EP85: Like LeetCode, but for improving debugging skills
This week’s system design refresher:
SadServers, like LeetCode, but for improving debugging skills
How Big Tech Ships Code to Production (Youtube video)
Top 9 HTTP Request Methods
The Software Engineer's Guidebook
Log Parsing Cheat Sheet
How to become a technical founder VCs love investing in (Sponsored)
Engineers like you make some of the best startup founders but struggle when it comes to raising money.
To help future founders like you, I’ve created a guide to becoming that sought after technical founder that VCs LOVE to invest in.
It includes:
📋 8 step-by-step project plans (no thinking, just doing)
👨🏻 15 video explainers
✍️ Copywriting templates
The retail price is $287 but I’m offering it for FREE to ByteByteGo readers who use the code ‘byte287’
(btw - who am I?) My name’s Jason Yeh. I studied compsci before working in Venture Capital and raising millions as a founder. I’ve helped founders around the world raise over $250MM (@jayyeh and my newsletter, and admnt.com).
SadServers, like LeetCode, but for improving debugging skills
One of the best ways to learn is to debug real problems. I recently discovered an interesting site built by Fernando Duran. It's similar to LeetCode, but focuses on improving developers debugging skills. I hope you find it useful. You can check it out here.
How Big Tech Ships Code to Production
Top 9 HTTP Request Methods
GET, POST, PUT... Common HTTP “verbs” in one figure.
HTTP GET
This retrieves a resource from the server. It is idempotent. Multiple identical requests return the same result.HTTP PUT
This updates or Creates a resource. It is idempotent. Multiple identical requests will update the same resource.HTTP POST
This is used to create new resources. It is not idempotent, making two identical POST will duplicate the resource creation.HTTP DELETE
This is used to delete a resource. It is idempotent. Multiple identical requests will delete the same resource.HTTP PATCH
The PATCH method applies partial modifications to a resource.HTTP HEAD
The HEAD method asks for a response identical to a GET request but without the response body.HTTP CONNECT
The CONNECT method establishes a tunnel to the server identified by the target resource.HTTP OPTIONS
This describes the communication options for the target resource.HTTP TRACE
This performs a message loop-back test along the path to the target resource.
Over to you: What other HTTP verbs have you used?
Latest articles
If you’re not a paid subscriber, here’s what you missed this month.
The 6 Most Impactful Ways Redis is Used in Production Systems
The Tech Promotion Algorithm: A Structured Guide to Moving Up
To receive all the full articles and support ByteByteGo, consider subscribing:
The Software Engineer's Guidebook
It is great to be one of the first readers of this amazing book: The Software Engineer's Guidebook.
Gergely Orosz spent four years writing it. The book provides a roadmap for a typical software engineering career, starting as a fresh-faced software developer and progressing to a senior/lead role model, all the way up to the staff/principal/distinguished level.
What's inside?
Part 1: Developer Career Fundamentals
1. Career paths
2. Owning your career
3. Performance reviews
4. Promotions
5. Thriving in different environments
6. Switching jobs
Part 2: The Competent Software Developer
7. Getting things done
8. Coding
9. Software development
10. Tools of the productive engineer
Part 3: The Well-Rounded Senior Engineer
11. Getting things done
12. Collaboration and teamwork
13. Software engineering
14. Testing
15. Software architecture
Part 4: The Pragmatic Tech Lead
16. Project management
17. Shipping in production
18. Stakeholder management
19. Team structure
20. Team dynamics
Part 5: Role-Model Staff and Principal Engineers
21. Understanding the business
22. Collaboration
23. Software engineering
24. Reliable software engineering
25. Software architecture
If you are interested, you can check out the book here.
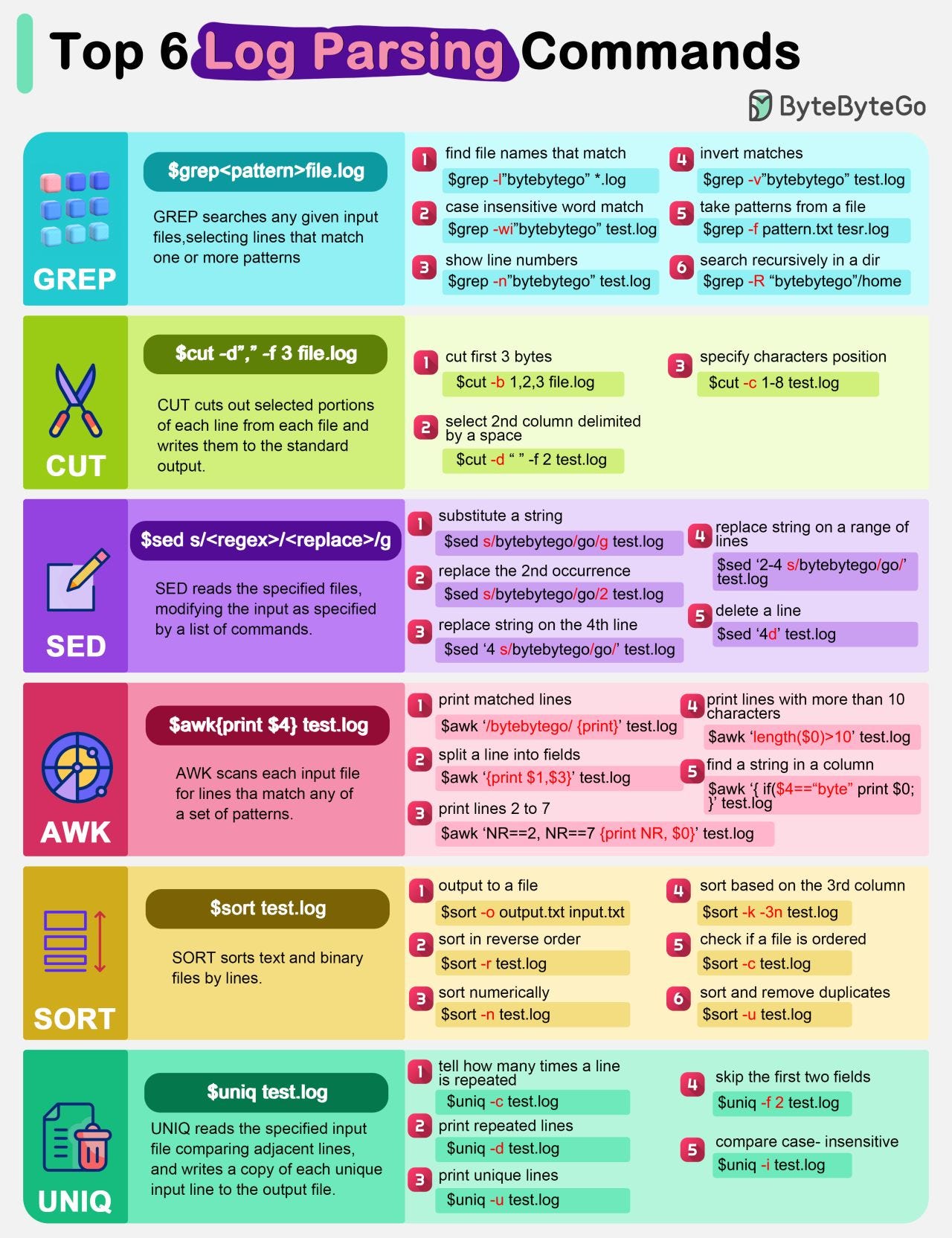
Log Parsing Cheat Sheet
The diagram below lists the top 6 log parsing commands.
GREP
GREP searches any given input files, selecting lines that match one or more patterns.CUT
CUT cuts out selected portions of each line from each file and writes them to the standard output.SED
SED reads the specified files, modifying the input as specified by a list of commands.AWK
AWK scans each input file for lines that match any of a set of patterns.SORT
SORT sorts text and binary files by lines.UNIQ
UNIQ reads the specified input file comparing adjacent lines and writes a copy of each unique input line to the output file.
These commands are often used in combination to quickly find useful information from the log files. For example, the below commands list the timestamps (column 2) when there is an exception happening for xxService.
grep “xxService” service.log | grep “Exception” | cut -d” “ -f 2
Over to you: What other commands do you use when you parse logs?