Payment security
A few weeks ago, I posted the high-level design for the payment system. Today, I’ll continue the discussion and focus on payment security.
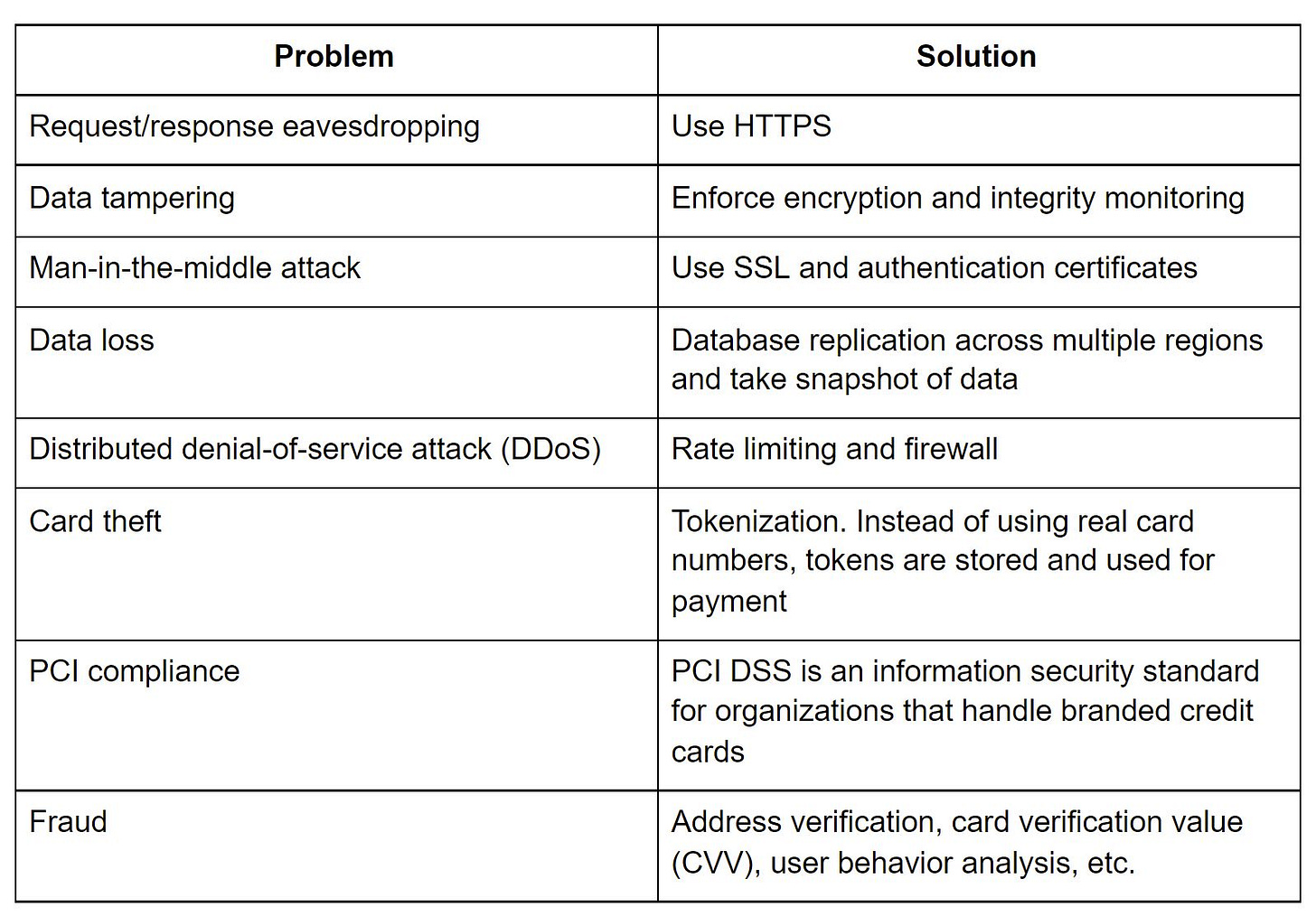
The table below summarizes techniques that are commonly used in payment security.
If you enjoyed this post, you might like our system design interview books as well.
SDI-vol1: https://amzn.to/3tK0qQn
SDI-vol2: https://amzn.to/37ZisW9