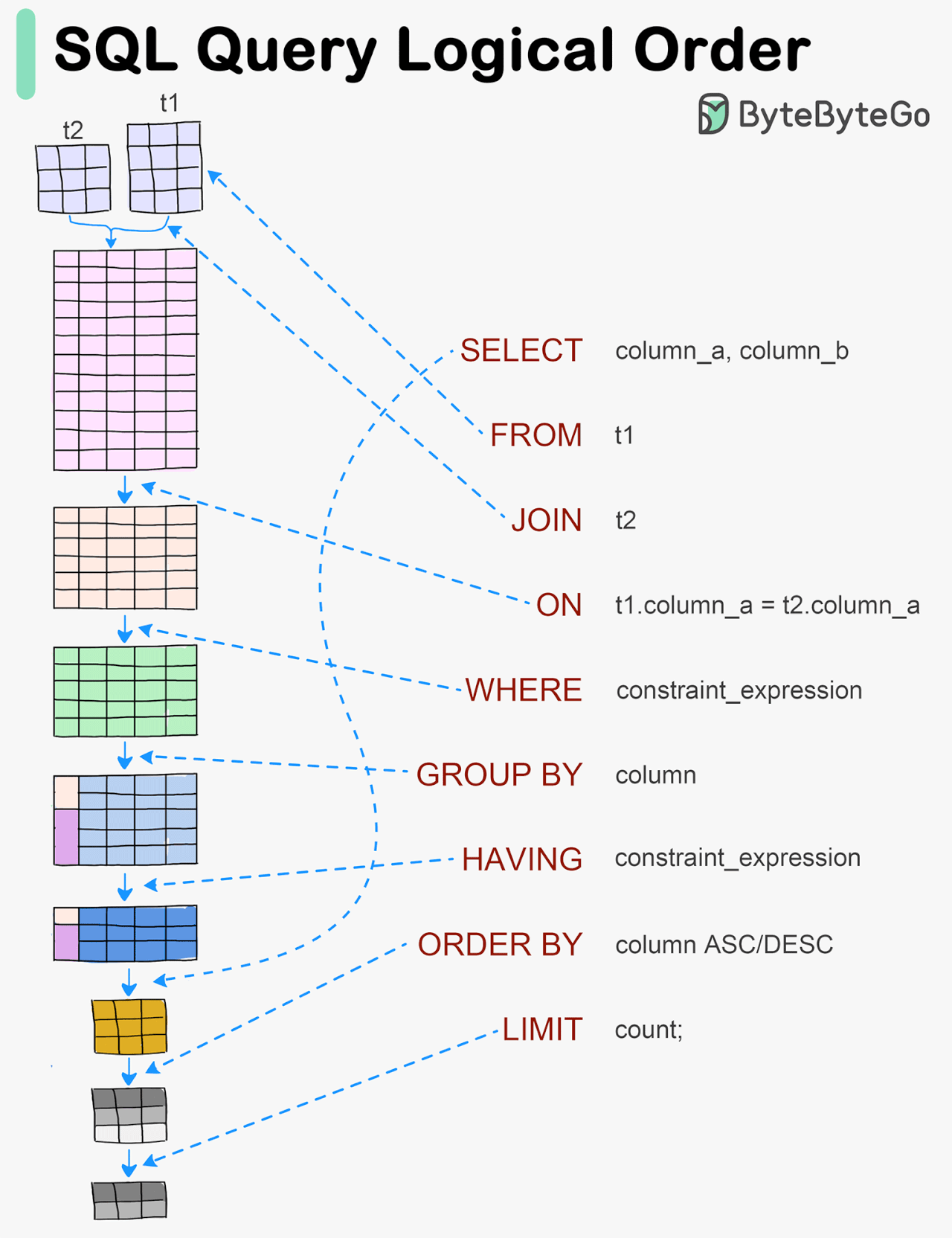
Visualizing a SQL query
SQL statements are executed by the database system in several steps, including:
Parsing the SQL statement and checking its validity
Transforming the SQL into an internal representation, such as relational algebra
Optimizing the internal representation and creating an execution plan that utilizes index information
Executing the plan and returning the results
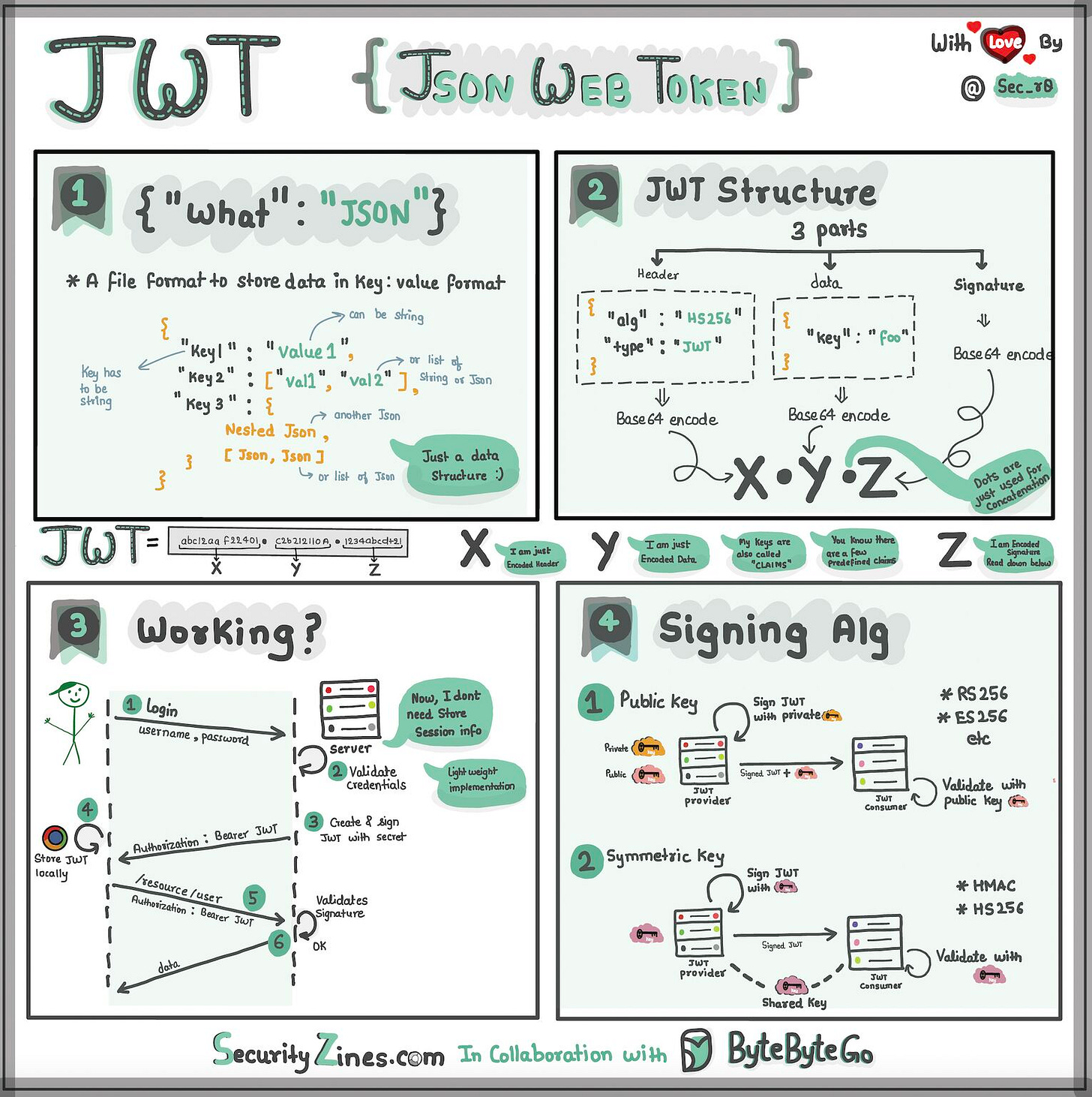
Explaining JSON Web Token (JWT) with simple terms
Imagine you have a special box called a JWT. Inside this box, there are three parts: a header, a payload, and a signature.
The header is like the label on the outside of the box. It tells us what type of box it is and how it's secured. It's usually written in a format called JSON, which is just a way to organize information using curly braces { } and colons : .
The payload is like the actual message or information you want to send. It could be your name, age, or any other data you want to share. It's also written in JSON format, so it's easy to understand and work with.
Now, the signature is what makes the JWT secure. It's like a special seal that only the sender knows how to create. The signature is created using a secret code, kind of like a password. This signature ensures that nobody can tamper with the contents of the JWT without the sender knowing about it.
When you want to send the JWT to a server, you put the header, payload, and signature inside the box. Then you send it over to the server. The server can easily read the header and payload to understand who you are and what you want to do.
Over to you: When should we use JWT for authentication? What are some other authentication methods?
SPONSOR US
Get your product in front of more than 1,000,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing sponsorship@bytebytego.com.






For "Key Cloud Services", I think we can also have Database services like AWS DynamoDB, RDB, etc.
Great stuff!!