EP109: Top 6 Tools to Turn Code into Beautiful Diagrams
This week’s system design refresher:
Top 9 Must-Read Blogs for Engineers
Top 6 Tools to Turn Code into Beautiful Diagrams
What is DevSecOps?
Top 5 Trade-offs in System Designs
Top 8 Cache Eviction Strategies
SPONSOR US
POST/CON 24 | April 30 - May 1 (Sold Out)(Sponsored)
POST/CON 24 is sold out, but you can still join the waitlist here for a complimentary ticket and be the first to know if tickets become available!
You’ll hear keynote speakers, see demos of new Postman features, watch an incredible panel discussion on AI—and so much more. If you can’t join us in person, mark your calendar and save this link to check out the livestream of it all on May 1, from 9 am - 11:30 am PDT.
Top 9 Must-Read Blogs for Engineers
Top 6 Tools to Turn Code into Beautiful Diagrams
Diagrams
Go Diagrams
Mermaid
PlantUML
ASCII diagrams
Markmap
Over to you: Did we miss anything? What's your favorite?
Latest articles
If you’re not a paid subscriber, here’s what you missed.
To receive all the full articles and support ByteByteGo, consider subscribing:
What is DevSecOps?
DevSecOps emerged as a natural evolution of DevOps practices with a focus on integrating security into the software development and deployment process. The term "DevSecOps" represents the convergence of Development (Dev), Security (Sec), and Operations (Ops) practices, emphasizing the importance of security throughout the software development lifecycle.
The diagram below shows the important concepts in DevSecOps.
Automated Security Checks
Continuous Monitoring
CI/CD Automation
Infrastructure as Code (IaC)
Container Security
Secret Management
Threat Modeling
Quality Assurance (QA) Integration
Collaboration and Communication
Vulnerability Management
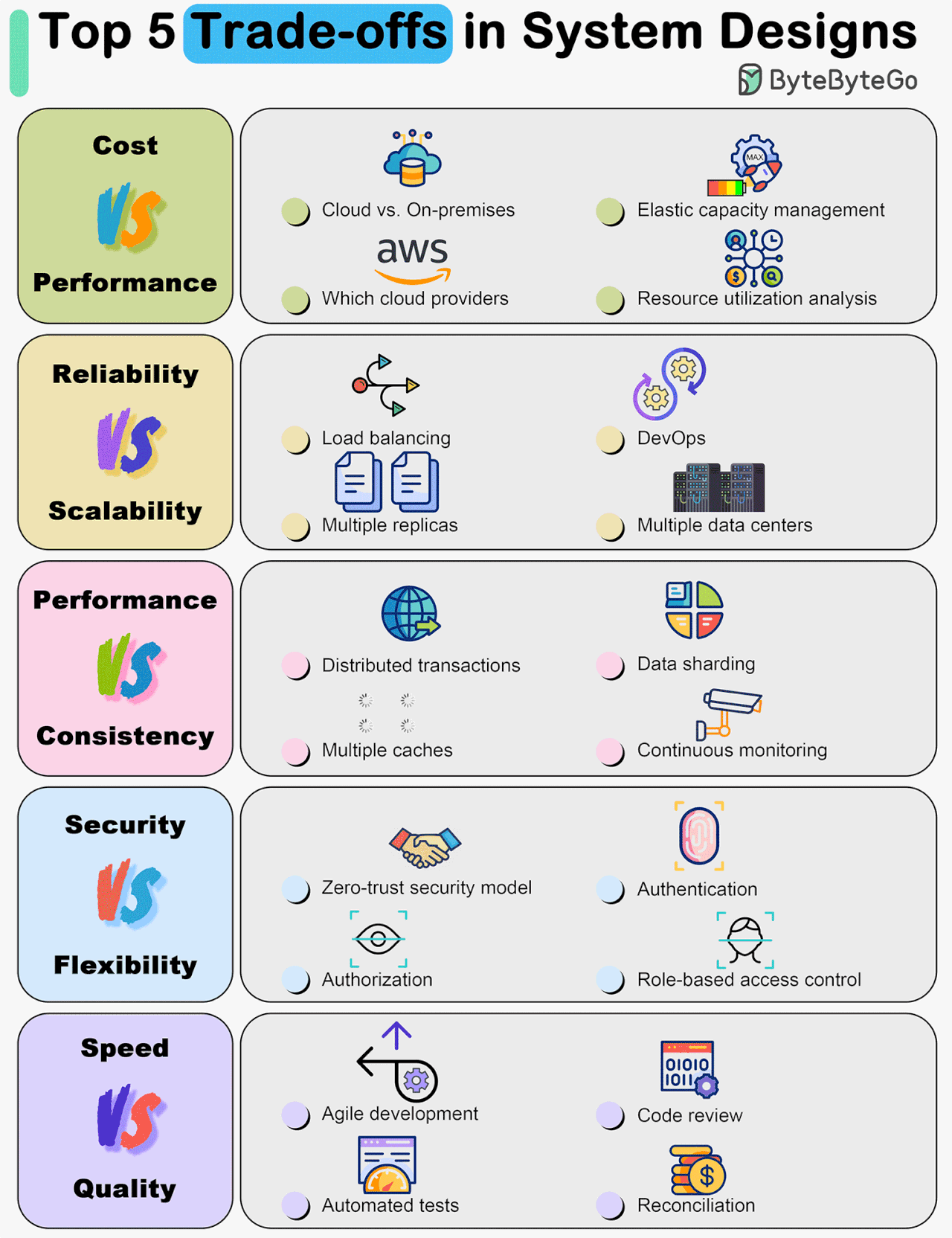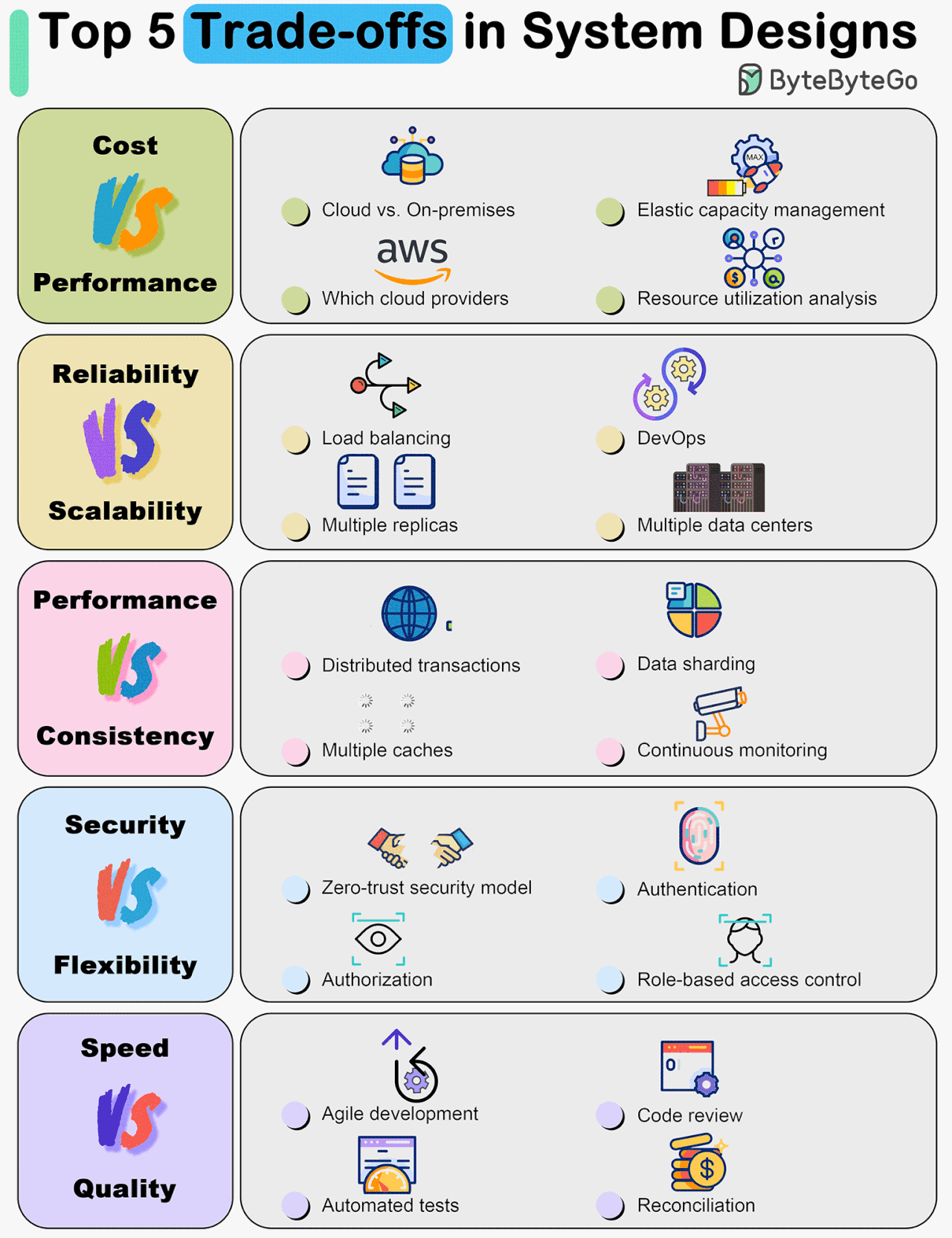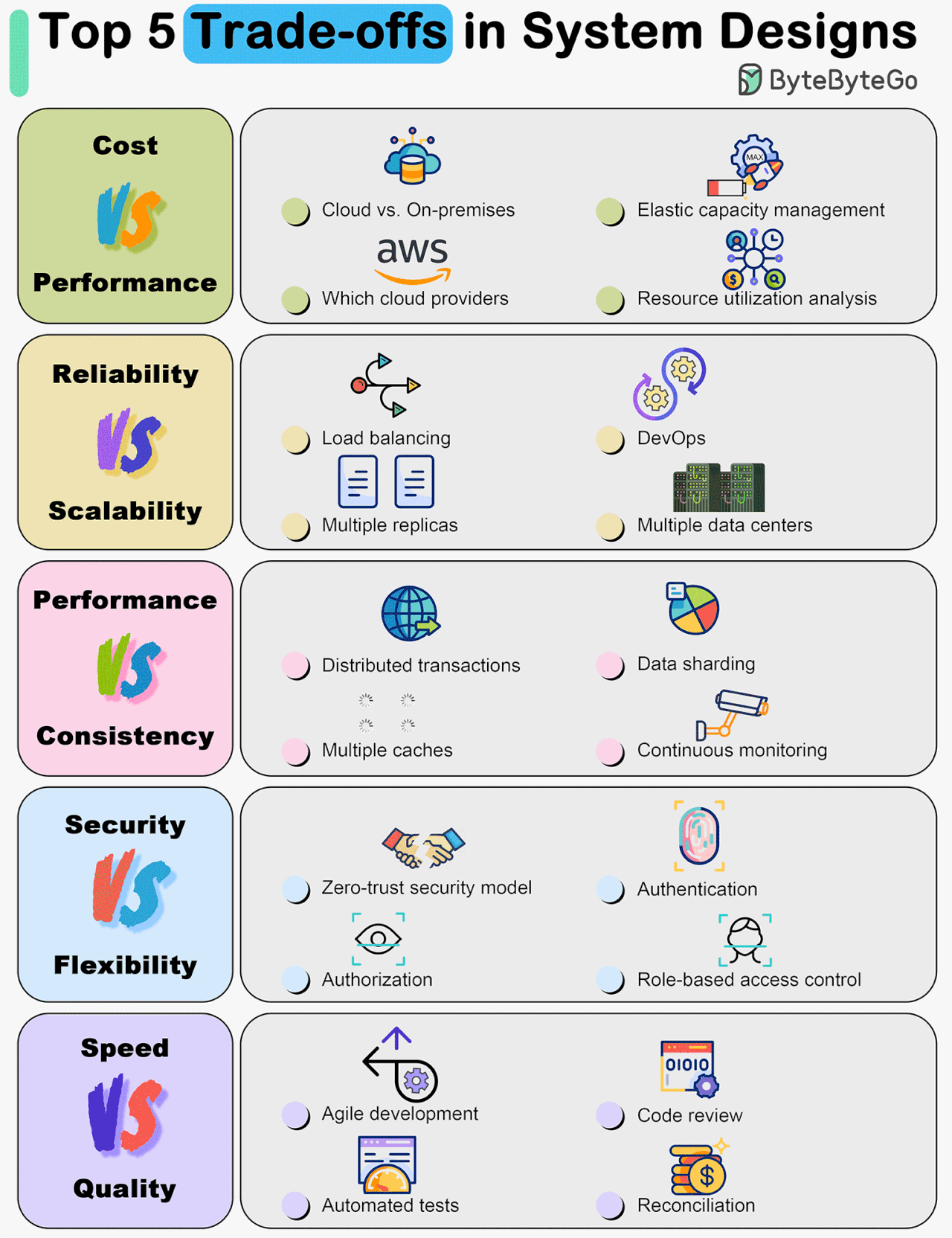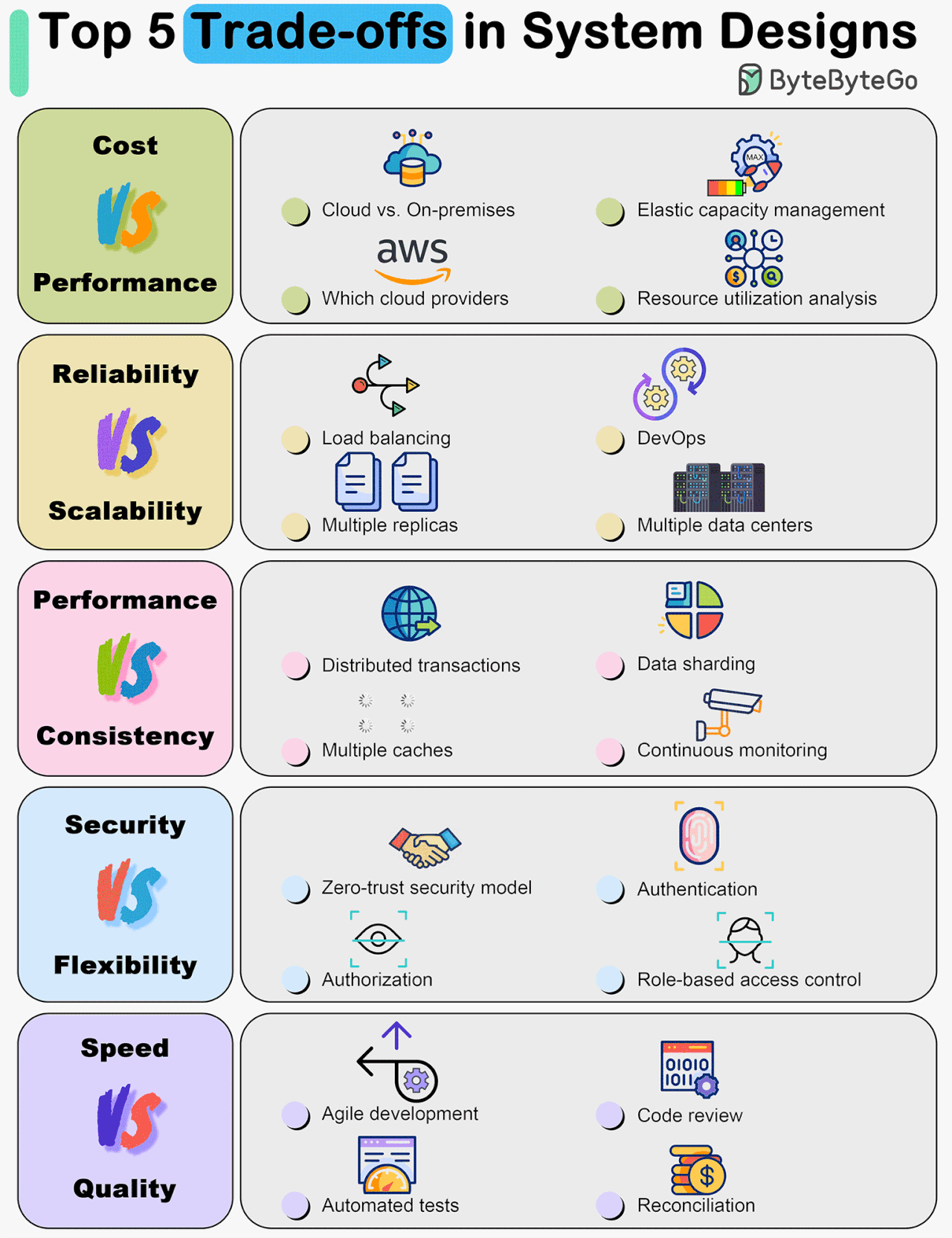
Top 5 Trade-offs in System Designs
Everything is a trade-off.
Everything is a compromise.
There is no right or wrong design.
The diagram below shows some of the most important trade-offs.
Cost vs. Performance
Reliability vs. Scalability
Performance vs. Consistency
Security vs. Flexibility
Development Speed vs. Quality
Over to you: What trade-offs have you made in the past?
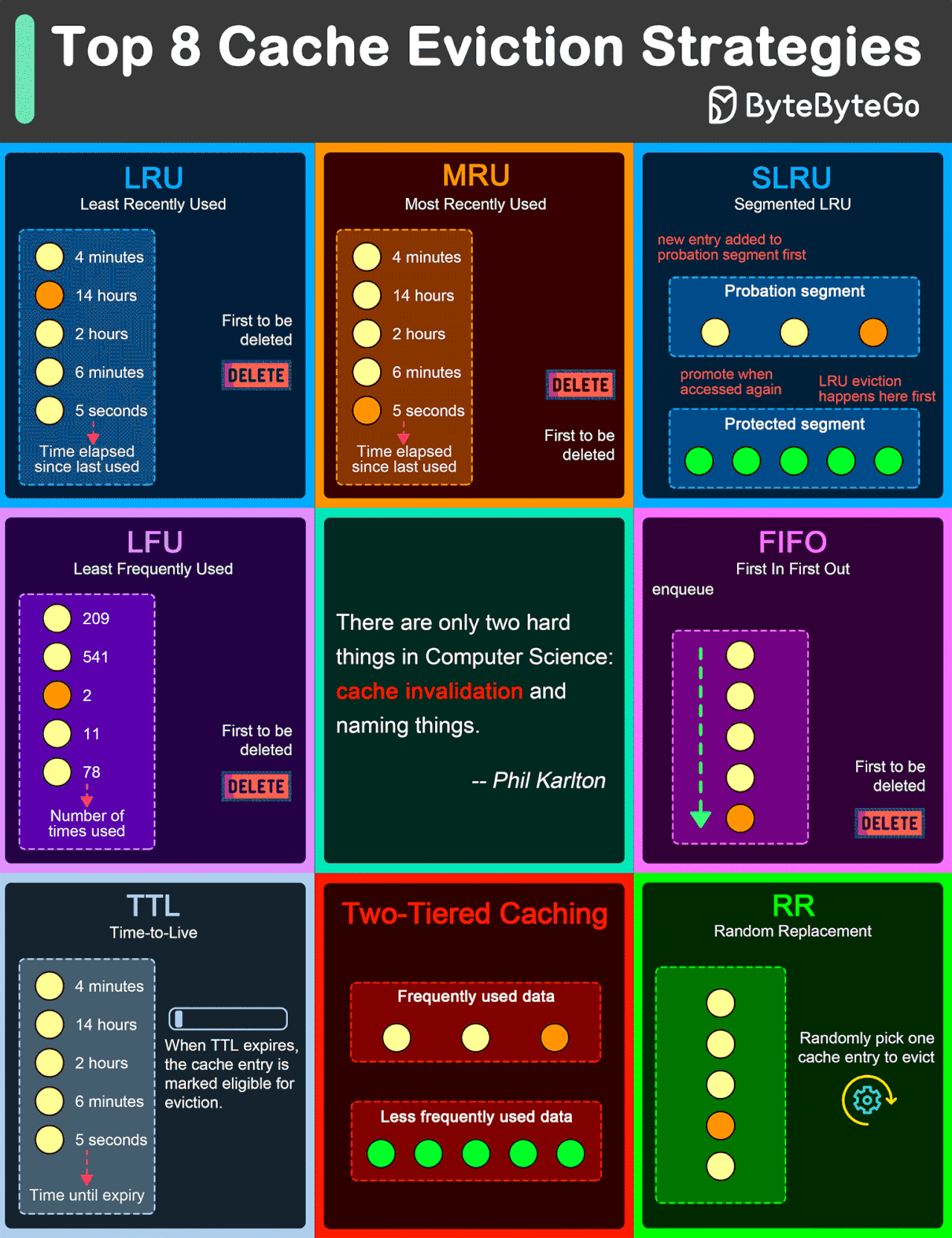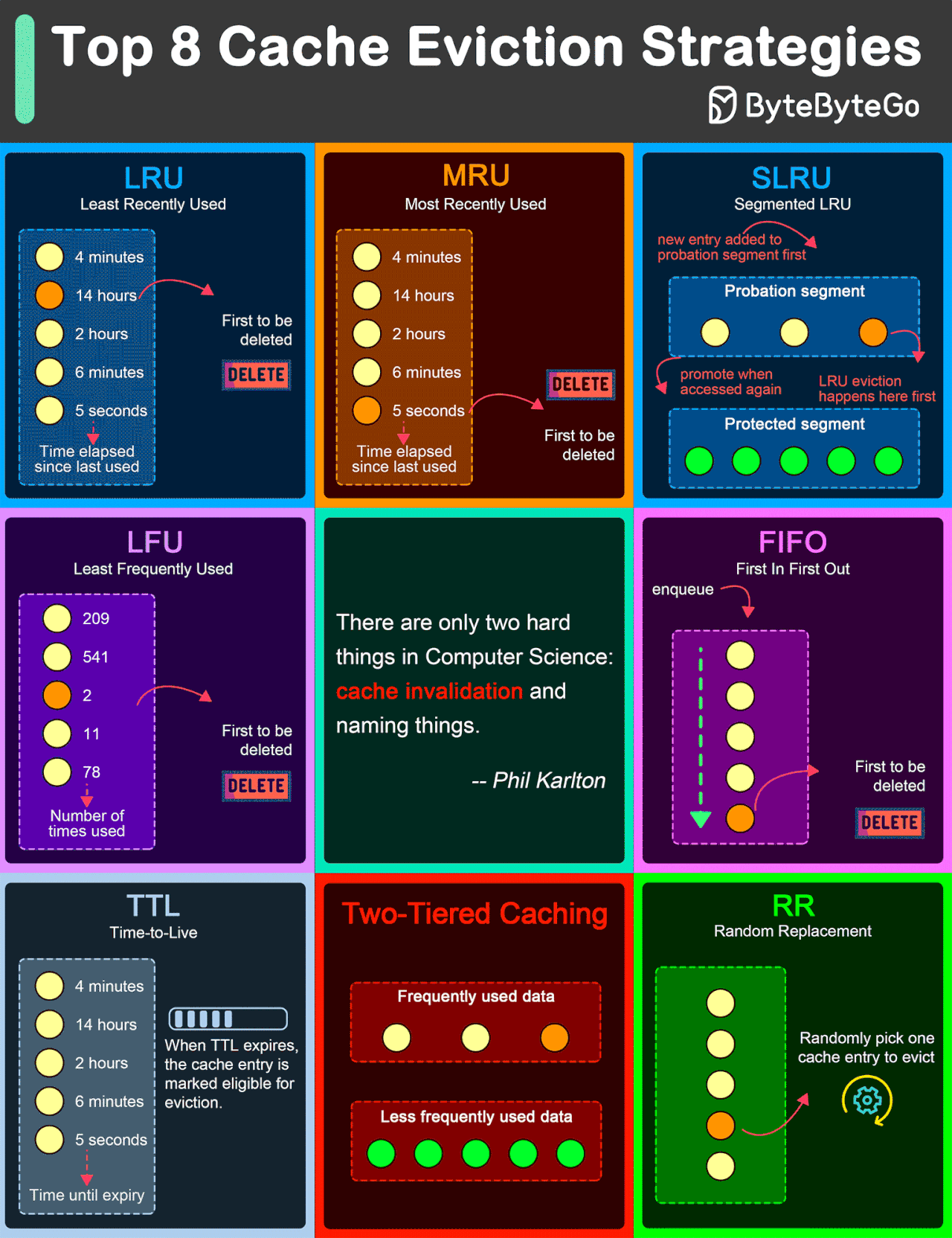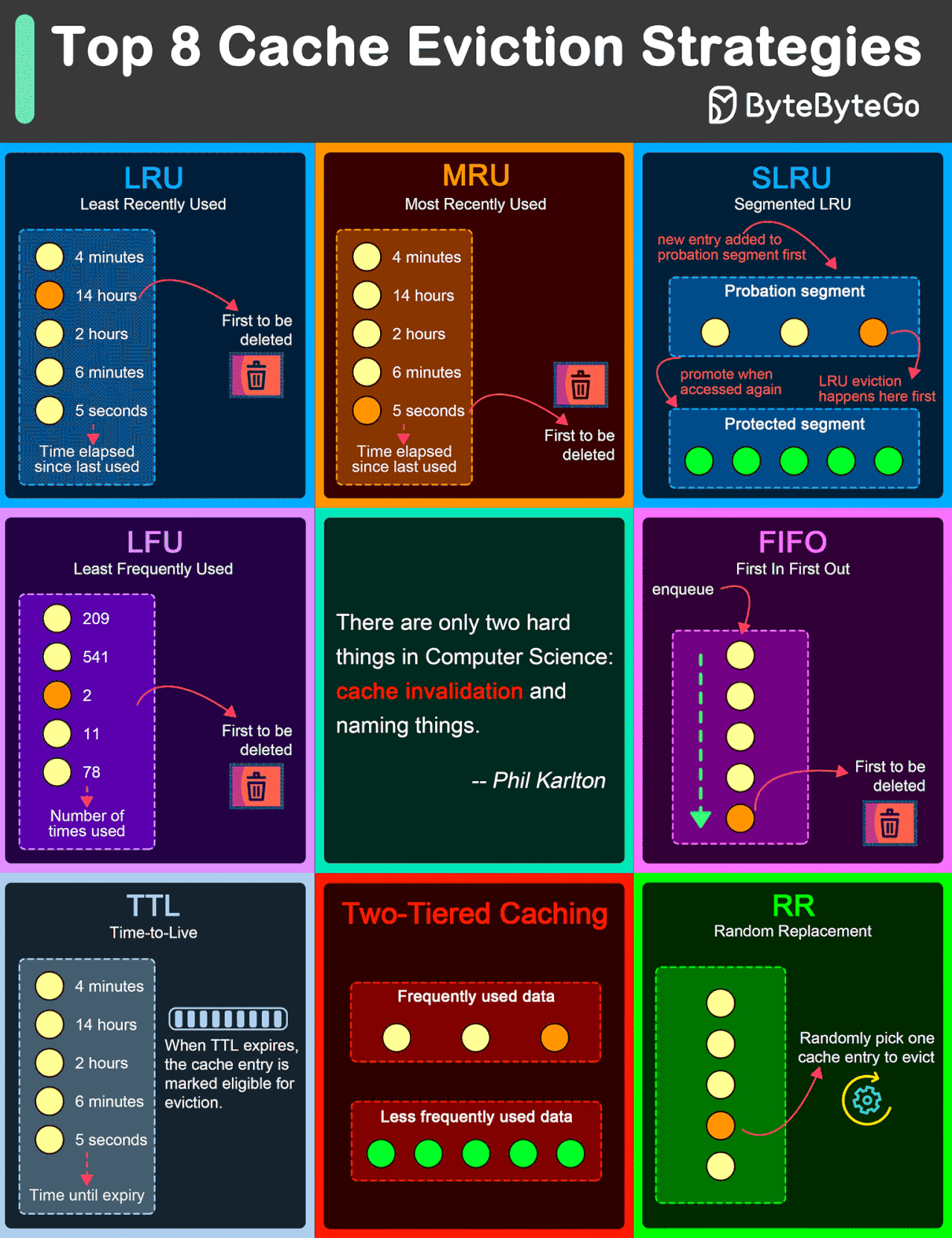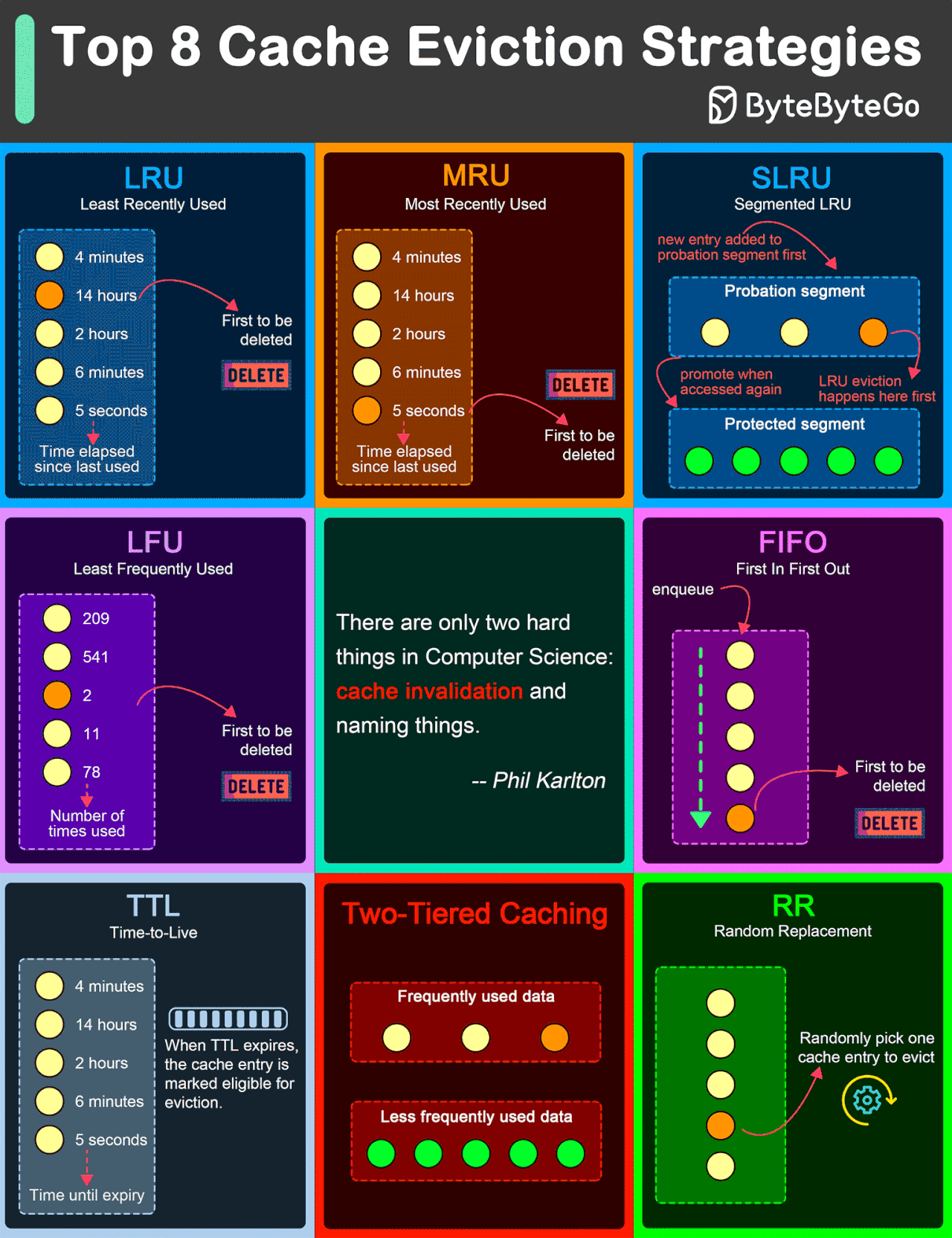
Top 8 Cache Eviction Strategies
LRU (Least Recently Used)
LRU eviction strategy removes the least recently accessed items first. This approach is based on the principle that items accessed recently are more likely to be accessed again in the near future.
MRU (Most Recently Used)
Contrary to LRU, the MRU algorithm removes the most recently used items first. This strategy can be useful in scenarios where the most recently accessed items are less likely to be accessed again soon.
SLRU (Segmented LRU)
SLRU divides the cache into two segments: a probationary segment and a protected segment. New items are initially placed into the probationary segment. If an item in the probationary segment is accessed again, it is promoted to the protected segment.
LFU (Least Frequently Used)
LFU algorithm evicts the items with the lowest access frequency.
FIFO (First In First Out)
FIFO is one of the simplest caching strategies, where the cache behaves in a queue-like manner, evicting the oldest items first, regardless of their access patterns or frequency.
TTL (Time-to-Live)
While not strictly an eviction algorithm, TTL is a strategy where each cache item is given a specific lifespan.
Two-Tiered Caching
In Two-Tiered Caching strategy, we use an in-memory cache for the first layer and a distributed cache for the second layer.
RR (Random Replacement)
Random Replacement algorithm randomly selects a cache item and evicts it to make space for new items. This method is also simple to implement and does not require tracking access patterns or frequencies.
SPONSOR US
Get your product in front of more than 500,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com.






Try https://code2diagram.com/ and select any diagram you need. No setup or installation is required, just use a simple code to generate the best diagram, Additionally, a new AI-powered feature is now available for flowcharts! Just provide a detailed prompt, and the AI will instantly generate both the code and diagram. Simplify your workflow and effortlessly visualize your ideas.