EP117: What makes HTTP2 faster than HTTP1?
This week’s system design refresher:
Kafka vs. RabbitMQ vs. Messaging Middleware vs. Pulsar (Youtube video)
What makes HTTP2 faster than HTTP1?
Top 6 Cases to Apply Idempotency
4 Ways Netflix Uses Caching to Hold User Attention
Log Parsing Cheat Sheet
SPONSOR US
Collaborating on APIs Is Easier with Postman (Sponsored)
API Collaboration improves developer productivity by empowering producers and consumers to share, discover, and reuse high-quality API assets.
Postman revolutionizes the experience of collaborative API development with Postman Collections and Workspaces. Used together, they enable API design, testing, and documentation, while providing a shared canvas for collaborating on API assets.
Learn how companies like Cvent, Visma, Built Technologies, and Amadeus use Postman to collaborate more easily and deliver better APIs faster.
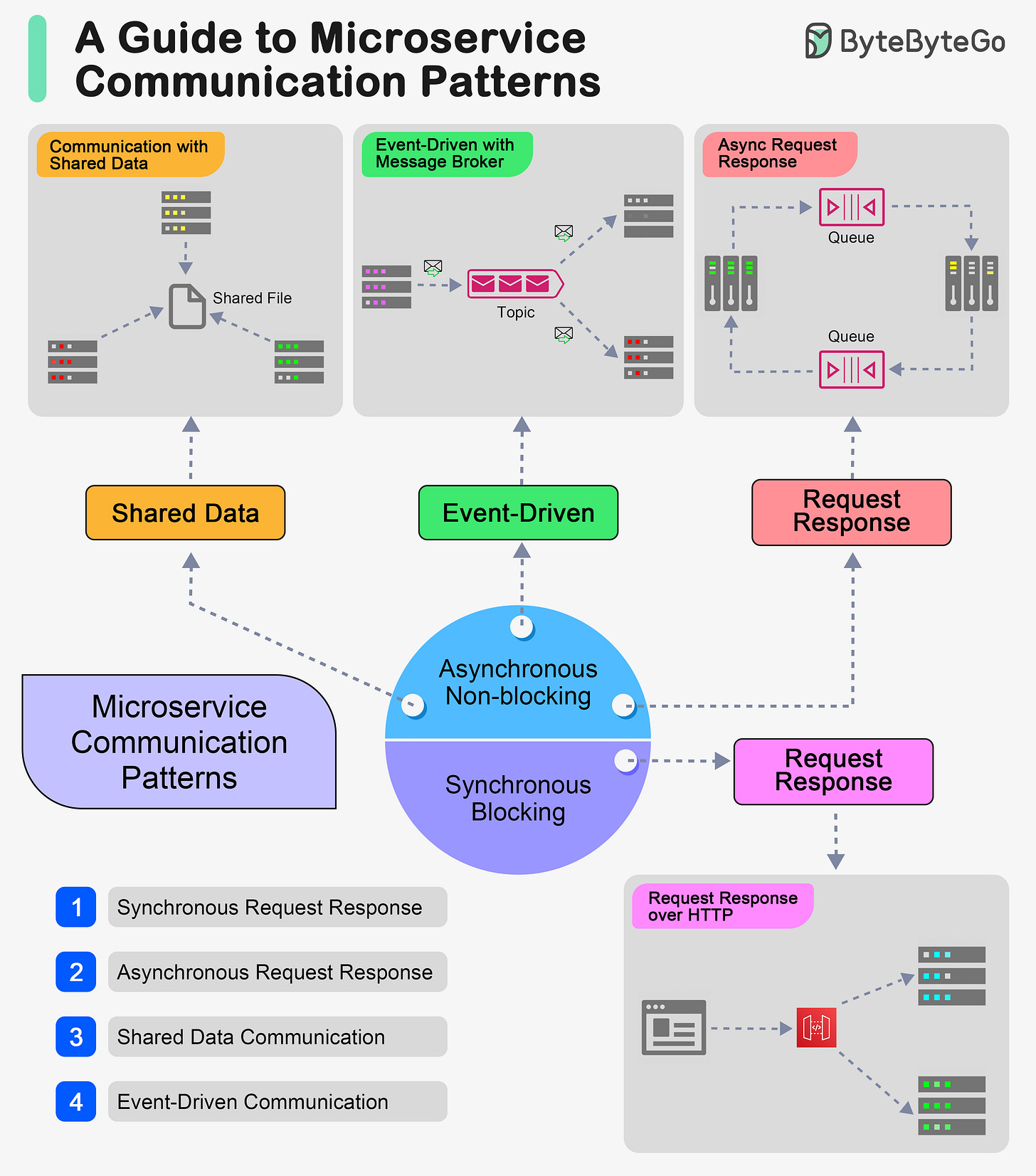
Kafka vs. RabbitMQ vs. Messaging Middleware vs. Pulsar
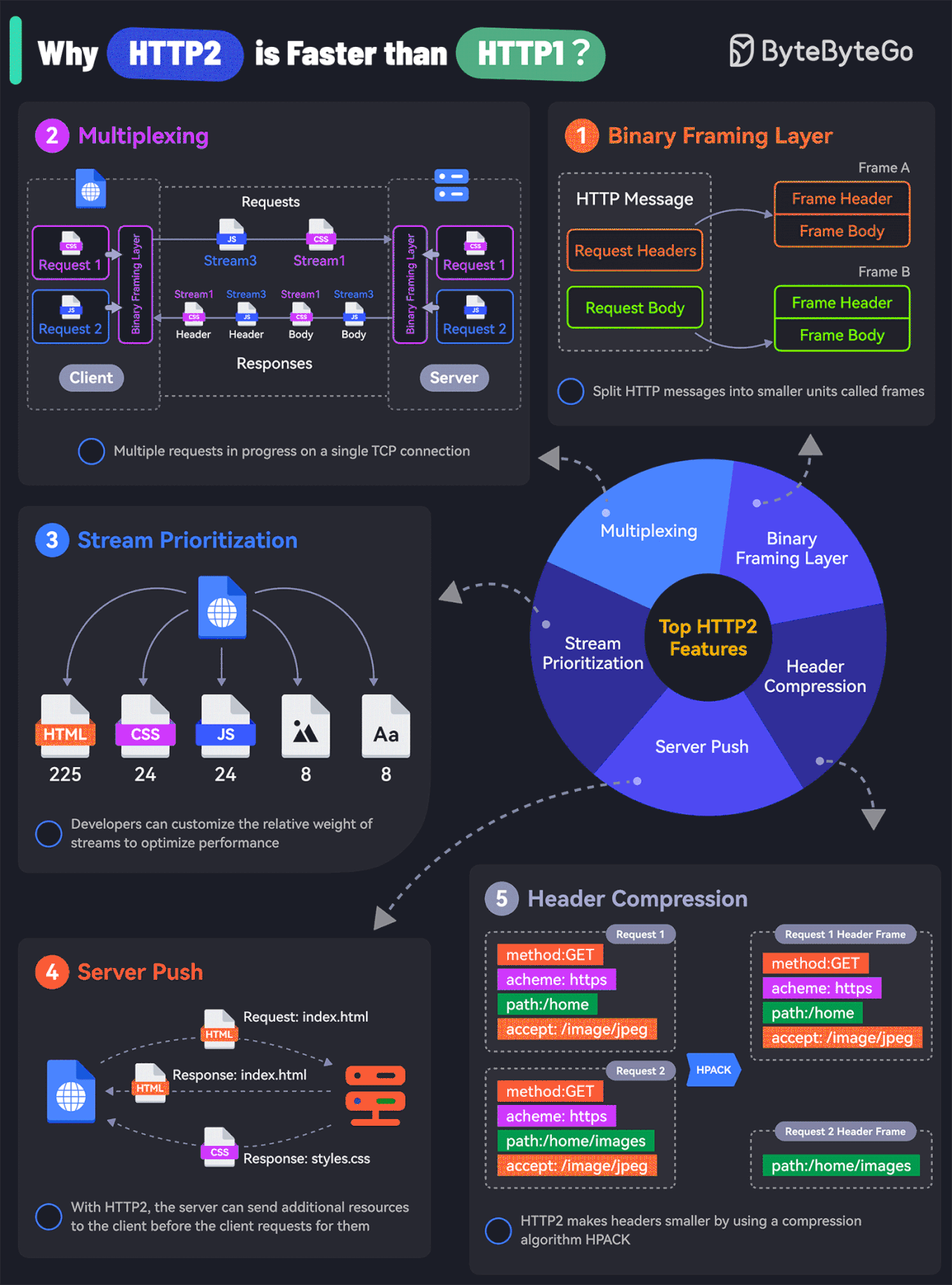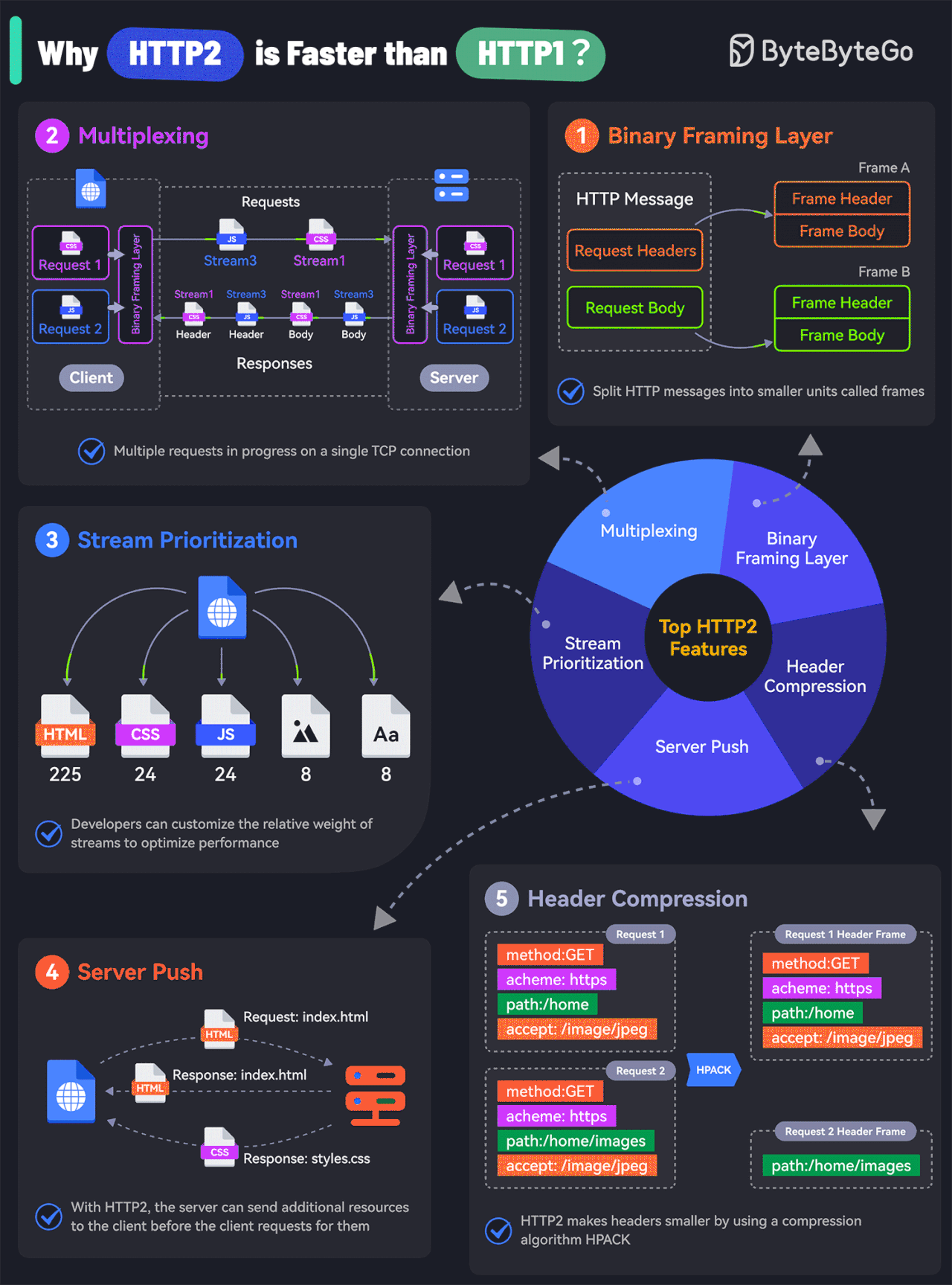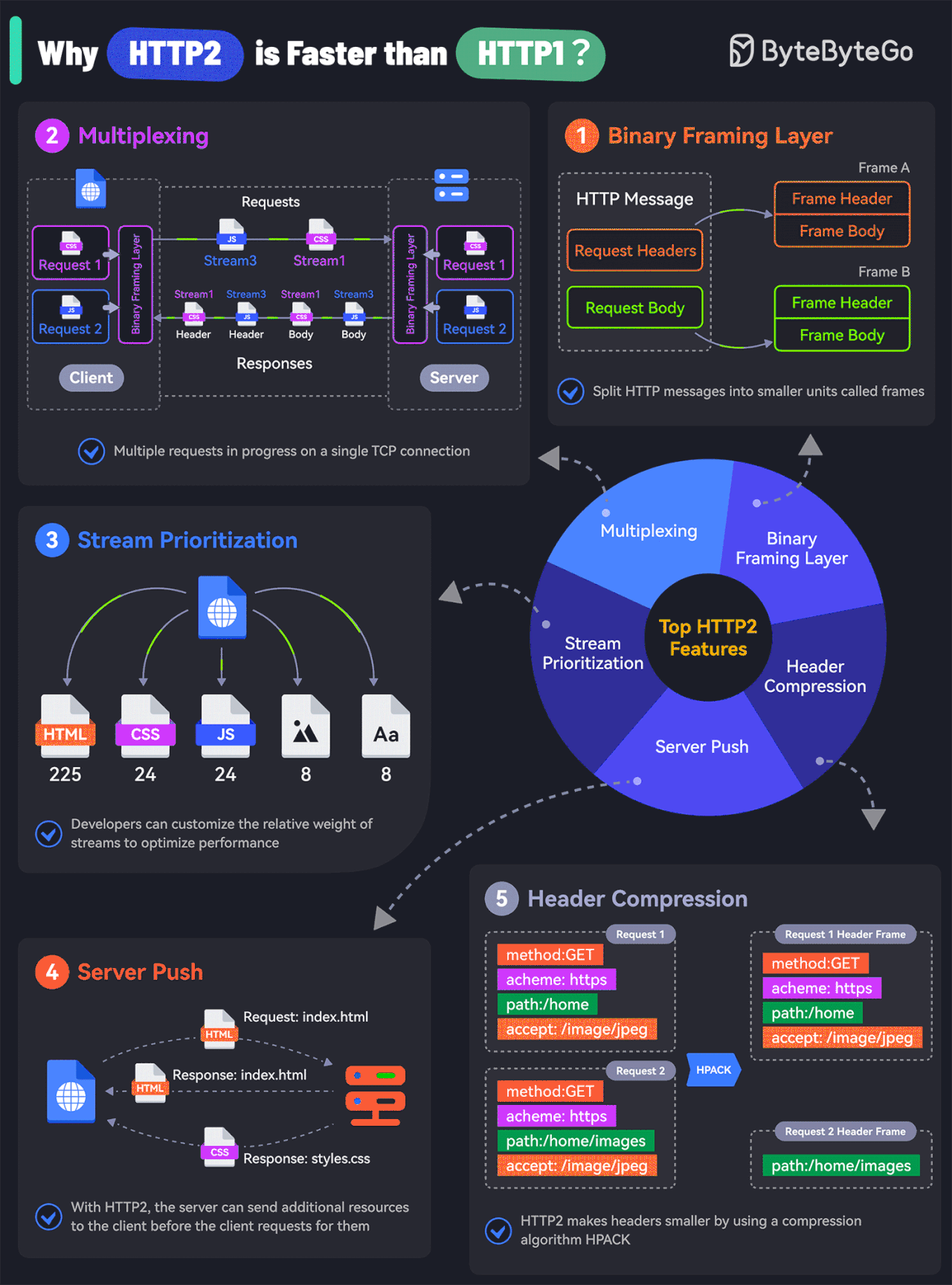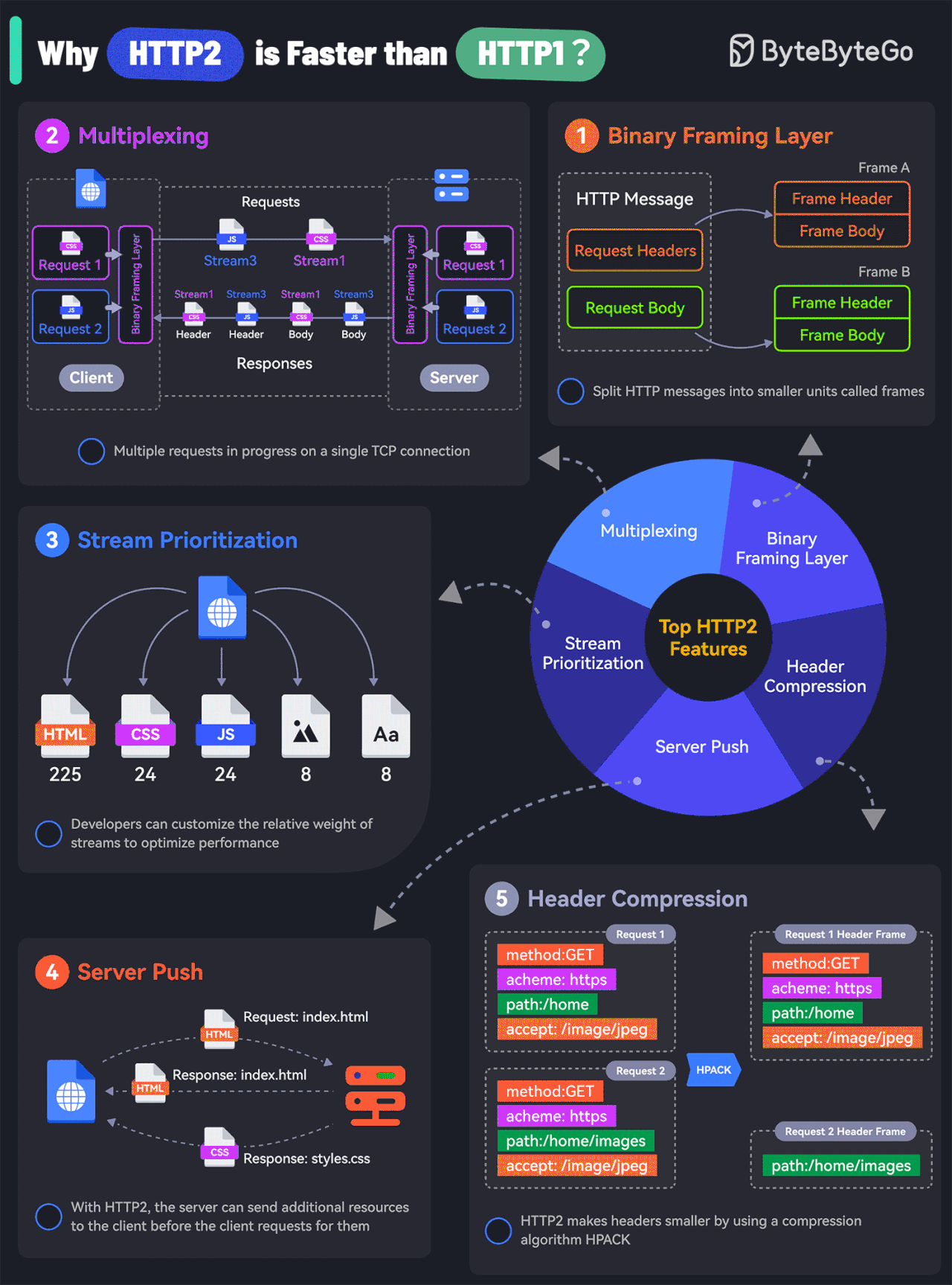
What makes HTTP2 faster than HTTP1?
The key features of HTTP2 play a big role in this. Let’s look at them:
Binary Framing Layer
HTTP2 encodes the messages into binary format.
This allows the messages into smaller units called frames, which are then sent over the TCP connection, resulting in more efficient processing.Multiplexing
The Binary Framing allows full request and response multiplexing.
Clients and servers can interleave frames during transmissions and reassemble them on the other side.Stream Prioritization
With stream prioritization, developers can customize the relative weight of requests or streams to make the server send more frames for higher-priority requests.Server Push
Since HTTP2 allows multiple concurrent responses to a client’s request, a server can send additional resources along with the requested page to the client.HPACK Header Compression
HTTP2 uses a special compression algorithm called HPACK to make the headers smaller for multiple requests, thereby saving bandwidth.
Of course, despite these features, HTTP2 can also be slow depending on the exact technical scenario. Therefore, developers need to test and optimize things to maximize the benefits of HTTP2.
Over to you: Have you used HTTP2 in your application?
Latest articles
If you’re not a paid subscriber, here’s what you missed.
To receive all the full articles and support ByteByteGo, consider subscribing:
Top 6 Cases to Apply Idempotency
Idempotency is essential in various scenarios, particularly where operations might be retried or executed multiple times. Here are the top 6 use cases where idempotency is crucial:
RESTful API Requests
We need to ensure that retrying an API request does not lead to multiple executions of the same operation. Implement idempotent methods (like PUT and DELETE) to maintain consistent resource states.Payment Processing
We need to ensure that customers are not charged multiple times due to retries or network issues. Payment gateways often need to retry transactions; idempotency ensures only one charge is made.Order Management Systems
We need to ensure that submitting an order multiple times results in only one order being placed. We design a safe mechanism to prevent duplicate inventory deductions or updates.Database Operations
We need to ensure that reapplying a transaction does not change the database state beyond the initial application.User Account Management
We need to ensure that retrying a registration request does not create multiple user accounts. Also, we need to ensure that multiple password reset requests result in a single reset action.Distributed Systems and Messaging
We need to ensure that reprocessing messages from a queue does not result in duplicate processing. We Implement handlers that can process the same message multiple times without side effects.
4 Ways Netflix Uses Caching to Hold User Attention
The goal of Netflix is to keep you streaming for as long as possible. But a user’s typical attention span is just 90 seconds.
They use EVCache (a distributed key-value store) to reduce latency so that the users don’t lose interest.
However, EVCache has multiple use cases at Netflix.
Lookaside Cache
When the application needs some data, it first tries the EVCache client and if the data is not in the cache, it goes to the backend service and the Cassandra database to fetch the data.
The service also keeps the cache updated for future requests.Transient Data Store
Netflix uses EVCache to keep track of transient data such as playback session information.
One application service might start the session while the other may update the session followed by a session closure at the very end.Primary Store
Netflix runs large-scale pre-compute systems every night to compute a brand-new home page for every profile of every user based on watch history and recommendations.
All of that data is written into the EVCache cluster from where the online services read the data and build the homepage.High Volume Data
Netflix has data that has a high volume of access and also needs to be highly available. For example, UI strings and translations that are shown on the Netflix home page.
A separate process asynchronously computes and publishes the UI string to EVCache from where the application can read it with low latency and high availability.
Reference: "Caching at Netflix: The Hidden Microservice" by Scott Mansfield
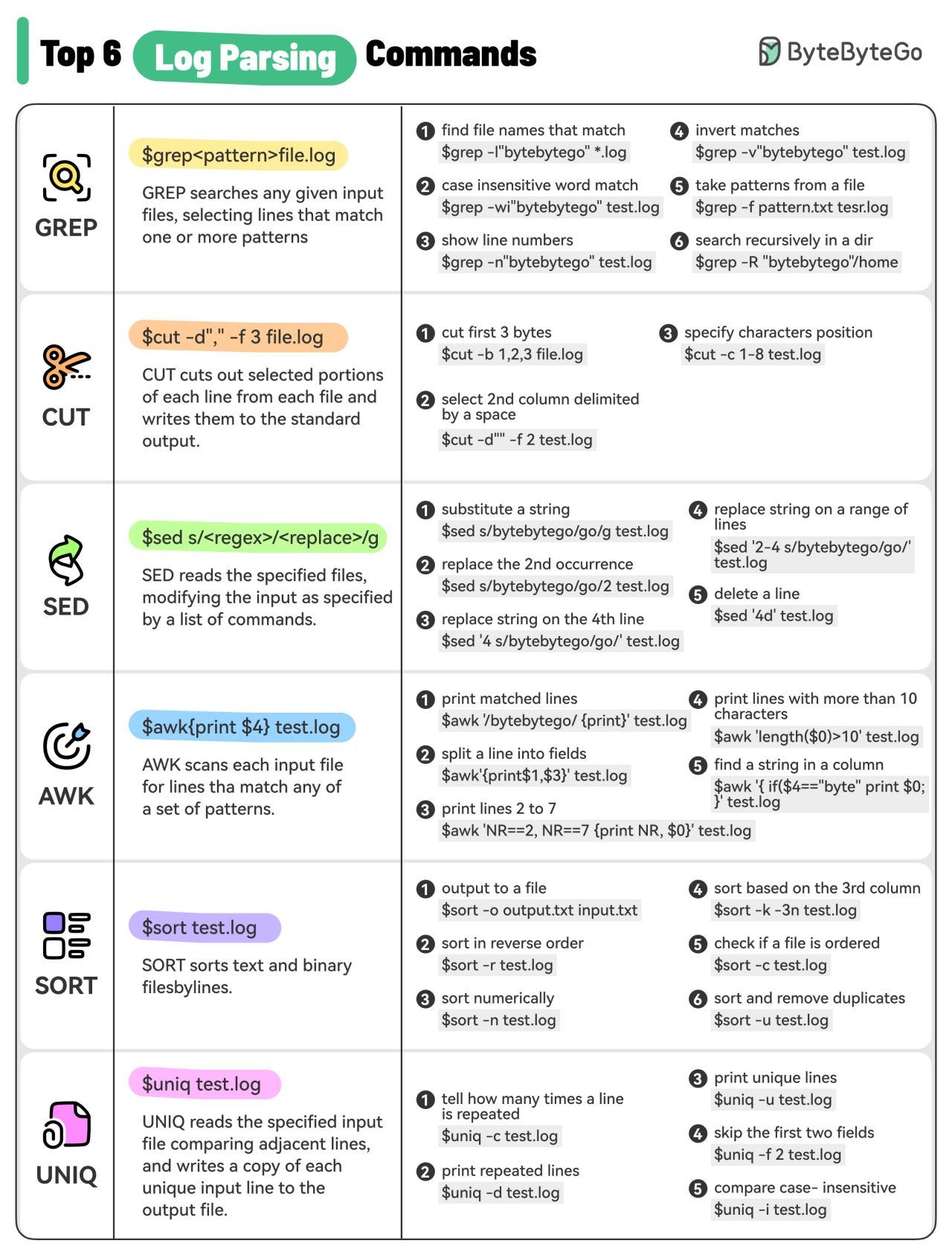
Log Parsing Cheat Sheet
The diagram below lists the top 6 log parsing commands.
GREP
GREP searches any given input files, selecting lines that match one or more patterns.CUT
CUT cuts out selected portions of each line from each file and writes them to the standard output.SED
SED reads the specified files, modifying the input as specified by a list of commands.AWK
AWK scans each input file for lines that match any of a set of patterns.SORT
SORT sorts text and binary files by lines.UNIQ
UNIQ reads the specified input file comparing adjacent lines and writes a copy of each unique input line to the output file.
These commands are often used in combination to quickly find useful information from the log files. For example, the below commands list the timestamps (column 2) when there is an exception happening for xxService.
grep “xxService” service.log | grep “Exception” | cut -d” “ -f 2
Over to you: What other commands do you use when you parse logs?
SPONSOR US
Get your product in front of more than 500,000 tech professionals.
Our newsletter puts your products and services directly in front of an audience that matters - hundreds of thousands of engineering leaders and senior engineers - who have influence over significant tech decisions and big purchases.
Space Fills Up Fast - Reserve Today
Ad spots typically sell out about 4 weeks in advance. To ensure your ad reaches this influential audience, reserve your space now by emailing hi@bytebytego.com