EP197: 12 Architectural Concepts Developers Should Know
How Sentry Built Production-Informed AI Code Reviews (Sponsored)
In order to have your code review reflect real system behavior, you can integrate production signals into developer workflows.
Sentry built Seer to connect production failure signals to incoming code changes before merge.
Under the hood is a multi-stage bug prediction pipeline ⚙️
Filtering: large change sets are scoped down to files with the strongest historical failure signals
Prediction: models generate and cross-check bug hypotheses using code context and production telemetry
Prioritization: findings are ranked by estimated risk so only high-confidence issues surface during review
See how this works in practice on the Sentry blog.
This week’s system design refresher:
12 Architectural Concepts Developers Should Know
Top Developer Tools You Can Use in 2026
5 Rate Limiting Strategies To Protect the System
How Live Streaming Works?
5 Leader Election Algorithms Powering Modern Databases
🚀 Learn AI in the New Year: Become an AI Engineer Cohort 3 Now Open
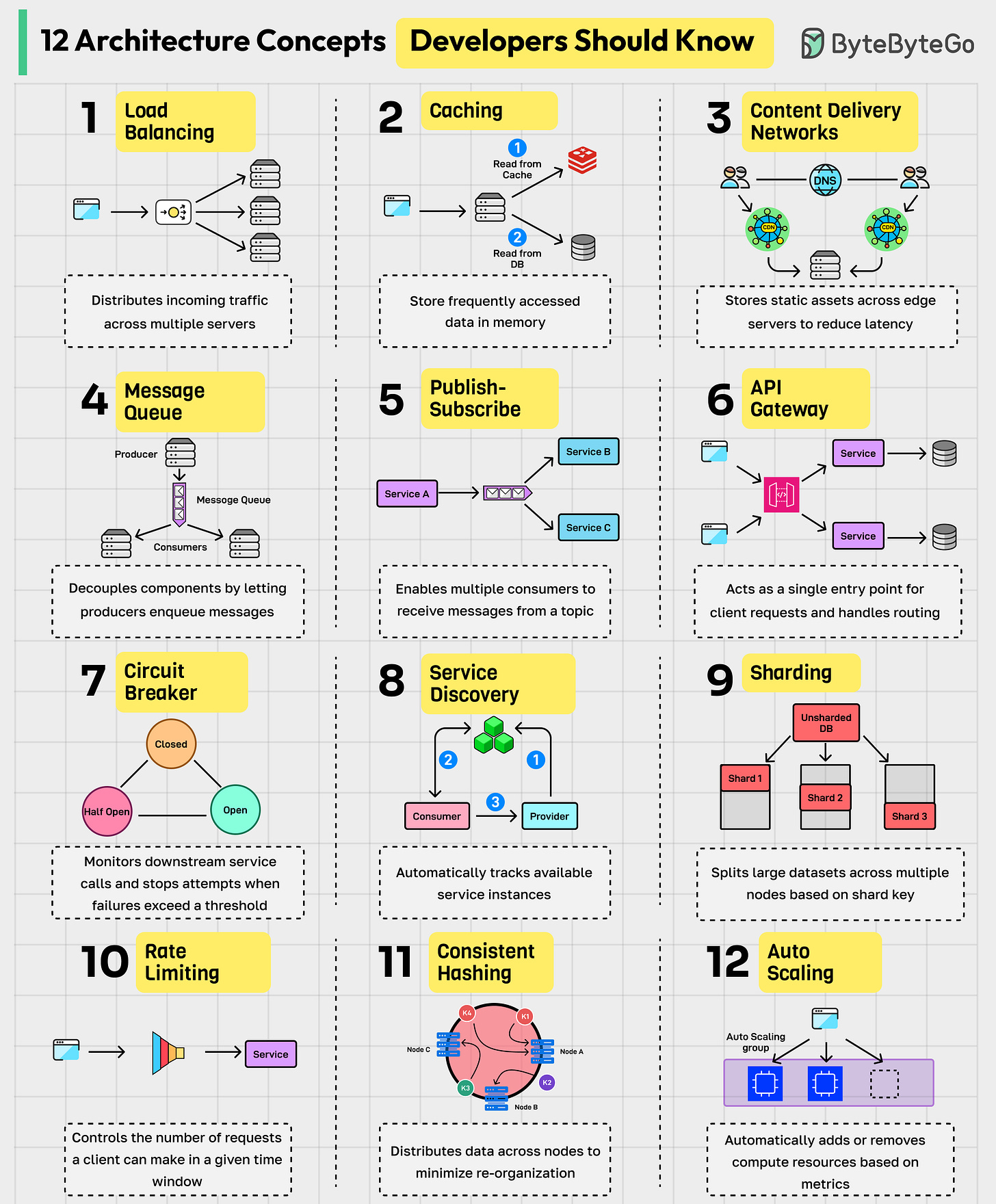
12 Architectural Concepts Developers Should Know
Load Balancing: Distributed incoming traffic across multiple servers to ensure no single node is overwhelmed.
Caching: Stores frequently accessed data in memory to reduce latency.
Content Delivery Network (CDN): Stores static assets across geographically distributed edge servers so users download content from the nearest location.
Message Queue: Decouples components by letting producers enqueue messages that consumers process asynchronously.
Publish-Subscribe: Enables multiple consumers to receive messages from a topic.
API Gateway: Acts as a single entry point for client requests, handling routing, authentication, rate limiting, and protocol translation.
Circuit Breaker: Monitors downstream service calls and stops attempts when failures exceed a threshold.
Service Discovery: Automatically tracks available service instances so components can locate and communicate with each other dynamically.
Sharding: Splits large datasets across multiple nodes based on a specific shard key.
Rate Limiting: Controls the number of requests a client can make in a given time window to protect services from overload.
Consistent Hashing: Distributes data across nodes in a way that minimizes reorganization when nodes join or leave.
Auto Scaling: Automatically adds or removes compute resources based on defined metrics.
Over to you: Which architectural concept will you add to the list?
Top Developer Tools You Can Use in 2026
Code Editors & IDEs: These tools help developers write, edit, and debug code with greater efficiency. Examples are Visual Code, IntelliJ IDEA, PyCharm, Cursor, Eclipse, etc.
Version Control Systems: Track code changes over time and enable collaboration between team members. Examples are Git, GitHub, Gitlab, Bitbucket, AWS Code Commit, etc.
Testing Tools: Help ensure that code behaves as expected by identifying bugs before they reach production. Examples are JUnit, Selenium, Playwright, Cypress, etc.
CI/CD Tools: They help automate the process of building and deploying code to speed up delivery. Examples are Jenkins, GitHub Actions, Circle CI, Travis CI, and Code Pipeline.
Containerization and Orchestration: Helps package applications and their dependencies into containers to make sure they run across environments in a consistent manner. Examples are Docker, Kubernetes, Podman, Containerd, Rancher, etc.
Project Management Tools: Helps the development teams plan, organize, and track the development of tasks. Examples are JIRA, Asana, Trello, ClickUp, Notion, etc.
API Testing Tools: They help test and validate APIs to ensure stable communication between services and with external consumers. Examples are Postman, Swagger, Hopscotch, Insomnia, etc.
AI-Powered Developer Tools: They are mainly used to boost developer productivity with code suggestions, error detection, and automated code generation. Examples are ChatGPT, Claude Code, Cursor, Copilot, Qodo, etc.
Over to you: Which other tools have you used?
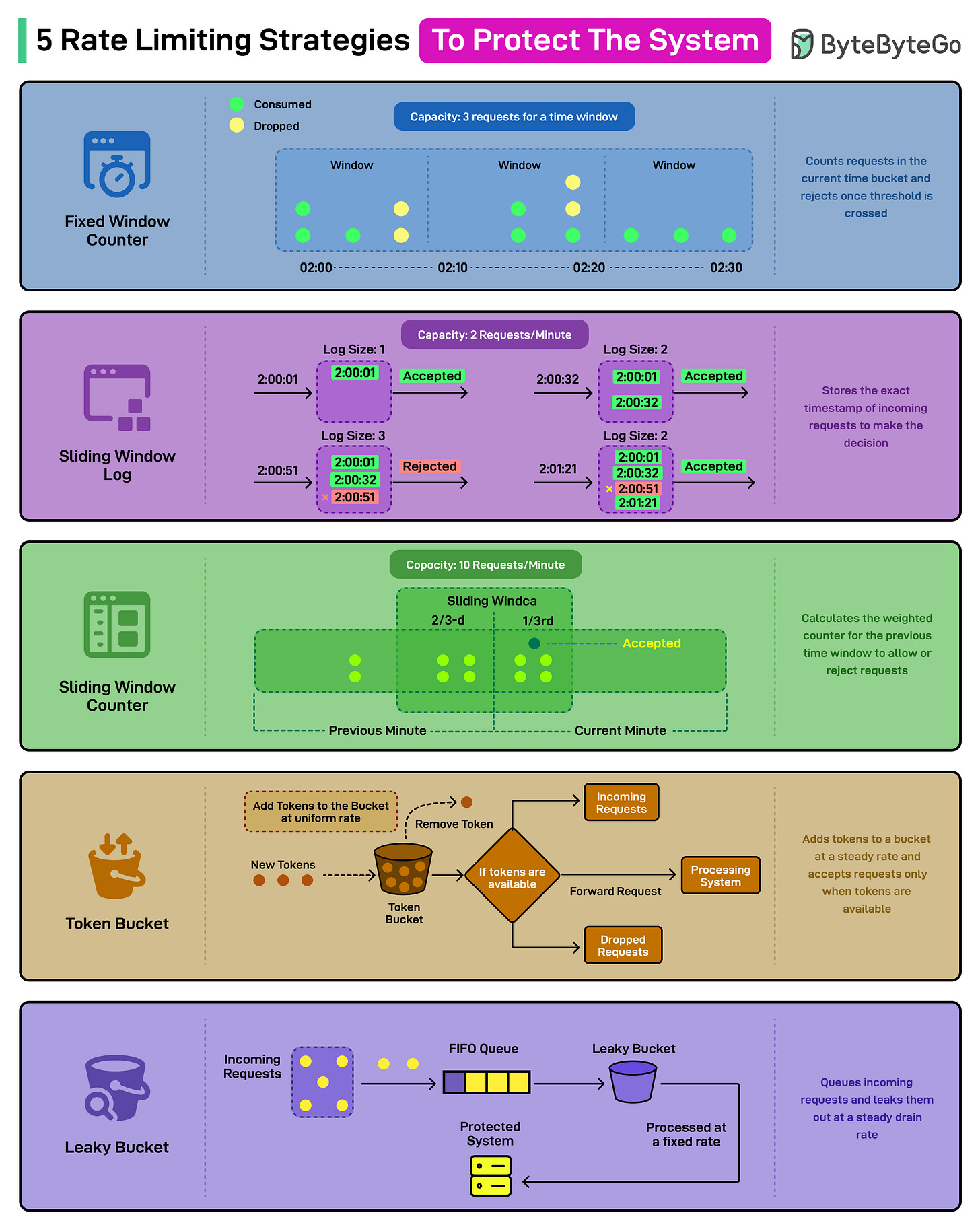
5 Rate Limiting Strategies To Protect the System
Rate limiting protects services from overload or abuse by shaping traffic to match capacity and by enforcing policy as soon as a request arrives. A good rate limiter optimizes for accuracy, predictability, fairness, and low overhead, and real systems trade one for another.
Fixed Window Counter: Involves counting requests in the current discrete time bucket and rejecting once the threshold is reached.
Sliding Window Log: Stores exact timestamps of the incoming requests and admits a request only if the last T seconds remain under the limit.
Sliding Window Counter: Instead of keeping a log of request timestamps, it calculates the weighted counter for the previous time window. When a new request arrives, the counter is adjusted based on the weight, and the request is allowed if the total is below the limit.
Token Bucket: Works by adding “tokens” to a bucket at a steady rate. Each request consumes one token. If tokens are available, the request passes immediately. If the bucket is empty, requests are rejected or delayed.
Leaky Bucket: Queues requests and lets them out at a fixed drain rate.
Over to you: Which other rate-limiting strategy will you add to the list?
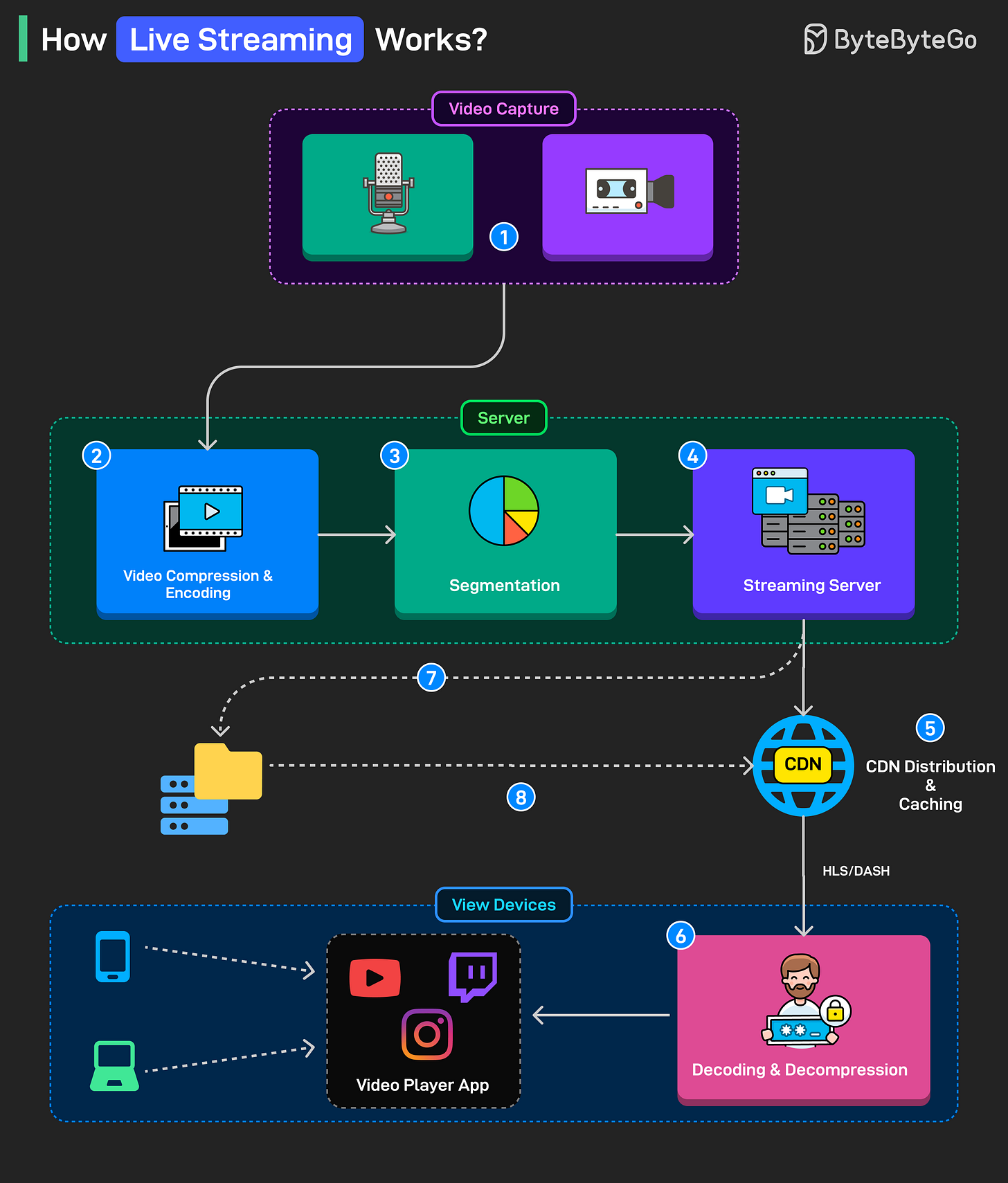
How Live Streaming Works?
Live streaming works using a few key protocols such as RTMP, HLS (made by Apple), and DASH (for non-Apple devices).
Here’s a step-by-step process:
Step 1: The camera and microphone record video and audio. The raw data is sent to a server.
Step 2: The video is made smaller by removing unnecessary parts (like separating the background). Then, it’s converted into a standard format like H.264, which makes it easier to send over the internet.
Step 3: The video is chopped into small parts, usually a few seconds long. This helps it load faster during streaming.
Step 4: To make sure the video plays smoothly on all kinds of devices and internet speeds, multiple versions of the video are created at different quality levels. This is called Adaptive Bitrate Streaming.
Step 5: The video is then sent to nearby servers (edge servers) using a CDN. This reduces delay and helps millions of people watch the video at the same time.
Step 6: The viewer’s phone, tablet, or computer receives the video, turns it back into full video and sound, and plays it in a video player.
Steps 7 and 8: If the video needs to be watched again later, it's saved on a storage server. Viewers can replay it whenever they want.
Over to you: What else will you add to understand the live streaming process?
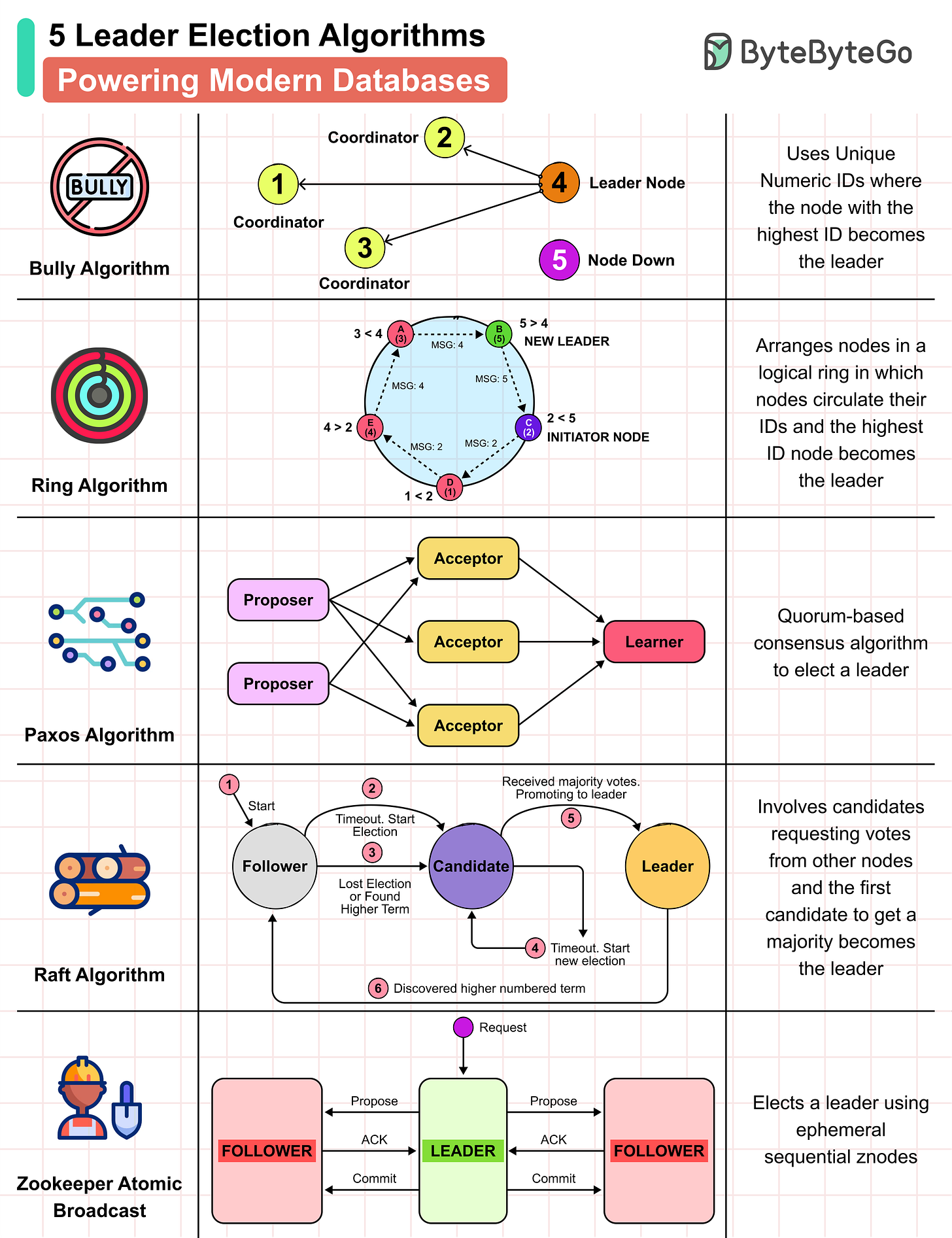
5 Leader Election Algorithms Powering Modern Databases
Leader Election Algorithms are important in distributed systems to manage tasks, maintain consistency, and make decisions.
Bully Algorithm: Nodes have unique numeric IDs, and the one with the highest ID takes over as leader after notifying others.
Ring Algorithm: Nodes are arranged in a logical ring and pass messages containing their IDs. The highest ID node wins and becomes the leader.
Paxos Algorithm: A quorum-based consensus method where proposers suggest values, acceptors vote, and a learner recognizes the chosen leader.
Raft Algorithm: Nodes start as followers and become candidates if no leader is detected. The first to secure a majority of votes becomes the leader.
Zookeeper Atomic Broadcast: Uses ephemeral sequential znodes to elect the leader, ensuring that the lowest-numbered znode holder is the leader.
Over to you: Which other Leader Election Algorithm have you seen?
🚀 Learn AI in the New Year: Become an AI Engineer Cohort 3 Now Open
After the amazing success of Cohorts 1 and 2 (with close to 1,000 engineers joining and building real AI skills), we are excited to announce the launch of Cohort 3 of Become an AI Engineer!



The leader election algorithms left me quite overwhelmed . First time coming across these terms 🤔
This Is Awsome!