EP199: Behind the Scenes: What Happens When You Enter Google.com
Debugging Next.js in Production (Sponsored)
Next.js makes it easy to ship fast, but once your app is in production it can be hard to tell where errors, slow requests, or hydration issues are really coming from.
Join Sentry’s hands-on workshop where Sergiy Dybskiy will dive into how these problems show up in real apps and how to connect what users experience with what’s happening under the hood. 🚀
This week’s system design refresher:
What Are AI Agents & How Do They Work? (Youtube video)
Behind the Scenes: What Happens When You Enter Google.com
Understanding the Linux Directory Structure
Symmetric vs. Asymmetric Encryption
Network Troubleshooting Test Flow
We’re hiring at ByteByteGo
What Are AI Agents & How Do They Work?
Behind the Scenes: What Happens When You Enter Google.com
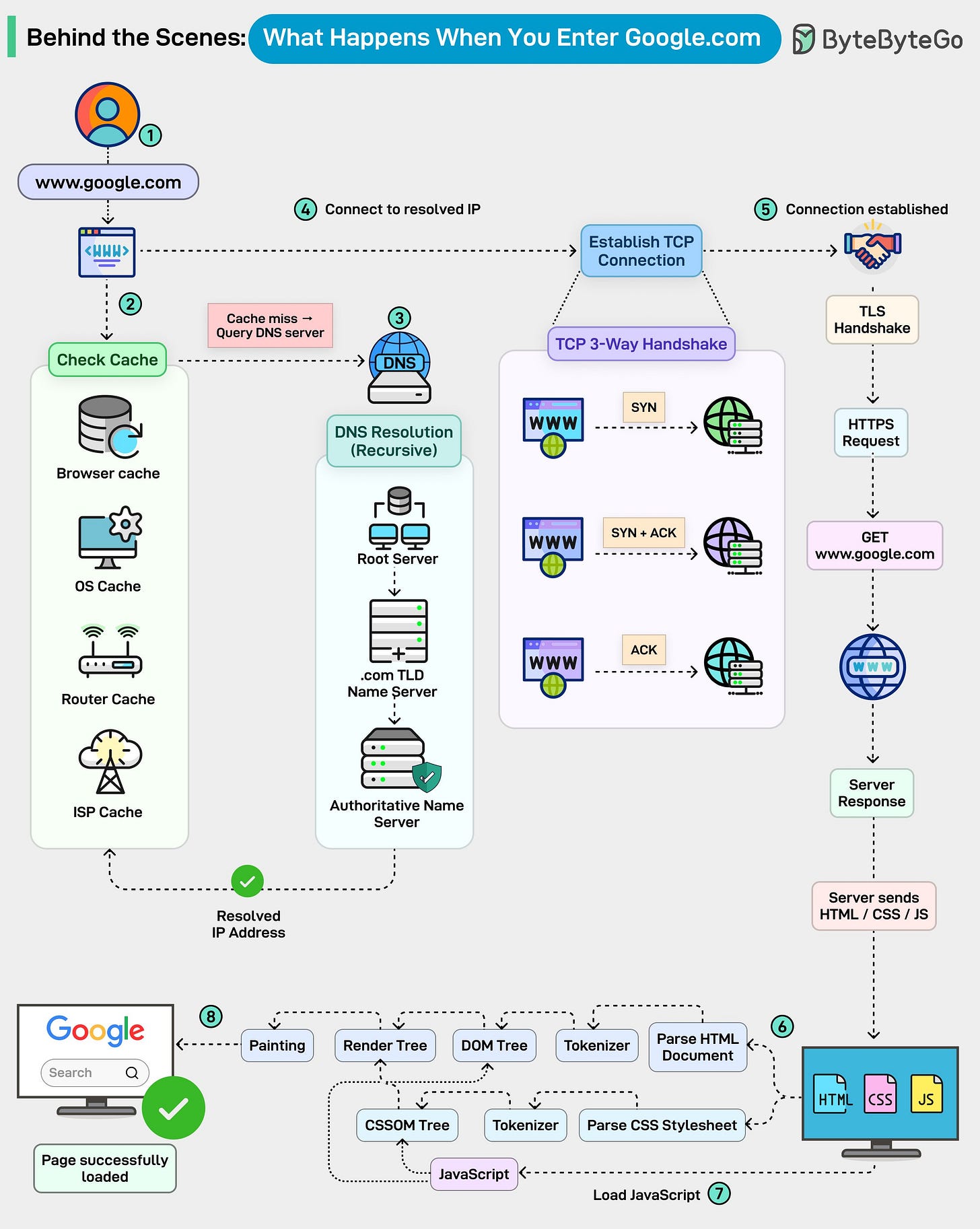
Most of us hit Enter and expect the page to load instantly, but under the hood, a surprisingly intricate chain of events fires off in milliseconds.
Here’s a quick tour of what actually happens:
The journey starts the moment you type “google. com” into the address bar.
The browser checks everywhere for a cached IP: Before touching the network, your browser looks through multiple cache layers, browser cache, OS cache, router cache, and even your ISP’s DNS cache.
A cache hit means an instant IP address. A miss kicks off the real journey.Recursive DNS resolution begins: Your DNS resolver digs through the global DNS hierarchy:
- Root servers
- TLD servers (.com)
- Authoritative servers for google. comA TCP connection is established: Your machine and Google’s server complete the classic TCP 3-way handshake:
- SYN → SYN/ACK → ACK
Only after the connection is stable does the browser move on. TLS handshake wraps everything in encryption. By the end of this handshake, a secure HTTPS tunnel is ready.The actual HTTP request finally goes out: Google processes the request and streams back HTML, CSS, JavaScript, and all the assets needed to build the page.
The rendering pipeline kicks in:
Your browser parses HTML into a DOM tree, CSS into a CSSOM tree, merges them into the Render Tree, and then:
- Lays out elements
- Loads and executes JavaScript
- Repaints the screen
8. The page is fully loaded.
Over to you: What part of this journey was most surprising the first time you learned how browsers work?
Understanding the Linux Directory Structure
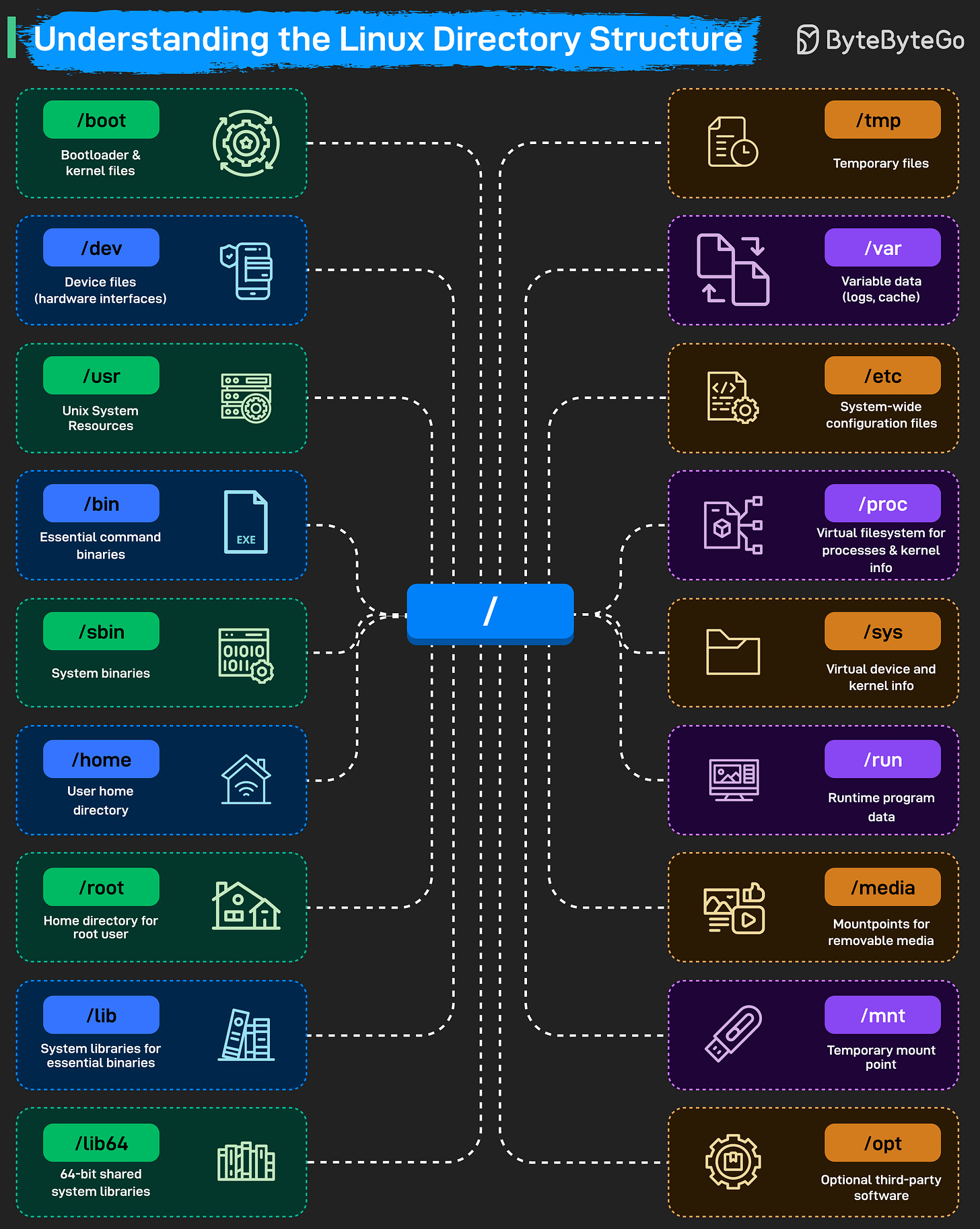
The root directory “/” is the starting point of the entire filesystem. From there, Linux organizes everything into specialized folders.
“/boot” stores the bootloader and kernel files, without it, the system can’t start.
“/dev” holds device files that act as interfaces to hardware.
“/usr” contains system resources, libraries, and user-level applications.
“/bin” and “/sbin” store essential binaries and system commands needed during startup or recovery.
User-related data sits under “/home” for regular users and “/root” for the root account.
System libraries that support core binaries live in “/lib” and “/lib64”.
Temporary data is kept in “/tmp”, while “/var” tracks logs, caches, and frequently changing files.
Configuration files live in “/etc”, and runtime program data lives in “/run”.
Linux also exposes virtual filesystems through “/proc” and “/sys”, giving you insight into processes, kernel details, and device information.
For external storage, “/media” and “/mnt” handle removable devices and temporary mounts, and “/opt” is where optional third-party software installs itself.
Over to you: Which Linux directory took you the longest to fully understand, and what finally made it click for you?
Symmetric vs. Asymmetric Encryption
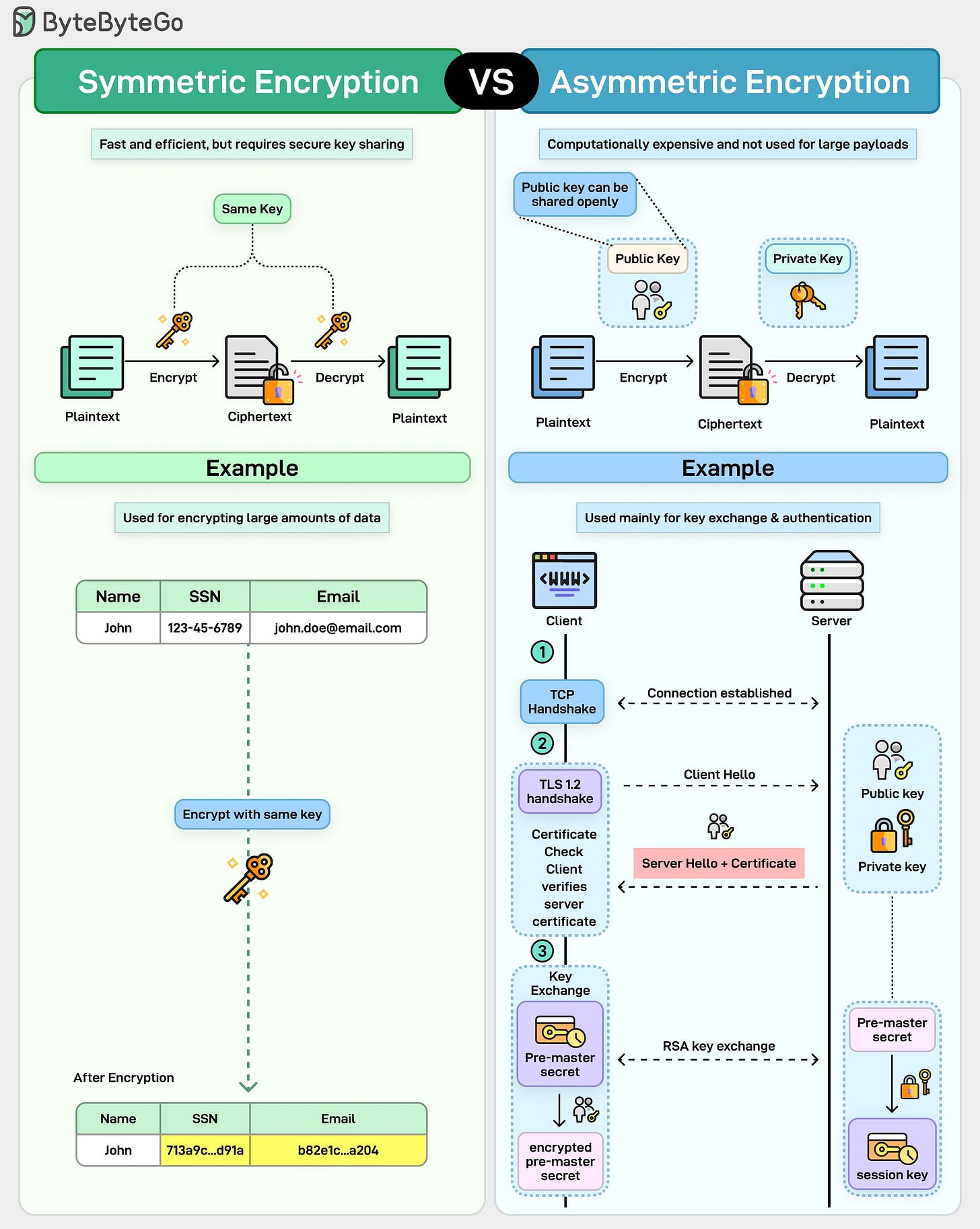
Symmetric and asymmetric encryption often get explained together, but they solve very different problems.
Symmetric encryption uses a single shared key. The same key encrypts and decrypts the data. It’s fast, efficient, and ideal for large amounts of data. That’s why it’s used for things like encrypting files, database records, and message payloads.
The catch is key distribution, both parties must already have the secret, and sharing it securely is hard.Asymmetric encryption uses a key pair. A public key that can be shared with anyone, and a private key that stays secret. Data encrypted with the public key can only be decrypted with the private key.
This removes the need for secure key sharing upfront, but it comes at a cost. It’s slower and computationally expensive, which makes it impractical for encrypting large payloads.
That’s why asymmetric encryption is usually used for identity, authentication, and key exchange, not bulk data.
Over to you: What’s the most common misunderstanding you’ve seen about encryption in system design?
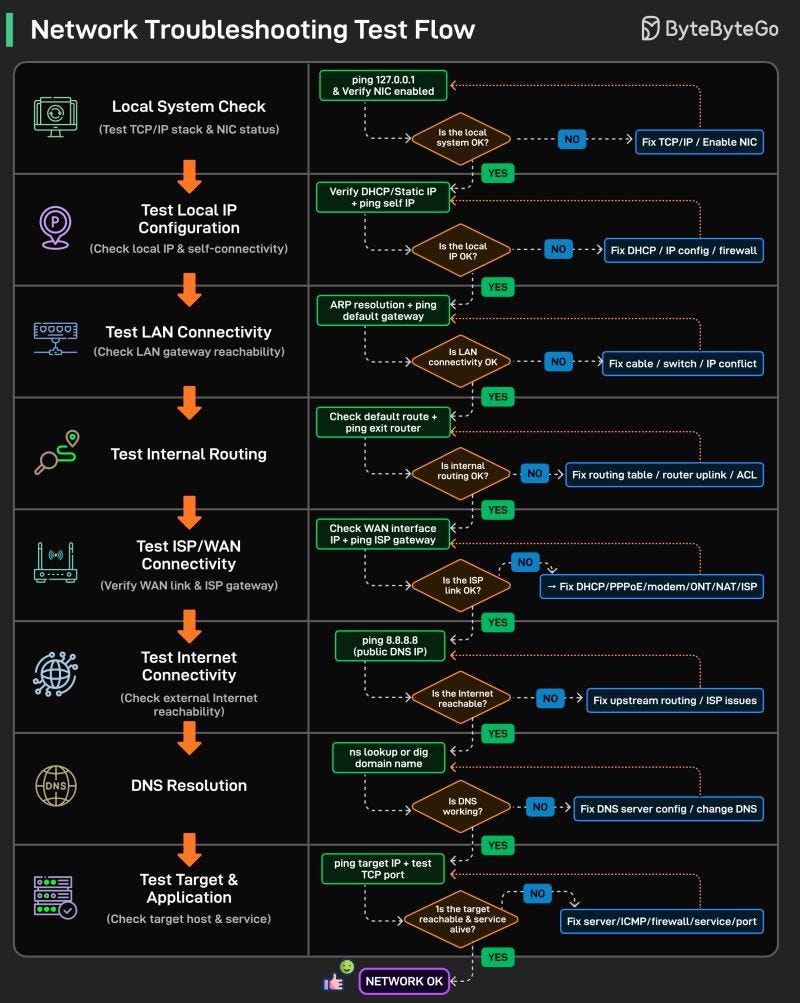
Network Troubleshooting Test Flow
Most network issues look complicated, but the troubleshooting process doesn’t have to be.
A reliable way to diagnose problems is to test the network layer by layer, starting from your own machine and moving outward until you find exactly where things break.
That’s exactly why we put together this flow: a structured, end-to-end checklist that mirrors how packets actually move through a system.
We’re Hiring
I am hiring for 2 roles: Technical Deep Dive Writer (System Design or AI Systems), and Lead Instructor (Building the World’s Most Useful AI Cohort). Job descriptions below.
1. Technical Deep Dive Writer
ByteByteGo started with a simple idea: explain system design clearly. Over time, it has grown into one of the largest technical education platforms for engineers, reaching millions of engineers every month. We believe it can become much bigger and more impactful.
This role is for someone exceptional who wants to help build that future by producing the highest-quality technical content on the internet.
You will work very closely with me to produce deep, accurate, and well structured technical content. The goal is not volume. The goal is to set the quality bar for how system design and modern AI systems are explained at scale.
The role is to turn technical knowledge into world class technical writing.
What you will do:
Turn complex systems into explanations that are precise, readable, and memorable.
Create clear technical diagrams that accurately represent system architecture and tradeoffs.
Collaborate directly with tech companies like Amazon, Shopify, Cursor, Yelp, etc.
Continuously raise the bar for clarity, correctness, and depth.
Who we are looking for
5+ years of experience building large scale systems
Ability to explain complex ideas without oversimplifying
Strong ownership mindset and pride in craft
Role Type: Part time remote (10-20 hours per week), with the possibility of converting to full time
Compensation: Competitive
This is not just a writing role. It is a chance to help build the most trusted technical education brand in the industry.
How to apply: If you are interested, please send your resume and a previous writing sample to jobs@bytebytego.com
2. Lead Instructor, Building the World’s Most Useful AI Cohort
Cohort Course Name: Building Production AI Systems
This cohort is focused on one of the hardest problems in modern engineering. Taking AI systems from impressive demos to reliable, secure, production ready systems used by real users.
Our learners already understand generative AI concepts. What they want and need is engineering rigor. How to evaluate models properly. How to ship safely. How to scale without blowing up cost or reliability. How to operate AI systems in the real world.
This role is for someone exceptional who has done this work in production and wants to help shape the future of AI engineering education.
Role Type: Part time remote (20+ hours per week), with the possibility of converting to full time
Compensation: Very Competitive
Responsibilities
Develop and maintain a curriculum centered on ai production
Design labs/assignments. Keep them runnable with modern tooling
Teach live sessions (lecture + hands-on lab)
Run weekly office hours
Provide clear feedback on assignments and async questions
Required expertise
Production AI Engineering
You have shipped and maintained AI features used by thousands of users. You have “war stories” regarding outages, cost spikes, or quality regressions.
Deep understanding of the FastAPI + Pydantic + Celery/Redis stack for handling asynchronous AI tasks.
Can articulate the nuances between Latency vs. Cost and Reliability vs. Velocity.
AI Evals
experience in evaluating AI systems like LLMs, RAGs, Agents, or image/video generation models)
Ability to explain standard metrics and design eval datasets (golden, adversarial, regression)
implement scoring (rules, rubrics, LLM-as-judge with guardrails)
Familiar with industry eval patterns and frameworks (e.g., OpenAI Evals)
AI security and guardrails
prompt injection,
insecure output handling, model DoS, supply chain risks.
Threat Modeling: Experience mapping threats to taxonomies like MITRE ATLAS.
Implementing input sanitization and output validation to prevent prompt injection and model DoS.
Deployment and optimization
Infrastructure: Comfort with Docker, Kubernetes, and hybrid routing (using a mix of self-hosted and managed APIs like Azure OpenAI or Bedrock).
Optimization: Hands-on experience with Quantization (FP8/INT8), Prompt Caching, Pruning, distillation, distributed inference, efficient attention variants, and batching strategies to maximize throughput.
Serving Engines like vLLM or NVIDIA TensorRT-LLM.
Comfortable with production deployment patterns (containerization, staged rollouts, canaries).
Backend: Python (Expert), FastAPI, Pydantic v2, and asynchronous programming.
Monitoring and observability
Ability to teach tracing and quality monitoring
Desirable Technical Stack Knowledge
Frameworks: LangGraph, CrewAI, or Haystack.
Databases: Vector DBs (Pinecone, Weaviate, Qdrant) and their indexing strategies (HNSW, IVFFlat).
Observability: LangSmith, Honeycomb, or Arize Phoenix.
Backend: Python (Expert), FastAPI, Pydantic v2, and asynchronous programming.
This is not just a teaching role. It is a chance to help scale the most popular AI cohort and define how production grade AI engineering is taught.
Let’s build the most popular AI cohort together.
How to Apply
Send your resume and a short note on why you’re excited about this role to jobs@bytebytego.com


Thanks. But note that the post on "What Happens When You Enter Google.com" is several years out-of-date. It describes the classic TCP-TLS protocol, but since about 2020, Chromium-based browsers (and now all the big ones) default to HTTP/3 aka QUIC and only back-off to TCP if there's a problem. HTTP/3 is much faster to start up, doesn't hit delays so often, deals better with switching between Wi-Fi and mobile, etc.
The video of AI Agents is very good. clearly explained the process.