EP97: 10 Good Coding Principles to Improve Code Quality
This week’s system design refresher:
How Disney Hotstar Captures One Billion Emojis (Youtube video)
10 Good Coding Principles to improve code quality
Top Network Security Cheatsheet
How does a VPN work?
What is a cookie?
ScyllaDB Summit | Feb 14-15 | Free + Virtual (Sponsored)
Join thousands of your peers for an unprecedented opportunity to learn from experts at Discord, Disney, Expedia, Zee, ShareChat, Paramount & more – for free, from anywhere.
30+ talks on NoSQL, Kafka, Kubernetes, and AI/ML system architectures and best practices, plus interactive hands-on training.
Discord Keynote: Everything's great until the database is down. Bo Ingram, staff engineer at Discord and author of ScyllaDB in Action, shares lessons from their database outage so that you can learn from their mistakes.
Book Bonus: Register this week to get Database Performance at Scale and an early access copy of ScyllaDB in Action.
How Disney Hotstar Captures One Billion Emojis!
10 Good Coding Principles to improve code quality
Software development requires good system designs and coding standards. We list 10 good coding principles in the diagram below.
01 Follow Code Specifications
When we write code, it is important to follow the industry's well-established norms, like “PEP 8”, “Google Java Style”, adhering to a set of agreed-upon code specifications ensures that the quality of the code is consistent and readable.02 Documentation and Comments
Good code should be clearly documented and commented to explain complex logic and decisions, and comments should explain why a certain approach was taken (“Why”) rather than what exactly is being done (“What”). Documentation and comments should be clear, concise, and continuously updated.03 Robustness
Good code should be able to handle a variety of unexpected situations and inputs without crashing or producing unpredictable results. Most common approach is to catch and handle exceptions.04 Follow the SOLID principle
“Single Responsibility”, “Open/Closed”, “Liskov Substitution”, “Interface Segregation”, and “Dependency Inversion” - these five principles (SOLID for short) are the cornerstones of writing code that scales and is easy to maintain.05 Make Testing Easy
Testability of software is particularly important. Good code should be easy to test, both by trying to reduce the complexity of each component, and by supporting automated testing to ensure that it behaves as expected.06 Abstraction
Abstraction requires us to extract the core logic and hide the complexity, thus making the code more flexible and generic. Good code should have a moderate level of abstraction, neither over-designed nor neglecting long-term expandability and maintainability.07 Utilize Design Patterns, but don't over-design
Design patterns can help us solve some common problems. However, every pattern has its applicable scenarios. Overusing or misusing design patterns may make your code more complex and difficult to understand.08 Reduce Global Dependencies
We can get bogged down in dependencies and confusing state management if we use global variables and instances. Good code should rely on localized state and parameter passing. Functions should be side-effect free.09 Continuous Refactoring
Good code is maintainable and extensible. Continuous refactoring reduces technical debt by identifying and fixing problems as early as possible.10 Security is a Top Priority
Good code should avoid common security vulnerabilities.
Over to you: which one do you prefer, and with which one do you disagree?
Latest articles
If you’re not a paid subscriber, here’s what you missed this month.
To receive all the full articles and support ByteByteGo, consider subscribing:
Top Network Security Cheatsheet
The diagram below shows some possible network attacks in 7 OSI model layers.
Application Layer
- Pushing
- Malware injection
- DDos attacksPresentation Layer
- Encoding/decoding vulnerabilities
- Format string attacks
- Malicious code injectionSession Layer
- Session hijacking
- Session fixation attacks
- Brute force attacksTransport Layer
- Man-in-the-middle attacks
- SYN/ACK floodNetwork Layer
- IP spoofing
- Route table manipulation
- DDos attacksData Link Layer
- MAC address spoofing
- ARP spoofing
- VLAN hoppingPhysical Layer
- Wiretapping
- Physical tampering
- Electromagnetic interference
Over to you - What did we miss?
How does a VPN work?
This diagram below shows how we access the internet with and without VPNs.
A VPN, or Virtual Private Network, is a technology that creates a secure, encrypted connection over a less secure network, such as the public internet. The primary purpose of a VPN is to provide privacy and security to data and communications.
A VPN acts as a tunnel through which the encrypted data goes from one location to another. Any external party cannot see the data transferring.
A VPN works in 4 steps:
Step 1 - Establish a secure tunnel between our device and the VPN server.
Step 2 - Encrypt the data transmitted.
Step 3 - Mask our IP address, so it appears as if our internet activity is coming from the VPN server.
Step 4 - Our internet traffic is routed through the VPN server.
Advantages of a VPN:
Privacy
Anonymity
Security
Encryption
Masking the original IP address
Disadvantages of a VPN:
VPN blocking
Slow down connections
Trust in VPN provider
What is a cookie?
Imagine Bob goes to a coffee shop for the first time, orders a medium-sized espresso with two sugars. The cashier records Bob’s identity and preferences on a card and hands it over to Bob with a cup of coffee.
The next time Bob goes to the cafe, he shows the cashier the preference card. The cashier immediately knows who the customer is and what kind of coffee he likes.
A cookie acts as the preference card. When we log in to a website, the server issues a cookie to us with a small amount of data. The cookie is stored on the client side, so the next time we send a request to the server with the cookie, the server knows our identity and preferences immediately without looking into the database.







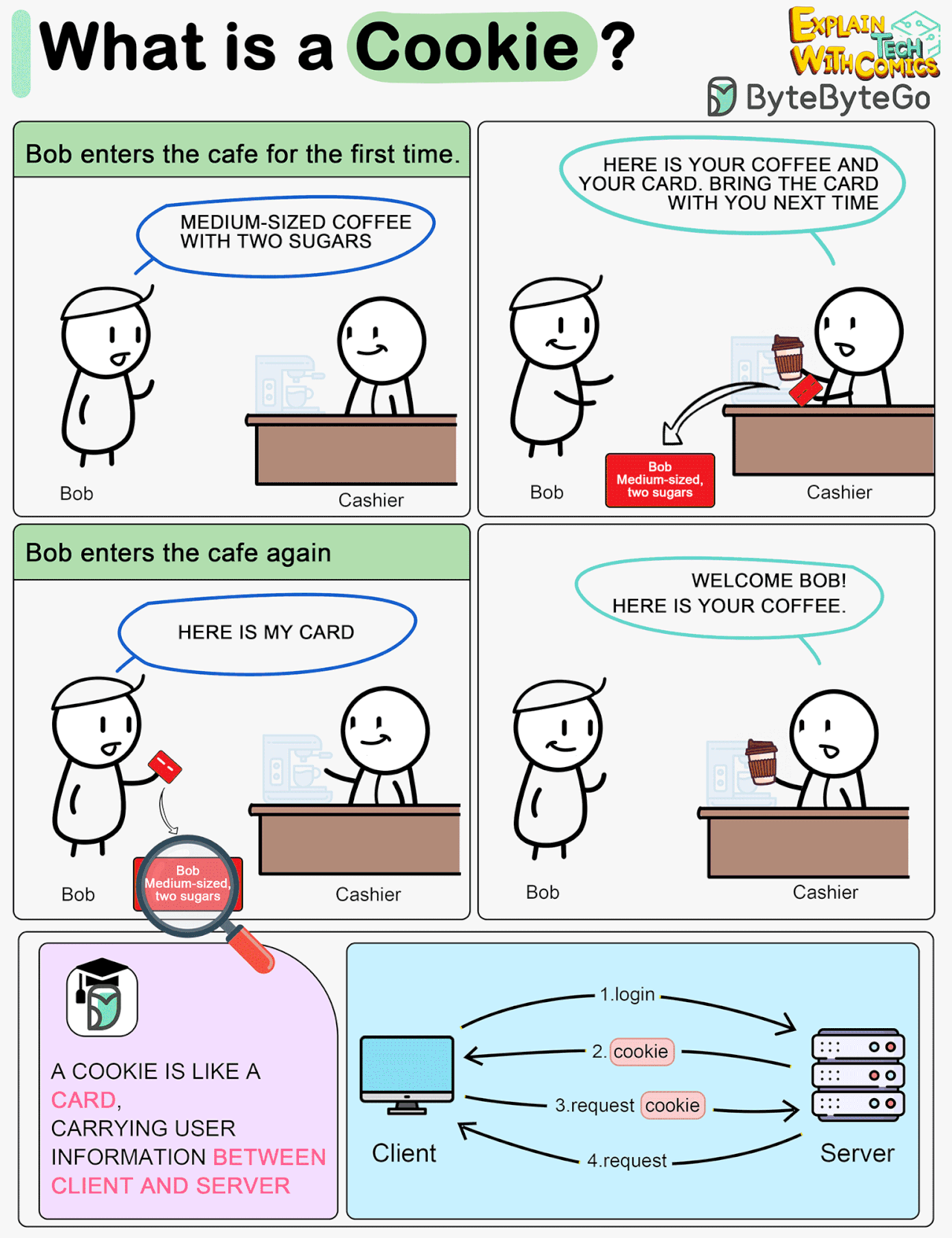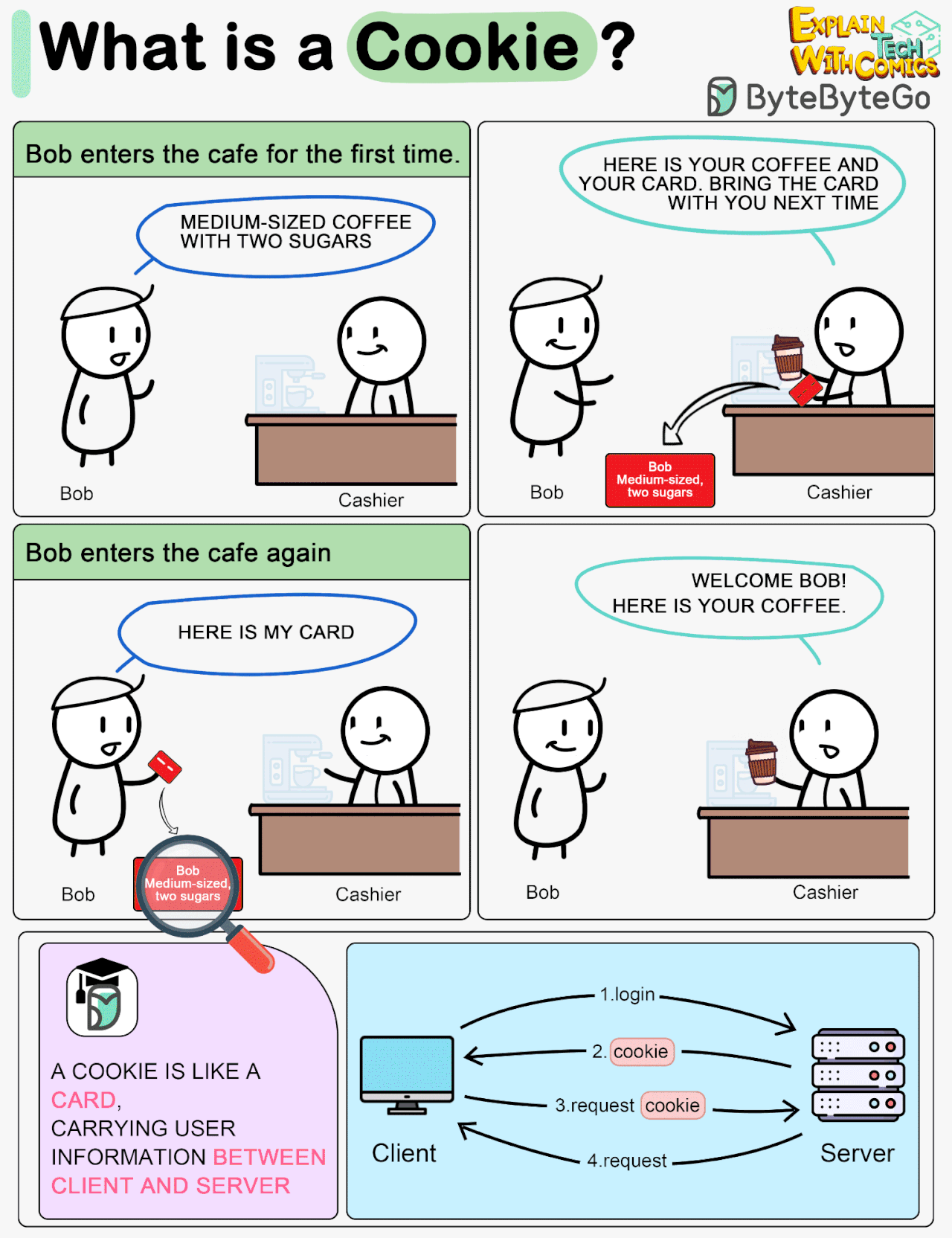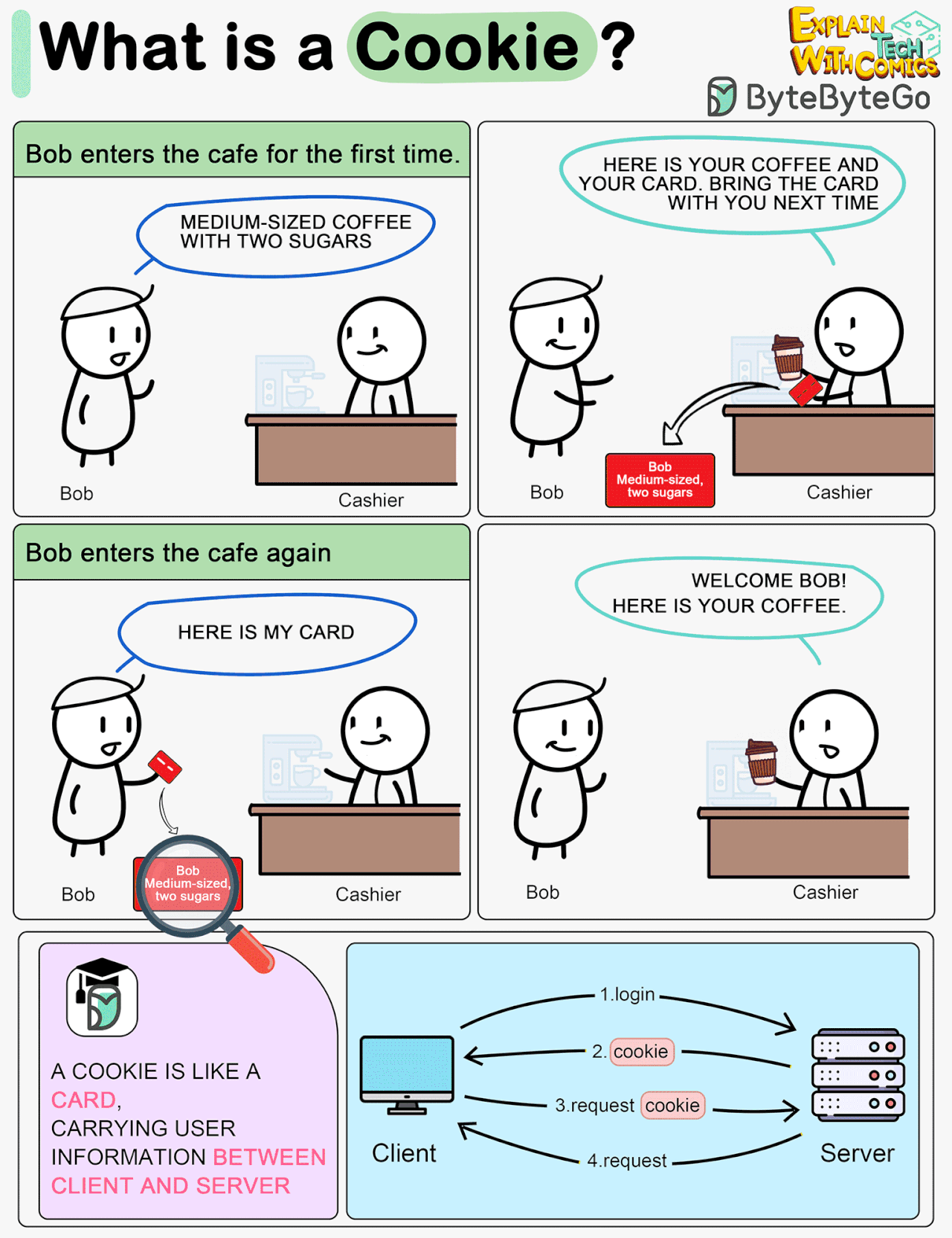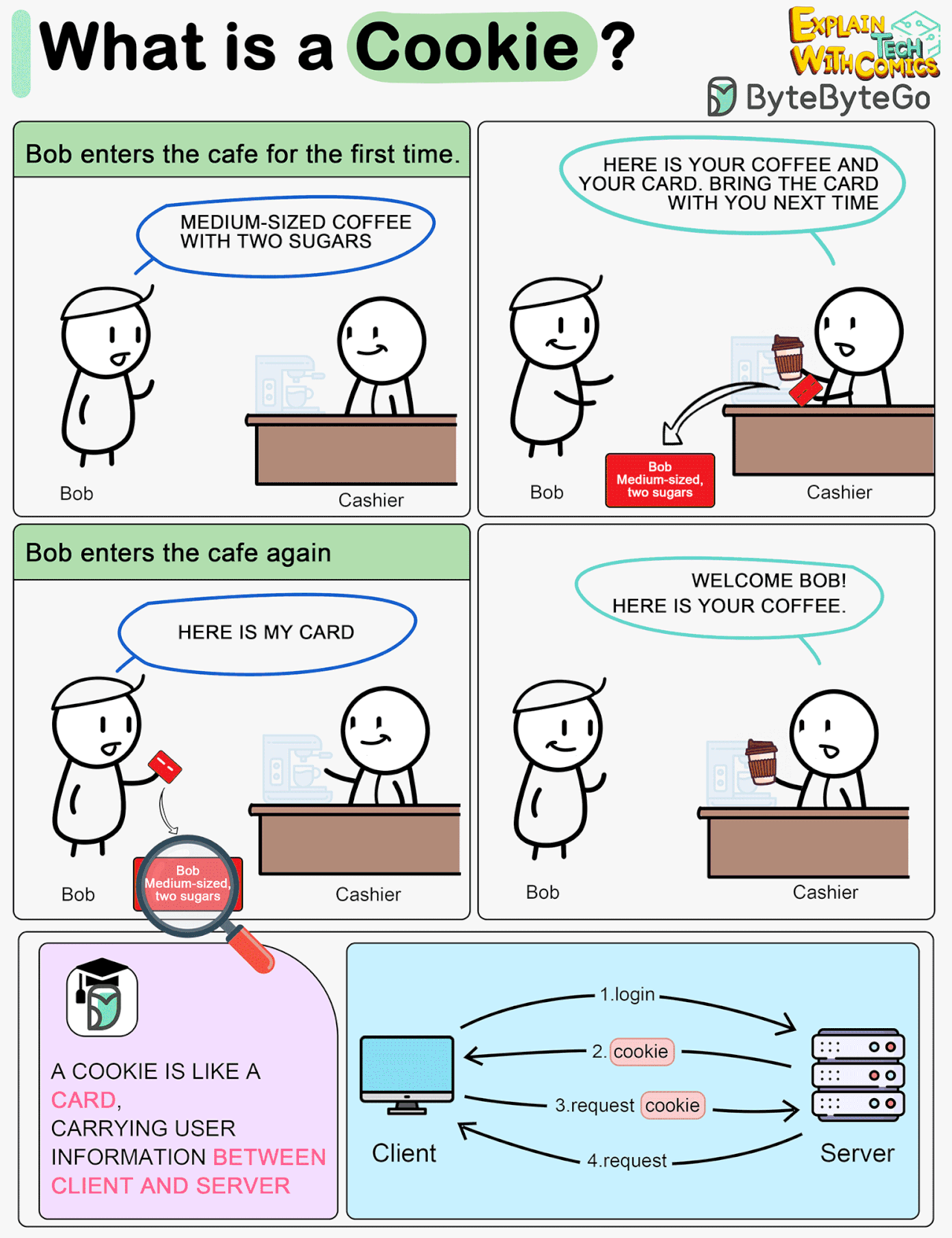
In the Cookie diagram I agree their original purpose was benign and they can be helpful, but you're missing the nasty side effects where Bob gets 472 other store cards in the same transaction, and all those store cards report where Bob has spent money to their own coffee shops so those shops can advertise the right coffee, shoes and political party to Bob.
In Cookie diagram, I guess flow 4 should be a Response