EP113: AWS Services Cheat Sheet
This week’s system design refresher:
Do You Know How Mobile Apps Are Released? (Youtube video)
AWS Services Cheat Sheet
A cheat sheet for API designs
Azure Services Cheat Sheet
How do computer programs run?
SPONSOR US
Collaborating on APIs is Easier With Postman (Sponsored)
Whether you’re a team of four or 40,000, development teams need to collaborate on APIs. API Collaboration improves developer productivity by empowering both API producers and consumers to share, discover, and reuse high-quality API assets.
Postman revolutionizes the experience of collaborative API development with Collections and Workspaces. Used together, they enable API design, testing, and documentation, providing a shared canvas for collaborating on API assets.
Learn how Postman is giving teams of all sizes and functions the ability to rapidly iterate on API development, elevate the quality of their APIs, and extend their API workflows for large-scale initiatives.
Do You Know How Mobile Apps Are Released?
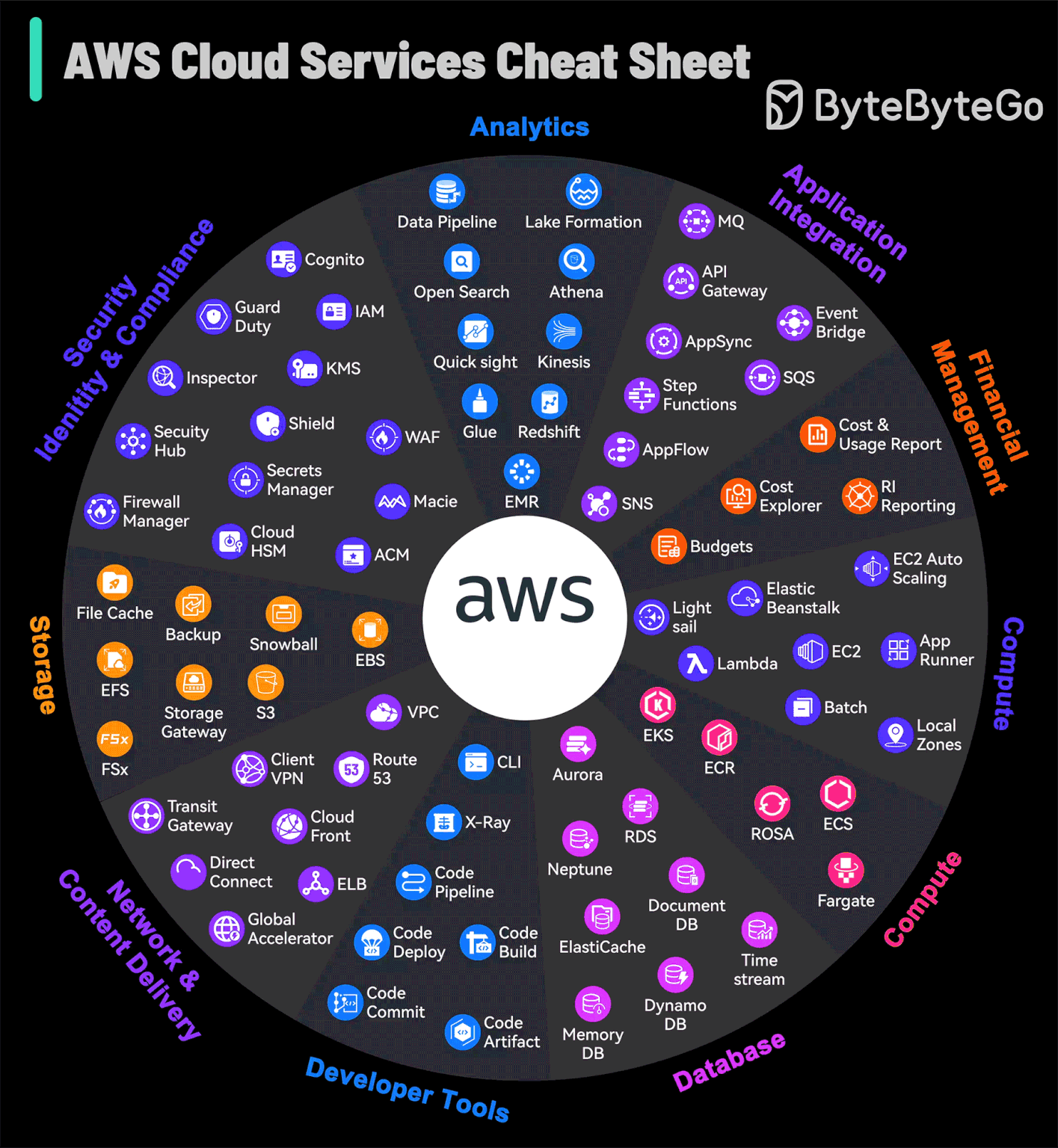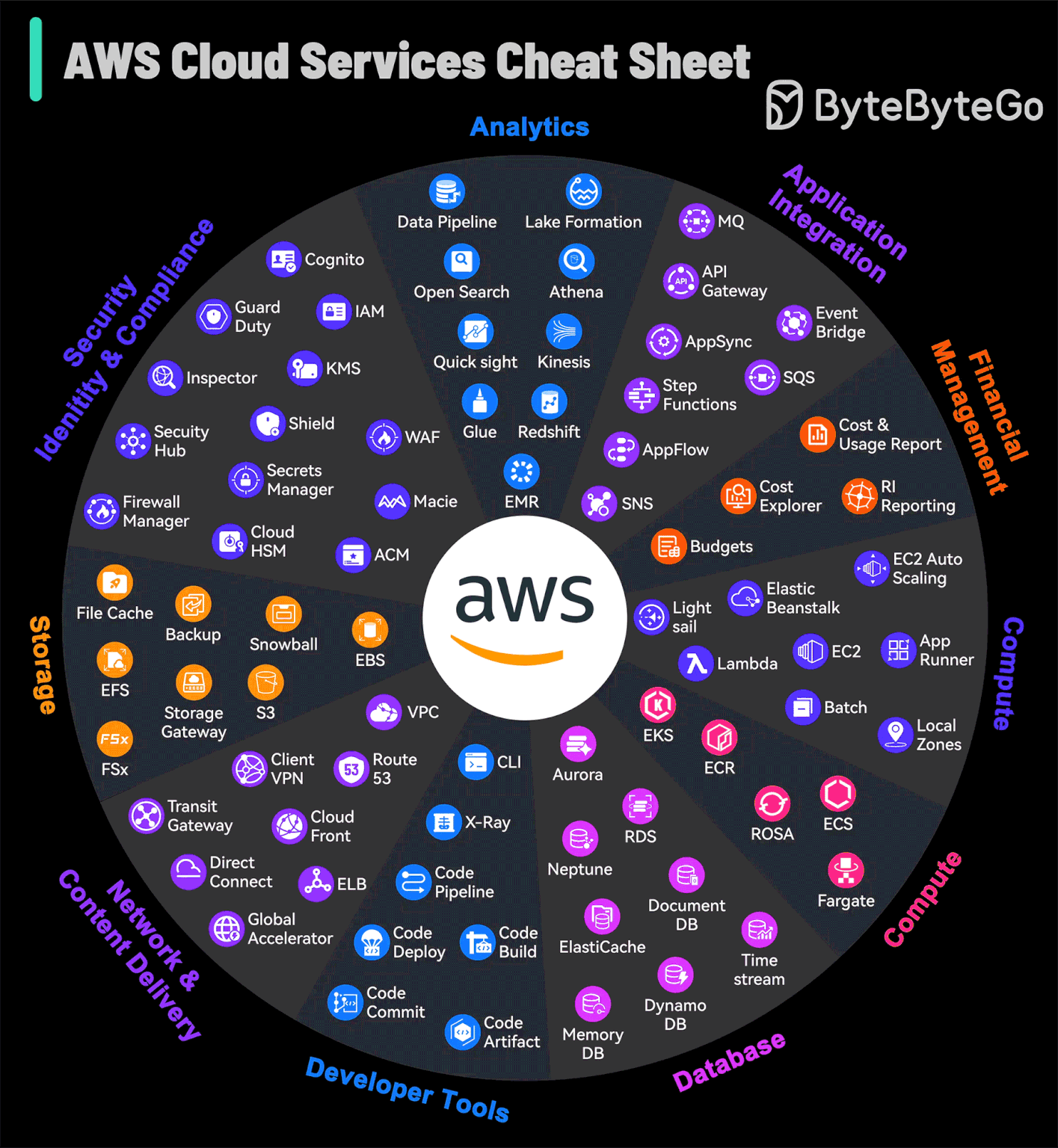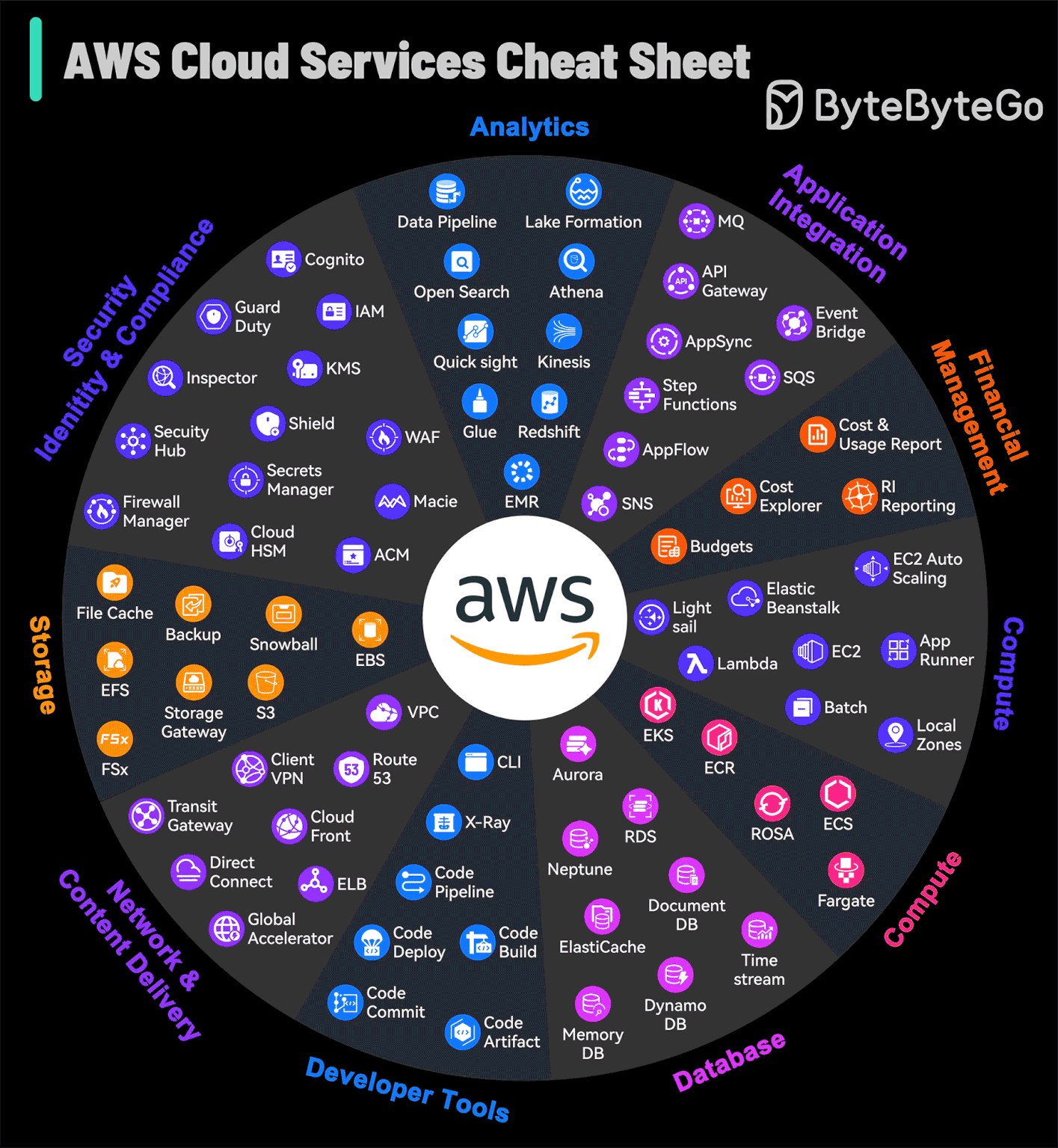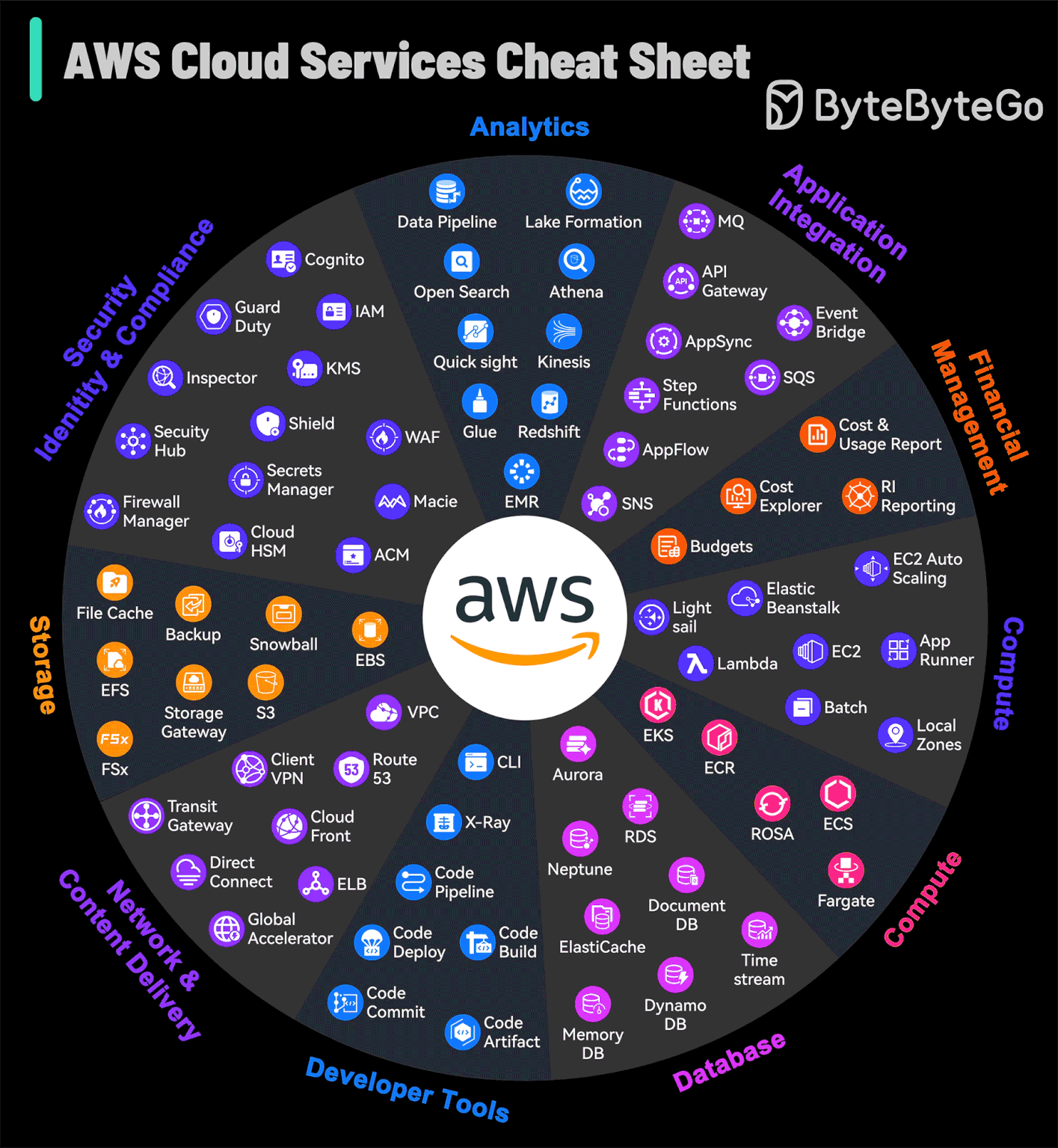
AWS Services Cheat Sheet
AWS grew from an in-house project to the market leader in cloud services, offering so many different services that even experts can find it a lot to take in.
The platform not only caters to foundational cloud needs but also stays at the forefront of emerging technologies such as machine learning and IoT, establishing itself as a bedrock for cutting-edge innovation. AWS continuously refines its array of services, ensuring advanced capabilities for security, scalability, and operational efficiency are available.
For those navigating the complex array of options, this AWS Services Guide is a helpful visual aid.
It simplifies the exploration of AWS's expansive landscape, making it accessible for users to identify and leverage the right tools for their cloud-based endeavors.
Over to you: What improvements would you like to see in AWS services based on your usage?
Latest articles
If you’re not a paid subscriber, here’s what you missed.
To receive all the full articles and support ByteByteGo, consider subscribing:
A cheat sheet for API designs
APIs expose business logic and data to external systems, so designing them securely and efficiently is important.
API key generation
We normally generate one unique app ID for each client and generate different pairs of public key (access key) and private key (secret key) to cater to different authorizations. For example, we can generate one pair of keys for read-only access and another pair for read-write access.Signature generation
Signatures are used to verify the authenticity and integrity of API requests. They are generated using the secret key and typically involve the following steps:
- Collect parameters
- Create a string to sign
- Hash the string: Use a cryptographic hash function, like HMAC (Hash-based Message Authentication Code) in combination with SHA-256, to hash the string using the secret key.Send the requests
When designing an API, deciding what should be included in HTTP request parameters is crucial. Include the following in the request parameters:
- Authentication Credentials
- Timestamp: To prevent replay attacks.
- Request-specific Data: Necessary to process the request, such as user IDs, transaction details, or search queries.
- Nonces: Randomly generated strings included in each request to ensure that each request is unique and to prevent replay attacks.Security guidelines
To safeguard APIs against common vulnerabilities and threats, adhere to these security guidelines.
Azure Services Cheat Sheet
Launching in 2010, Microsoft Azure has quickly grown to hold the No. 2 position in market share by evolving from basic offerings to a comprehensive, flexible cloud ecosystem.
Today, Azure not only supports traditional cloud applications but also caters to emerging technologies such as AI, IoT, and blockchain, making it a crucial platform for innovation and development.
As it evolves, Azure continues to enhance its capabilities to provide advanced solutions for security, scalability, and efficiency, meeting the demands of modern enterprises and startups alike. This expansion allows organizations to adapt and thrive in a rapidly changing digital landscape.
The attached illustration can serve as both an introduction and a quick reference for anyone aiming to understand Azure.
Over to you: How does your experience with Azure compare to that with AWS?
Over to you: Does the card network charge the same interchange fee for big merchants as for small merchants?
How do computer programs run?
The diagram shows the steps.
User interaction and command initiation
By double-clicking a program, a user is instructing the operating system to launch an application via the graphical user interface.Program Preloading
Once the execution request has been initiated, the operating system first retrieves the program's executable file.
The operating system locates this file through the file system and loads it into memory in preparation for execution.Dependency resolution and loading
Most modern applications rely on a number of shared libraries, such as dynamic link libraries (DLLs).Allocating memory space
The operating system is responsible for allocating space in memory.
Initializing the Runtime Environment
After allocating memory, the operating system and execution environment (e.g., Java's JVM or the .NET Framework) will initialize various resources needed to run the program.System Calls and Resource Management
The entry point of a program (usually a function named `main`) is called to begin execution of the code written by the programmer.Von Neumann Architecture
In the Von Neumann architecture, the CPU executes instructions stored in memory.Program termination
Eventually, when the program has completed its task, or the user actively terminates the application, the program will begin a cleanup phase. This includes closing open file descriptors, freeing up network resources, and returning memory to the system.
SPONSOR US
Get your product in front of more than 500,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com






Hello blogger, what software are these animations made with? I'm looking forward to your answer, thank you.
Great diagram, but missing a few key services that show up on my bill
API Gateway
Glacier
Simple Email Service
CloudWatch
CloudTrail
IoT (No longer Used)
WorkSpaces